Data Strategy Nexus - "Where Data Strategy Meets Business Growth" with Marita Huaman Peralta
Executive Summary
This webinar highlights key areas of focus for enhancing business growth and sustainability in B-to-B companies. Marita Huaman addresses the challenges of integrating financial objectives with Environmental, Social, and Governance (ESG) taxonomies while emphasising the importance of improving financial reporting and Data Management, particularly in cooperative organisations. Additionally, the implementation of IoT systems is noted for enabling real-time resource control and enhancing operational efficiency.
The second portion of the webinar explores employee retention strategies and the intricacies of change management in project execution. Vanessa Tarazona explores the pressing issue of credit card fraud, discussing its various types, the ecosystem of fraud within the banking industry, and the crucial need for robust information security measures. She finishes the webinar by offering an approach to fraud reduction through data architecture and risk profiling, which is essential to protect personal information and bolster the financial ecosystem.
Webinar Details:
Title: Data Strategy Nexus - "Where Data Strategy Meets Business Growth" with Marita Huaman Peralta
Date: 19/03/2025
Presenter: Marita Huaman & Vanessa Tarazona
Meetup Group: DAMA SA User Group Meeting
Write-up Author: Howard Diesel
Contents
Data Strategy and Business Growth
Challenges and Considerations in Sustainability Management in B-to-B Companies
Financial Objectives, ESG Taxonomies, and Social Objectives in Business
Improving Financial Reporting and Data Management in Cooperative Organisations
Environmental Measures and Data Analysis
Implementation of IoT System for Real-Time Control of Various Resources
Disrupting Technology for Improved Operational Efficiency
Improvement of Manual to Automatic Process in Business
Implementing Internet of Things in Nuclear Power
Employee Retention and Challenges in the Workplace
Change Management in Project Management
Strategies in Employee Retention and Change Management
Challenges and Impact of Credit Card Fraud
Fraud Reduction and Data Architecture Implementation in the Credit Card Industry
Different Types of Credit Card Fraud
Implementing Fraud Prevention Measures
Risk Profiling and Data Lake Architecture in Financial Services
Understanding the Fraud Ecosystem in the Banking Industry
The Impact of Fraud on the Financial Ecosystem
Information Security in Businesses
Data Security and Protecting Personal Information
Data Strategy and Business Growth
Howard Diesel opens the webinar and welcomes Marita Huaman, CEO of Ciclus Group, and Vanessa Tarazona, CEO of Novamind Consulting, who wish to share their insights on aligning data strategy with business growth. Marita starts her presentation on the importance of a strong data foundation and processes for sustainable growth, emphasising that effective strategies must balance economic growth, environmental protection, and social well-being for future generations. She encourages fostering a sense of community, with acknowledgment of the diverse attendees and their shared commitment to data-driven decision-making.
Figure 1 Opening Slide
Figure 2 Marita Huaman & Vanessa Tarazona
Figure 3 Sustainability
Challenges and Considerations in Sustainability Management in B-to-B Companies
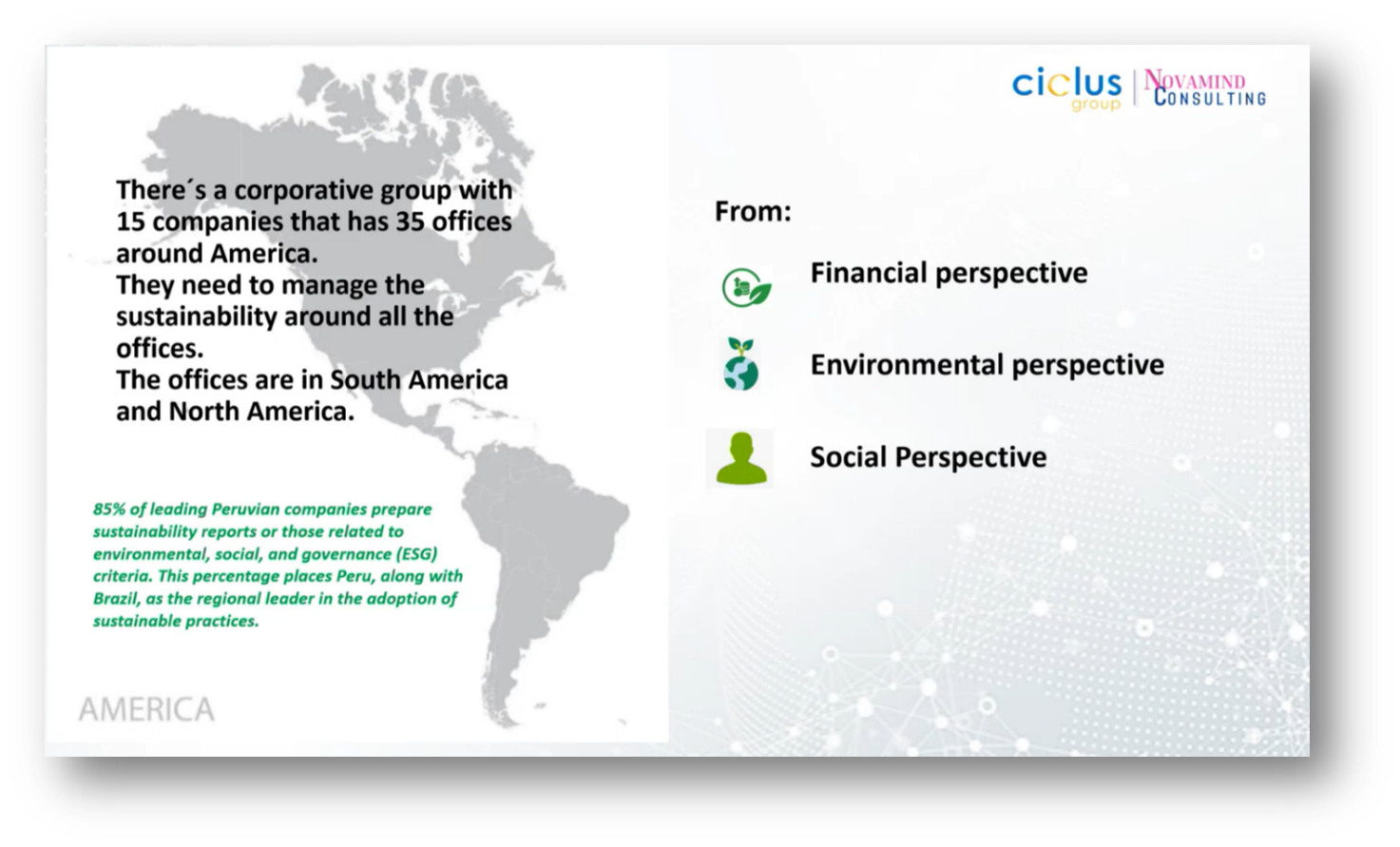
In Marita’s exploration of sustainability challenges within corporate groups, particularly in a Peruvian cooperative with 15 companies and 35 offices across South and North America, she has identified key issues in integrating sustainability into governance, strategy, and Data Management. The primary hurdles include the incorporation of sustainability objectives and effective monitoring of progress, often relying on inefficient tools like Excel for managing financial data, sustainability metrics, and employee growth. Additionally, there is a pressing need to govern data effectively to ensure proper information gathering and automation.
Figure 4 Sustainability Pt.2
Figure 5 "A Challenge of Corporative Groups"
Figure 6 Sustainability Project
Figure 7 Current Sustainability Challenges
Financial Objectives, ESG Taxonomies, and Social Objectives in Business
Marita highlights the challenges associated with integrating various ESG taxonomies in financial strategy, emphasising the need for careful alignment to address complexities. She references a project that tackled taxonomy issues by developing innovative solutions while also stressing the importance of financial objectives such as profit, revenue, operational efficiency, risk management, and sustainability goals like reducing environmental impact and energy waste.
Social objectives focus on equitable wages, diversity, inclusion, and employee retention, with the latter linked to profitability. The overall message underscores that a company's growth fosters job creation, benefiting both the organisation and the broader community.
Figure 8 Current Sustainability Challenges Pt.2
Figure 9 Sustainability Objectives
Improving Financial Reporting and Data Management in Cooperative Organizations
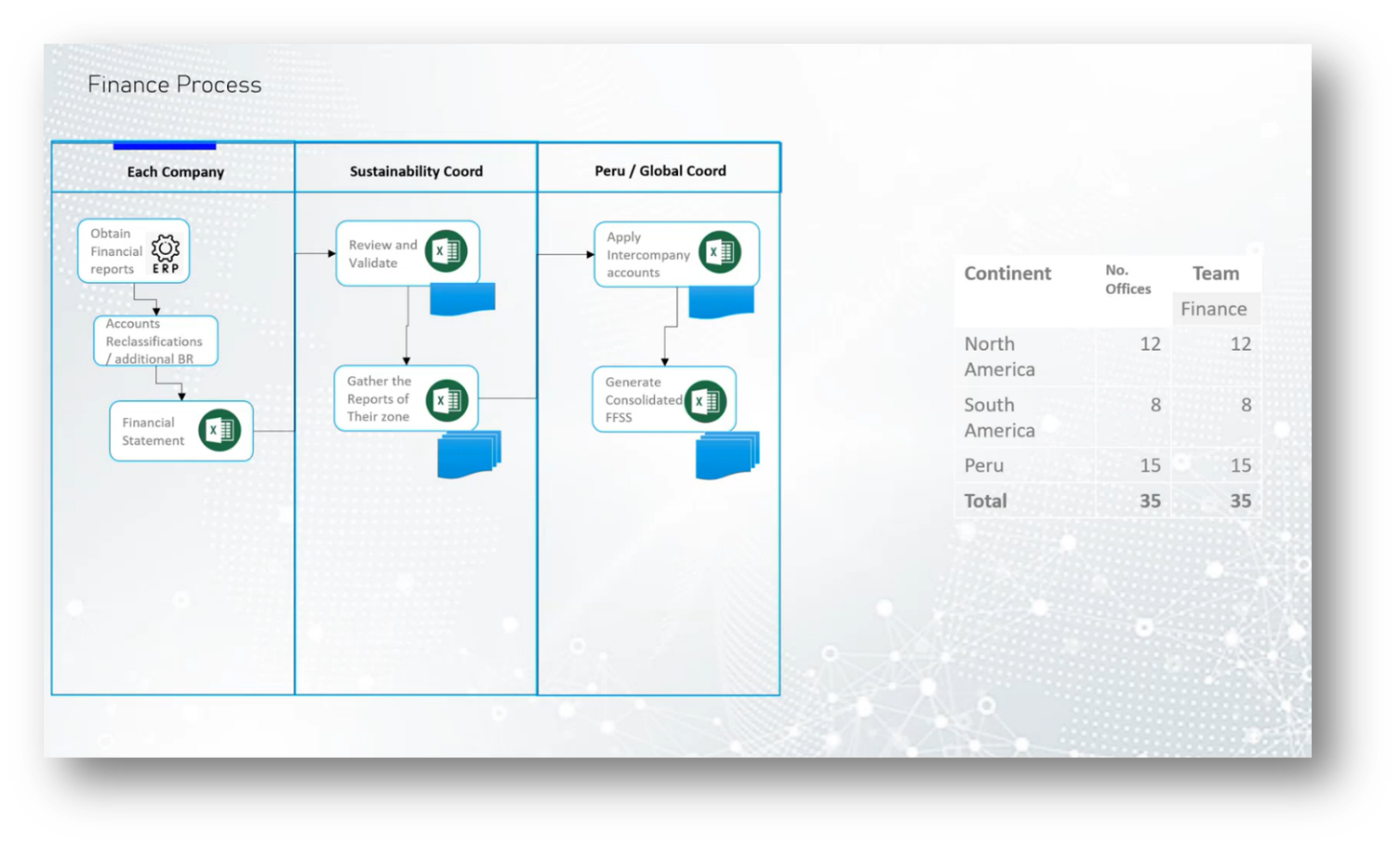
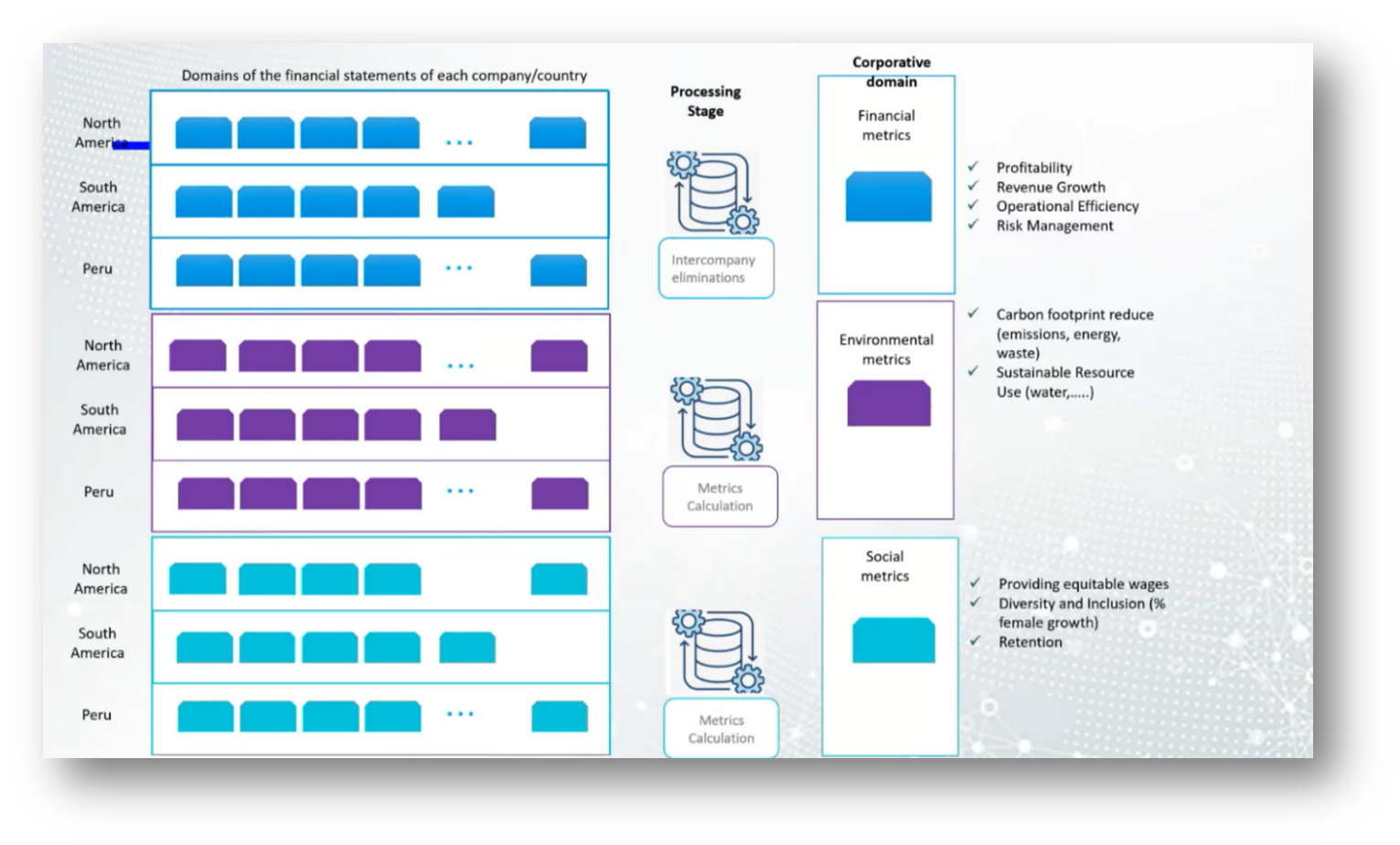
The cooperative group, consisting of 15 companies and 35 offices across America, faced challenges in generating financial reports due to the need for manual reclassifications and additional business rules that their ERP system could not accommodate, resulting in a reliance on Excel for financial statement preparation. A sustainability coordinator collected and validated data from each company, ultimately consolidating the financial statements by eliminating intercompany accounts.
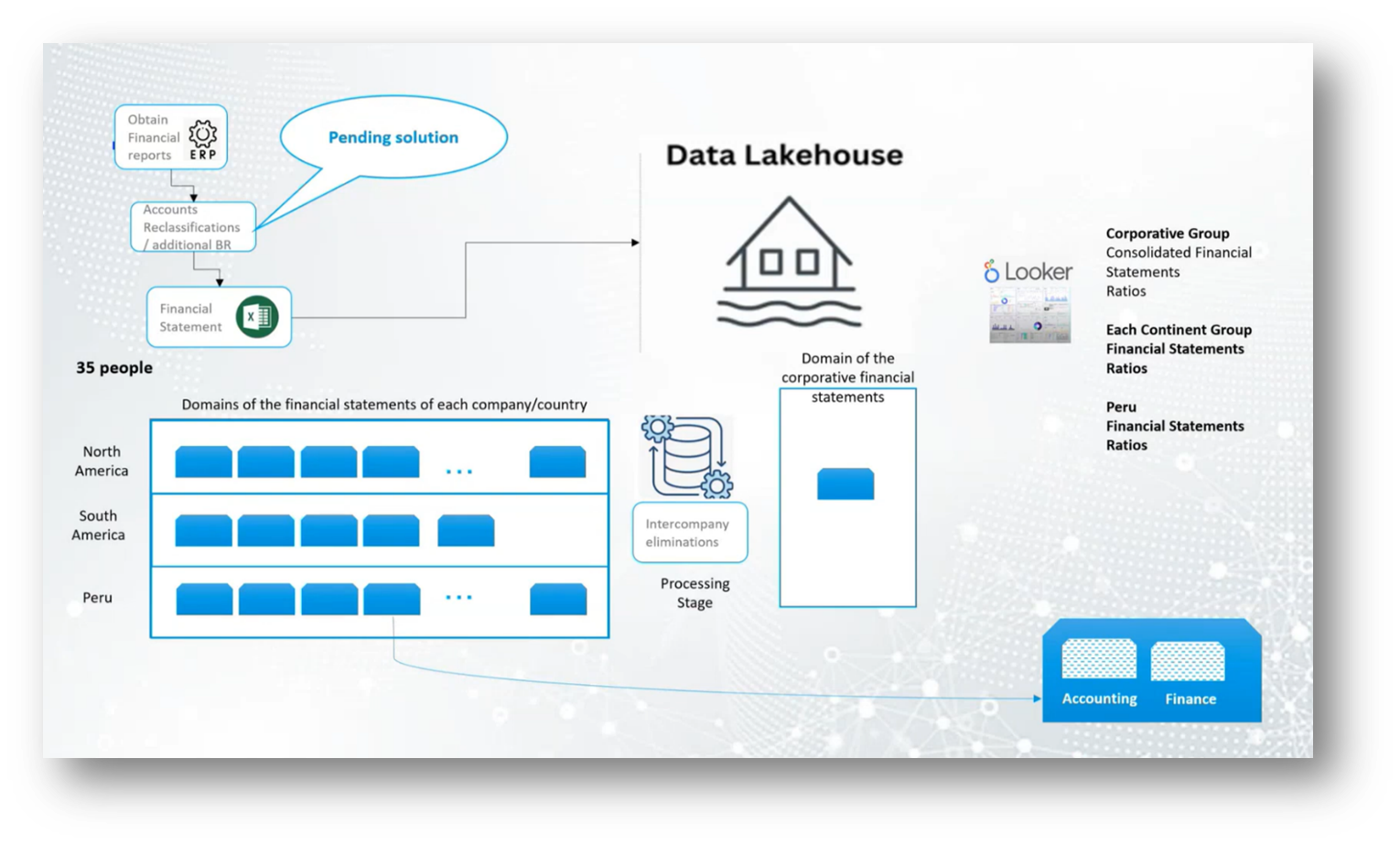
To streamline this process, a Data Lake House was designed, which organised financial data into specific domains by country, allowing for efficient processing and intercompany eliminations. This new system greatly reduced manual work, minimised the risk of errors, and improved the overall efficiency of generating corporate financial statements.
Figure 10 Finance Process
Figure 11 Data Lakehouse
Environmental Measures and Data Analysis
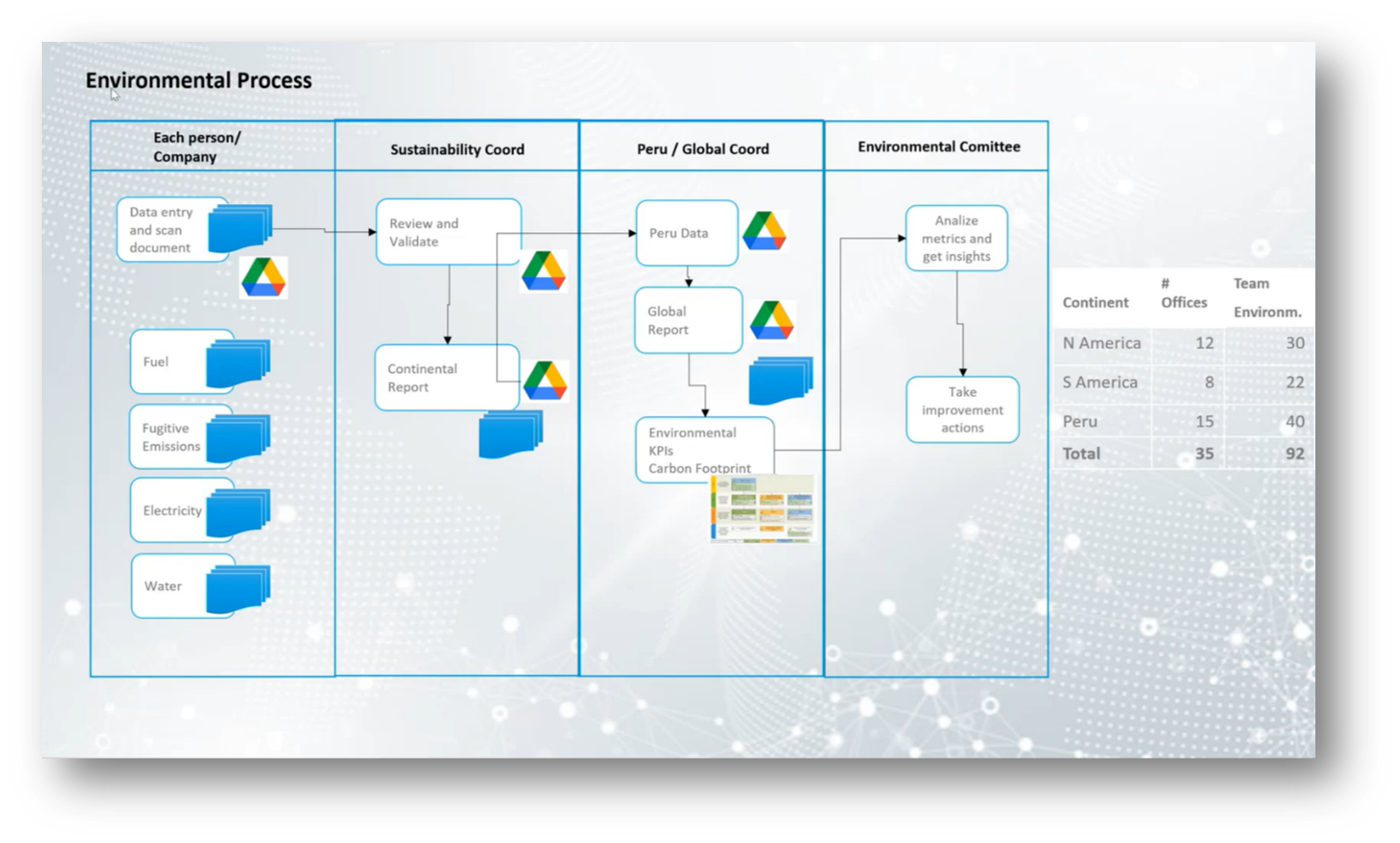
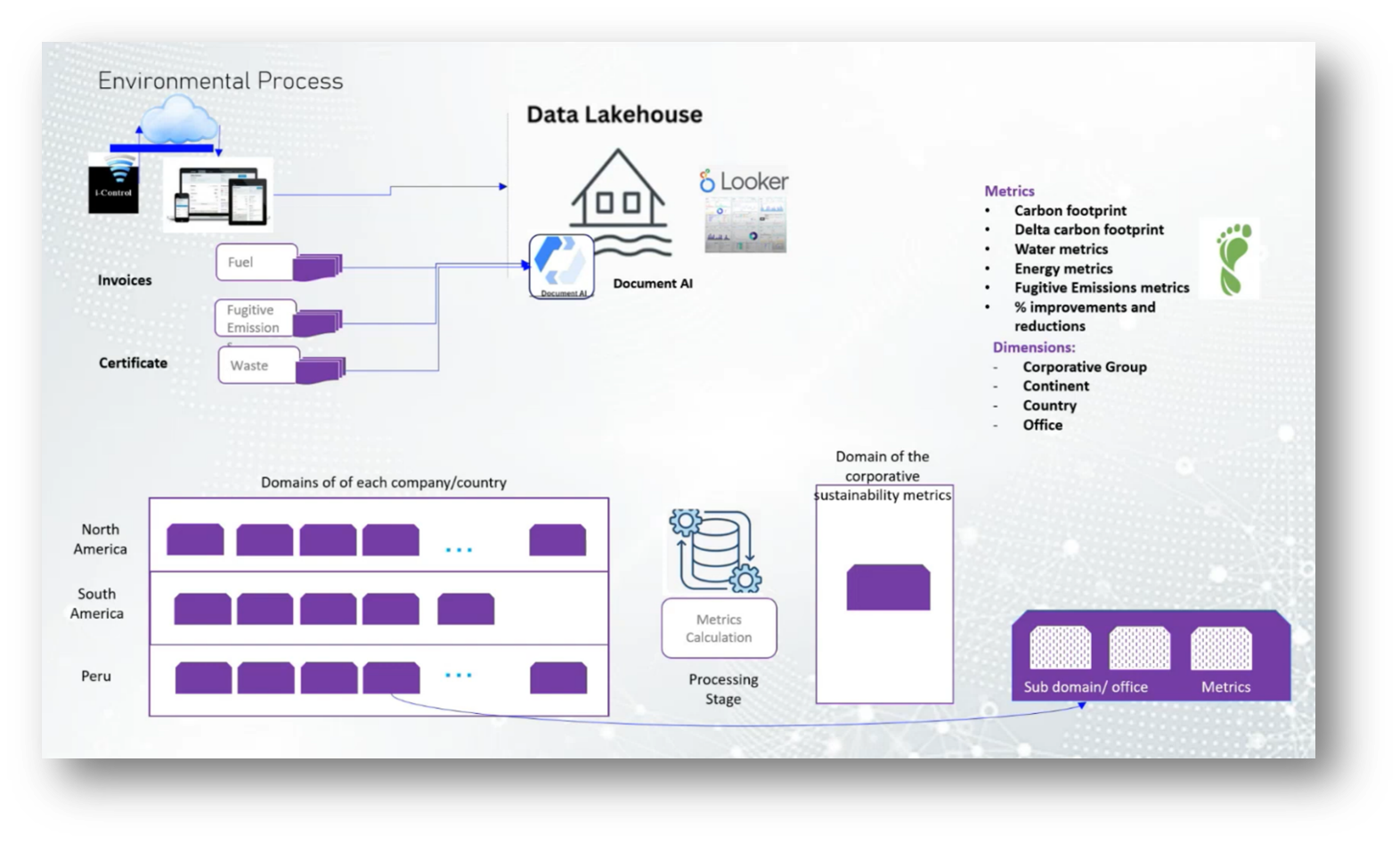
The recent environmental processes involve a collaborative effort using Google Drive to streamline data entry and document scanning among various companies. Each participant uploads invoices and certificates related to fuel consumption, fugitive emissions, and water usage, ensuring that all necessary measurements and documentation are submitted for validation by a coordinator.
This information is then compiled into a continental report, which is sent to Peru for inclusion in a global report. Despite past challenges with late information and a lack of awareness regarding environmental metrics, the environmental committee has improved data analysis and insights, leading to actionable improvement steps within cooperative groups, particularly those involved with the Lima stock exchange.
Figure 12 Environmental Process
Implementation of IoT System for Real-Time Control of Various Resources
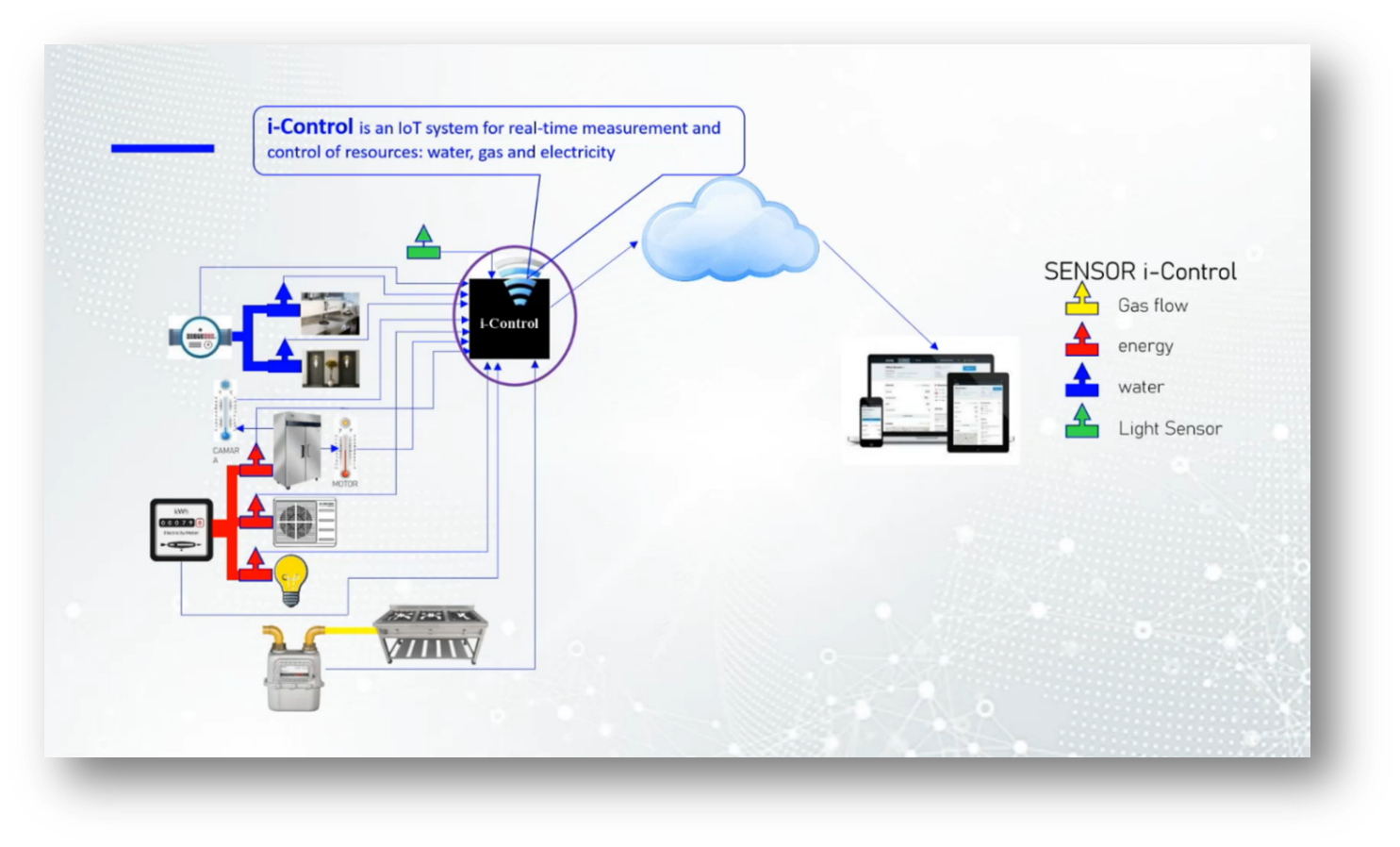
The iControl system is an innovative IoT solution designed for real-time monitoring and control of essential resources such as water, gas, and electricity. By integrating sensors with energy, gas, and water meters, it streamlines coordination by reducing the number of personnel needed for management. Additionally, the iControl sensors upload data to the cloud, allowing users to access all relevant metrics on a single platform. This system not only manages the flow of gas, energy, and water but also provides real-time insights into consumption, enabling efficient resource management. The implementation of iControl is intended to replace existing systems outlined in further documentation.
Disrupting Technology for Improved Operational Efficiency
The project Marita shares aims to enhance efficiency in monitoring resources like water, gas, and electricity by implementing two advanced technologies: an IoT system called iControl and GCP's Document AI. The iControl system utilises real-time measurements from energy, gas, and water meters, allowing for more accurate data than traditional invoices. Simultaneously, Document AI employs OCR technology to convert unstructured data from invoices into structured data, facilitating seamless integration into a Data Lake.
By combining these technologies, the process of measuring and reporting resource usage will be streamlined, reducing the need for human intervention and improving the accuracy of carbon footprint metrics across various domains, including cooperative groups, countries, and offices. Ultimately, this organised approach not only saves time but also enhances sustainability efforts through better-informed decisions.
Figure 13 i-Control
Figure 14 i-Control Pt.2
Figure 15 Environmental Process Pt.2
Improvement of Manual to Automatic Process in Business
The transition from manual processes to a more automated system significantly impacted efficiency and quality in document handling. Initially, the manual approach involved approximately 30 staff members, with an additional 60 responsible for managing invoices and certificates related to fuel and fugitive emissions. Coordinators were assigned to validate the outputs from optical character recognition (OCR), ensuring that the process was not solely automated but included human oversight for accuracy. Overall, this shift has proven to be a productive investment, enhancing operational effectiveness.
Figure 16 Social Perspective
Implementing the Internet of Things in Nuclear Power
The challenges and considerations involved in managing calibration standards across different countries within the context of the Internet of Things (IoT) in nuclear power is discussed. Marita emphasises the collaborative efforts required from various departments, such as operations and service management, to ensure proper calibration and data accuracy. While IoT has led to a reduction in administrative roles, it also necessitates a standardisation of instrumentation and enhanced management due to increased data complexity.
Marita suggests utilising AI to monitor instrument calibration within defined intervals as a supportive measure rather than a complete solution. Ultimately, she stresses the importance of engaging and upskilling staff in sustainability practices while adapting to new technologies for continuous improvement.
Employee Retention and Challenges in the Workplace
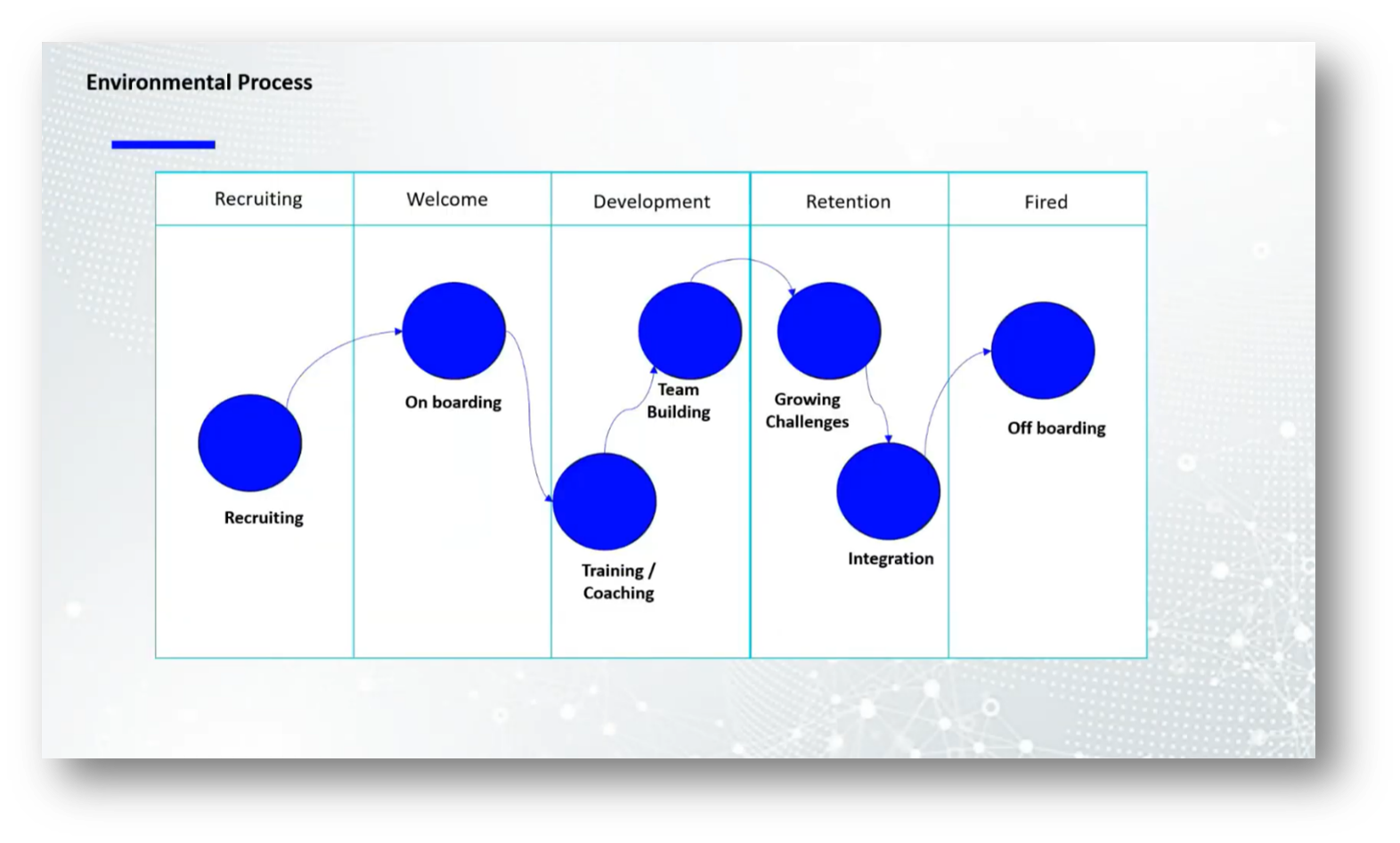
The life cycle of an employee encompasses several key stages: recruiting, onboarding, development, retention, and separation. Understanding the social perspective is crucial, as retention involves more than just a positive work climate or motivation. Current trends indicate that millennials and younger employees are particularly focused on how companies challenge them and support their growth. Organisations must continually adapt to provide for these ongoing challenges to retain talent effectively.
Figure 17 Environmental Process Pt.2
Change Management in Project Management
Change management is a critical component of successful project implementation, as highlighted in a recent discussion. It’s essential to involve the right stakeholders from the outset, allowing them to feel ownership and contribute to defining solutions. When key individuals are excluded due to time constraints or oversight, it can lead to resistance and conflict within the project. Therefore, effective change management should begin early, ensuring that all relevant parties are engaged throughout the process to foster a positive culture and smooth transition.
Figure 18 Data Lakehouse Pt.3
Strategies in Employee Retention and Change Management
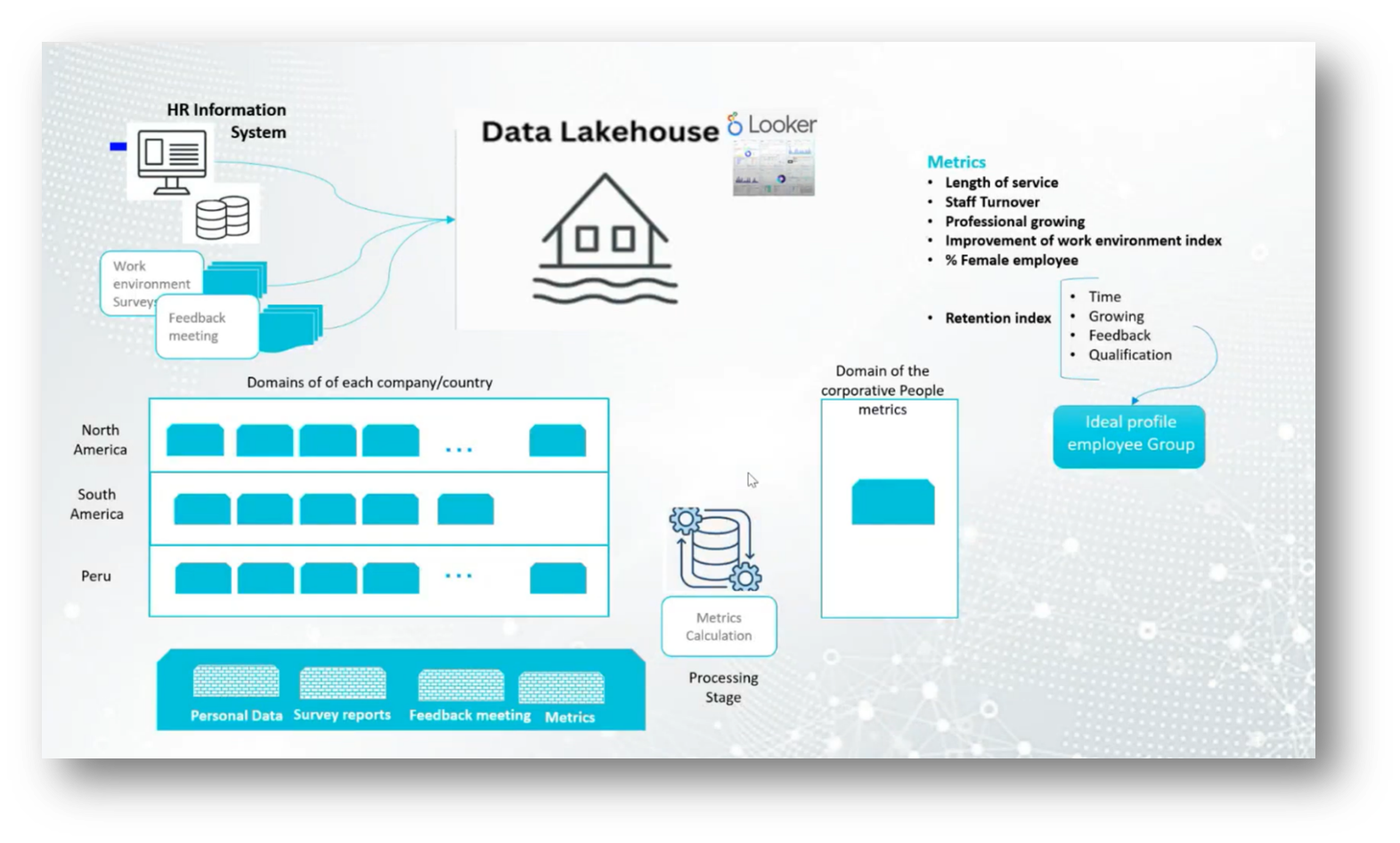
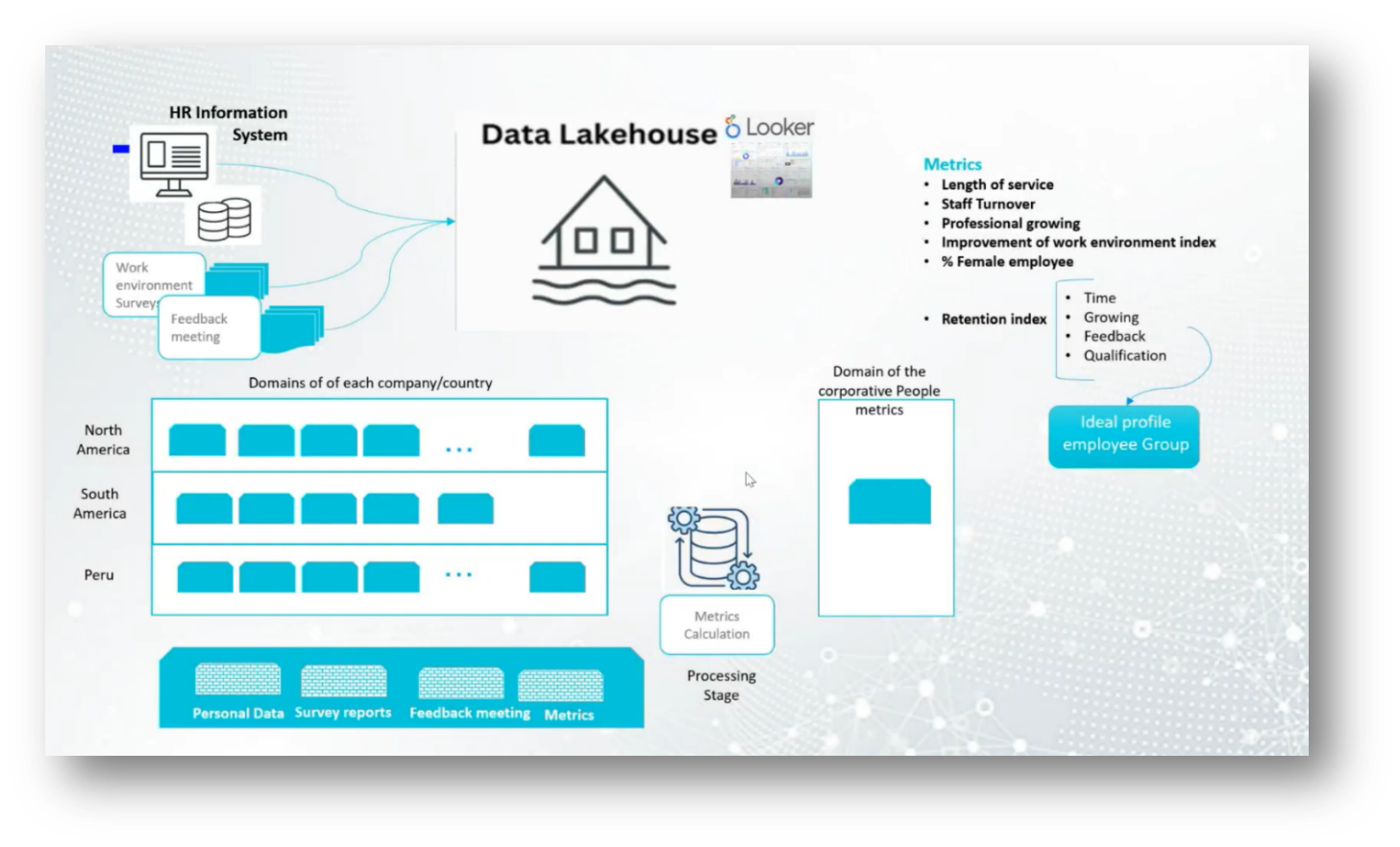
The current challenges in employee retention hinge on analysing various data sources, including human resources information systems, work environment surveys, and feedback from managers. This data is consolidated in a lake house, which allows for in-depth metrics on employee performance, turnover, professional growth, and the overall work environment. Key metrics include employee tenure, turnover rates, and a specialised retention index that incorporates professional development and feedback quality.
The objective is to align employee profiles with corporate growth needs, necessitating a shift in business processes as new technologies, such as the Internet of Things, are integrated. This transformation requires change management strategies to ensure that all teams adapt accordingly, recognising the differences in data flow and measurement between traditional and new systems until a cohesive understanding is achieved.
Figure 19 Data Lakehouse Pt.4
Figure 20 Project Overview
Figure 21 Marita's Closing Slide
Challenges and Impact of Credit Card Fraud
The transition from an old system to a new one can be challenging, involving different timings and old timing issues that complicate the process. To navigate this, it's essential to simplify complex procedures and create a detailed transition plan, possibly starting with a Minimum Viable Product (MVP). Training employees who may lack the necessary skills is crucial for effective change management.
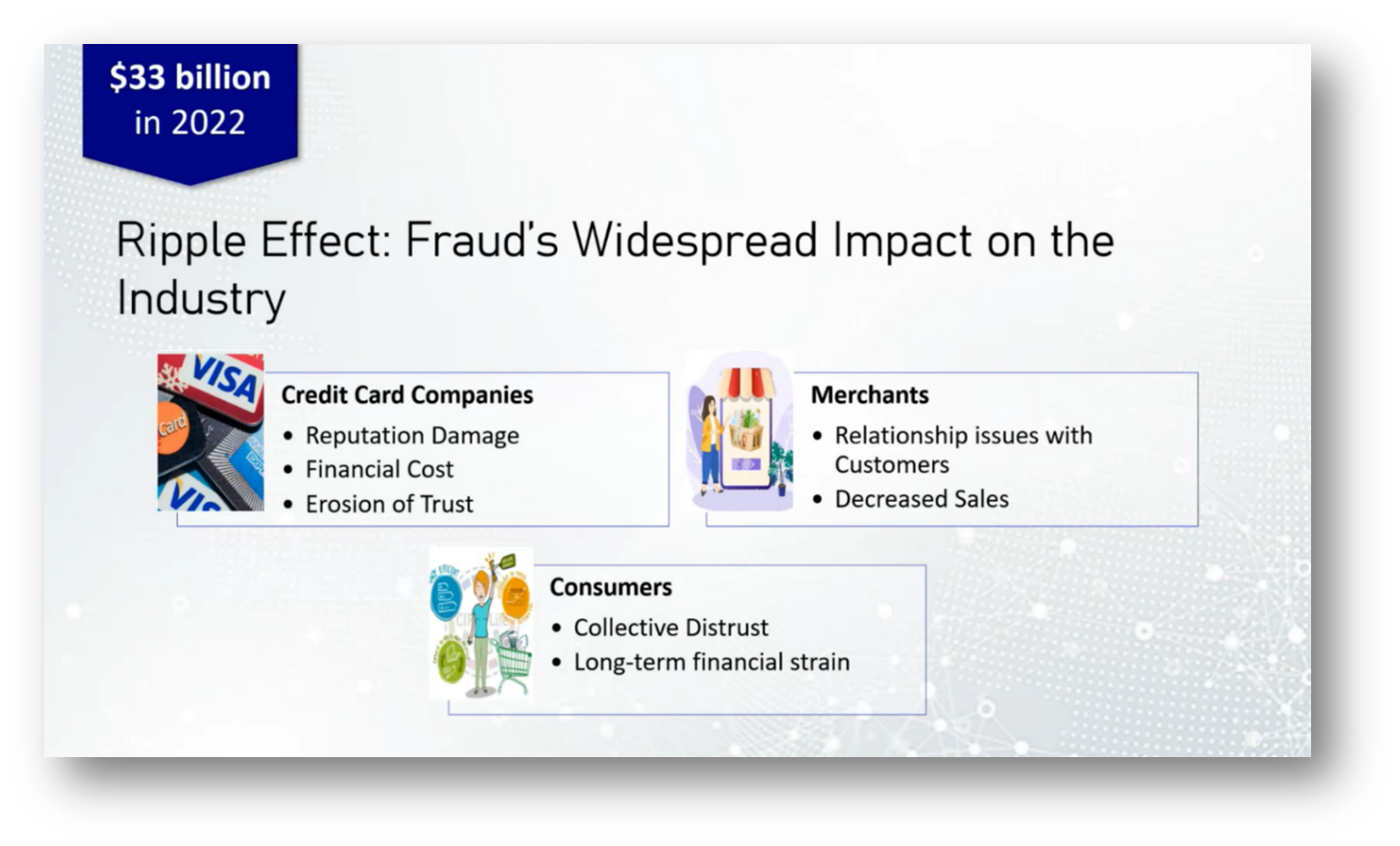
In a separate context, Vanessa also highlights the significant threat of credit card fraud, which resulted in global losses of $33 billion in 2022. This issue impacts not only financial losses but also the reputation of credit card companies, leading to decreased consumer trust as criminals increasingly leverage sophisticated methods, including Advanced Generative Intelligence (AGI), to exploit vulnerabilities.
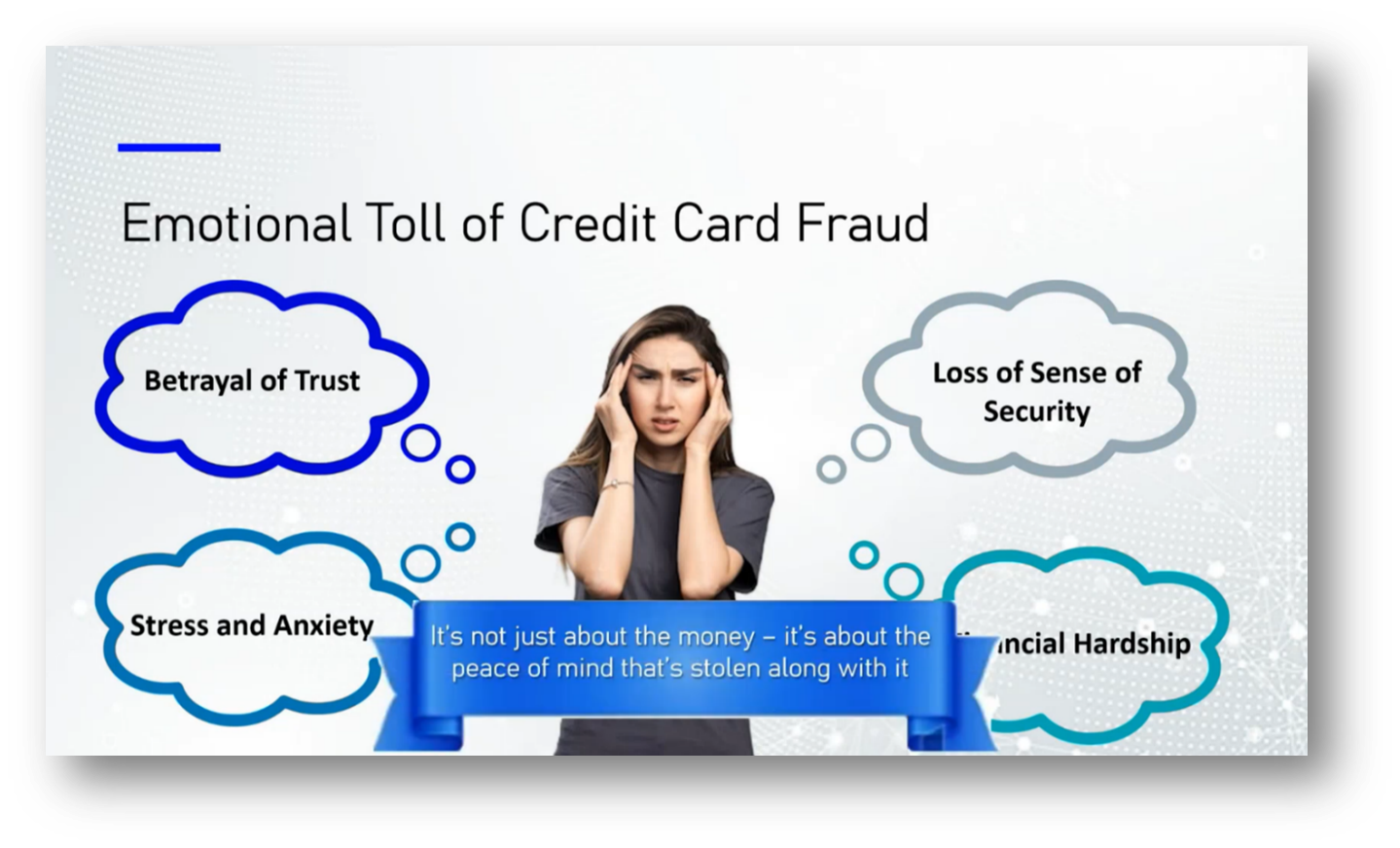
Fraud mitigation is essential for financial institutions to protect customers' money and maintain trust, especially in light of recurring cyber threats and data breaches that can lead to significant negative publicity. Merchants also face challenges as customer trust erodes when fraudulent activities occur after transactions, leading to decreased sales. Beyond financial losses, victims of credit card fraud experience deep emotional distress, as the betrayal of trust disrupts their sense of security in the financial system.
While some banks, particularly in North America, may cover fraudulent charges during investigation periods, in regions like South America, customers often face the burden of payments during resolution, adding to their financial strain. Ultimately, the impact of fraud transcends monetary aspects, highlighting the critical need for peace of mind among customers.
Figure 22 "Credit Card Fraud: More than the Financial Impact"
Figure 23 Ripple Effect
Figure 24 Ripple Effect Pt.2
Figure 25 Emotional Toll of Credit Card Fraud
Fraud Reduction and Data Architecture Implementation in the Credit Card Industry
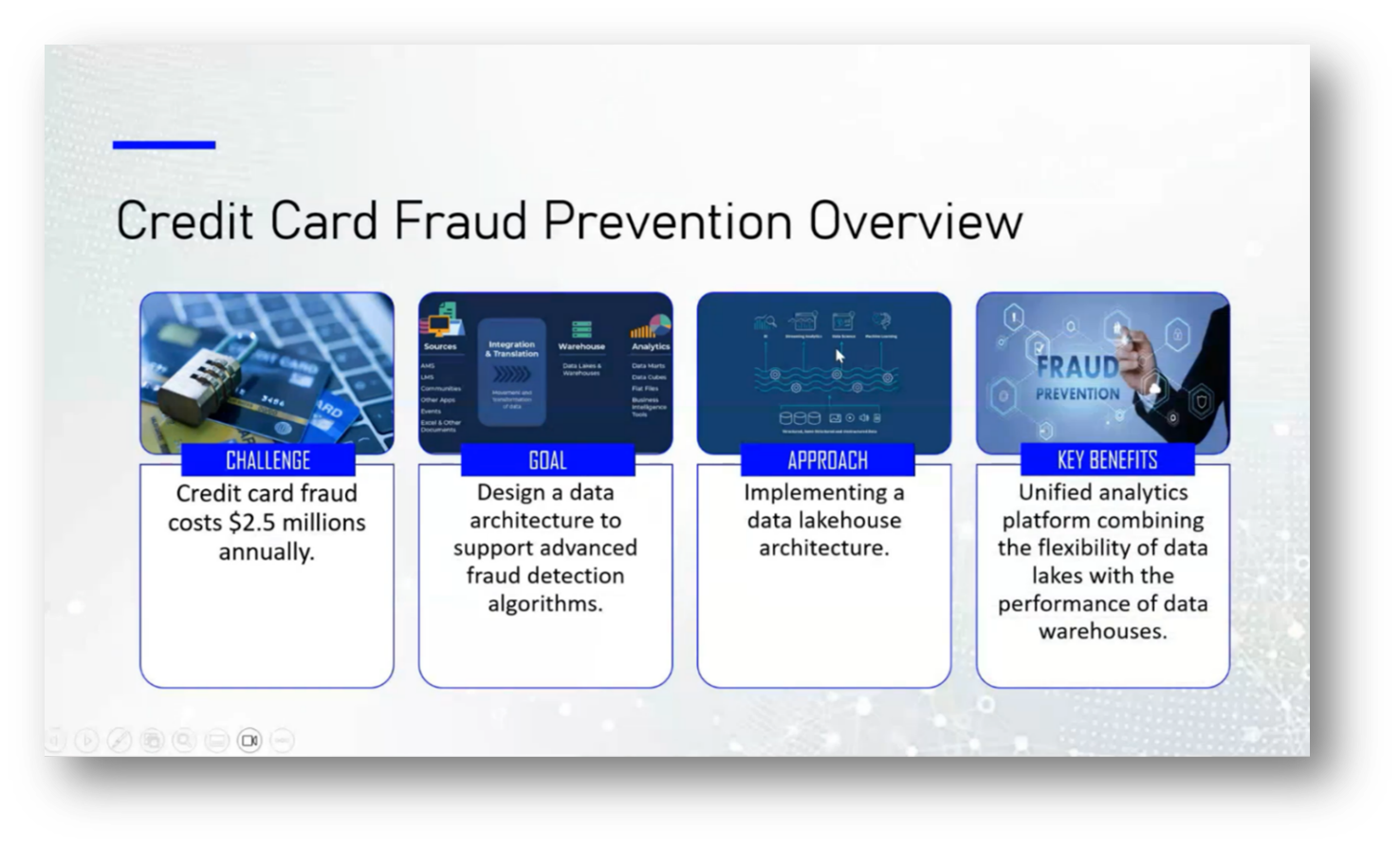
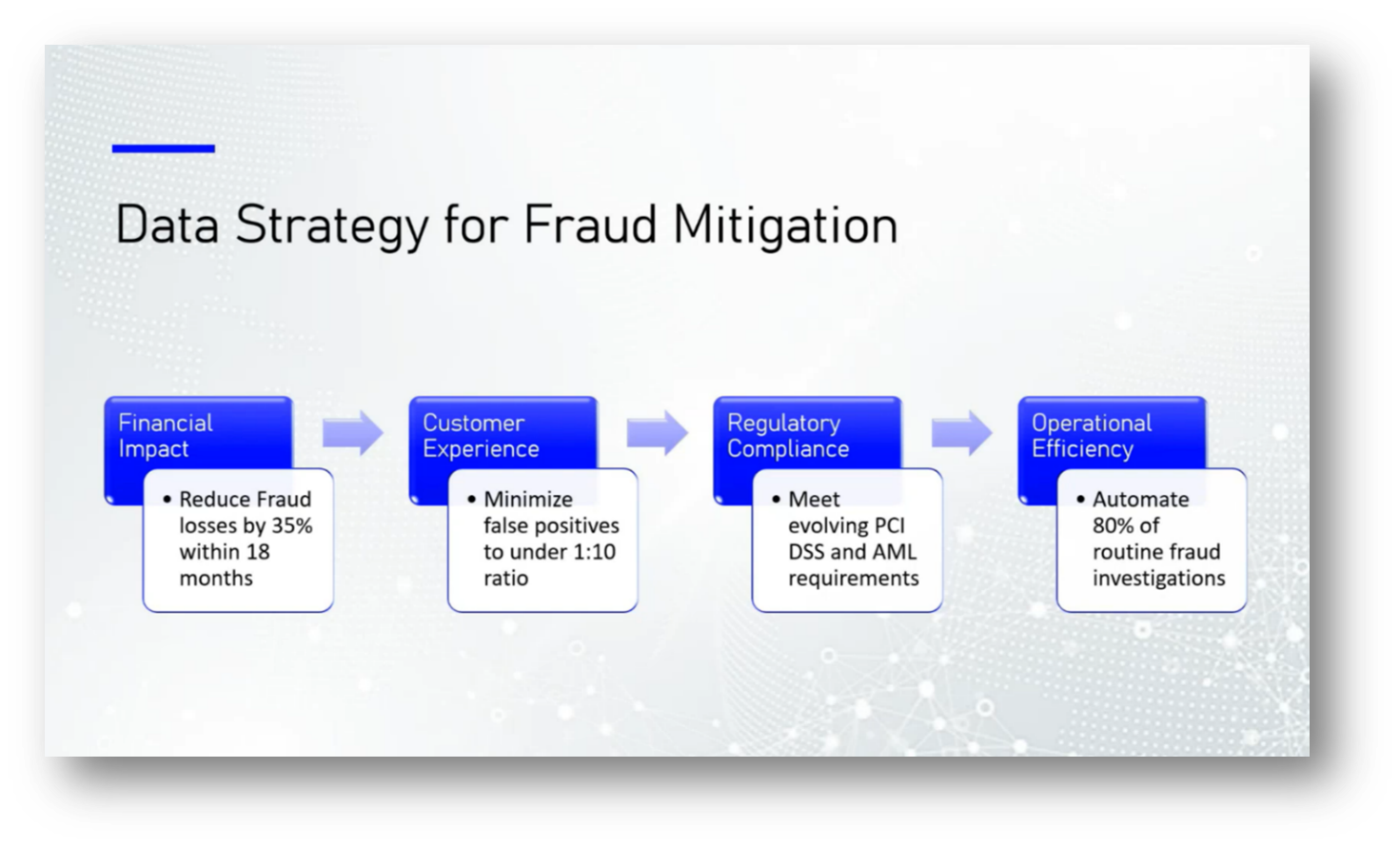
The company faced an annual credit card fraud cost of $2.5 million, prompting the need for a more responsive data architecture to support advanced fraud detection algorithms. The existing data infrastructure was inadequate for the evolving market demands, leading to the implementation of a Data Lake House architecture. This solution combined the flexibility of a Data Lake with the performance of a data warehouse, aiming to reduce fraud by 35% within 18 months, minimise false positives by a ratio of 10 to 1, and ensure compliance with PCI credit card and money laundering regulations. Additionally, the algorithms were designed to optimise the review process for routine fraud investigations, enhancing overall operational efficiency.
Figure 26 Emotional Toll Pt.2
Figure 27 Credit Card Fraud Prevention Overview
Figure 28 Data Strategy for Fraud Mitigation
Figure 29 Types of Credit Card Fraud
Different Types of Credit Card Fraud
Credit card fraud can take several forms, including theft of physical cards, where stolen or lost cards are used for unauthorised purchases. Another method involves criminals obtaining key information such as the card number, expiration date, and CVV for online transactions. Account takeover fraud occurs when an individual assumes control of someone's account through methods like identity theft or phishing, enabling them to request new credit cards sent to their address and change account details.
Application fraud entails impersonating someone to apply for credit in their name. Additionally, skimming devices can read data from magnetic stripes, which are more vulnerable than chip technology. Lastly, phishing schemes involve fraudsters soliciting personal information via phone calls or messages, often by posing as legitimate entities and prompting victims to provide sensitive details.
Figure 30 Types of Credit Card Fraud Pt.2
Implementing Fraud Prevention Measures
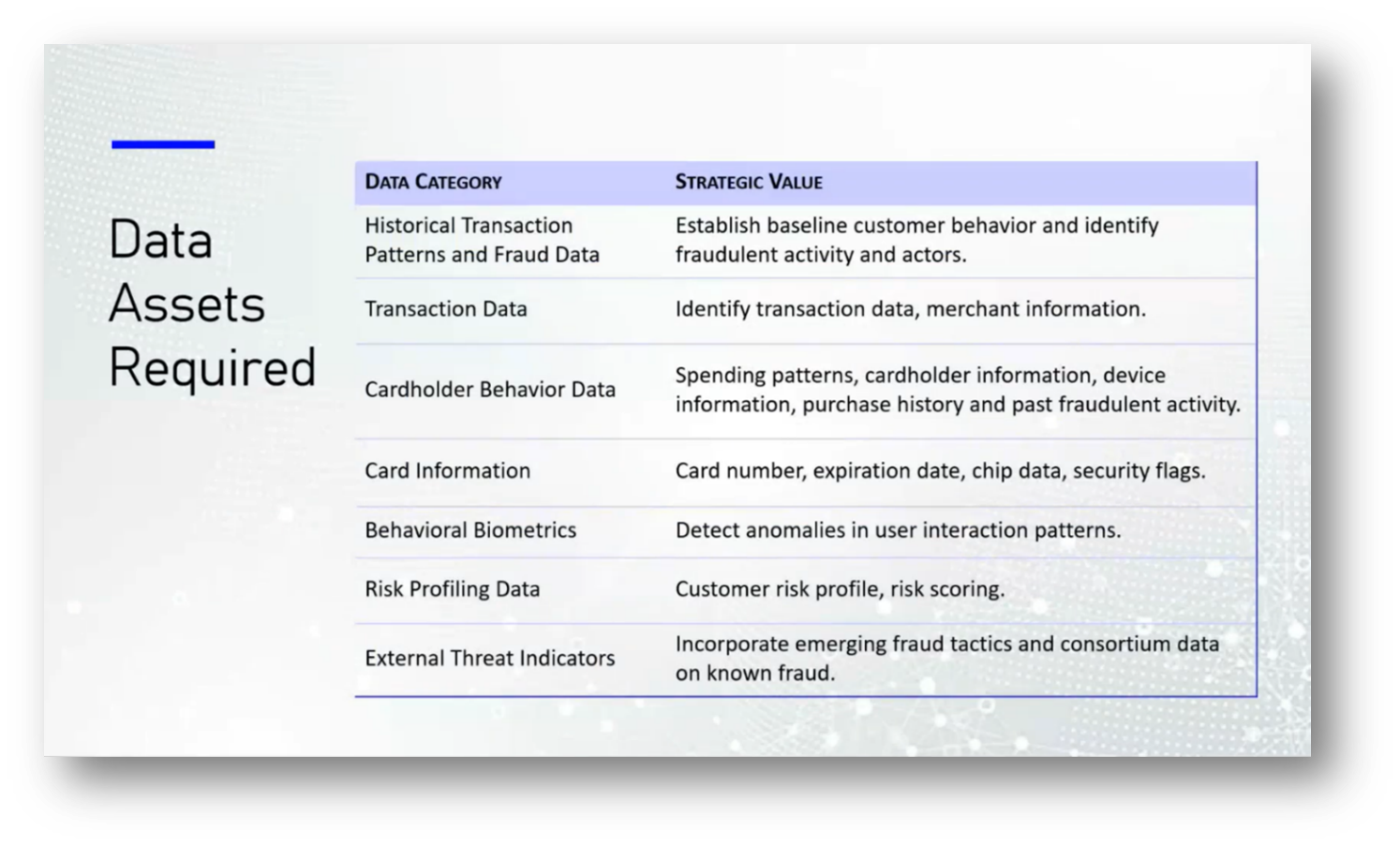
Understanding the types of fraud that can occur is essential for effective prevention. To take action, we need two primary categories of data: batteries for building machine learning models and transaction data, which includes merchant information to identify fraud perpetrators. Additionally, we must analyse customer behaviour data, such as spending patterns, device information, purchase history, and any previous fraudulent activity. Behavioural biometrics play a critical role in this process, as they capture data like typing speed and interaction patterns to distinguish legitimate users from potential fraudsters.
Recent changes, like the alteration of numeric keypads for security, are designed to thwart bots and hackers by disrupting predictable patterns that automated systems exploit. By understanding these metrics, we can better flag suspicious activities and enhance security measures.
Figure 31 Data Assets Required
Risk Profiling and Data Lake Architecture in Financial Services
The risk profiling of customers is crucial for identifying potentially fraudulent activity, particularly for frequent travellers who may present a riskier profile due to the nature of transactions originating from multiple locations. In the onboarding process at NFI, customers are assigned a reset score that encompasses multiple factors, including creditworthiness and money laundering risk. The industry collaborates to share information about emerging fraud patterns to minimise risk across the ecosystem.
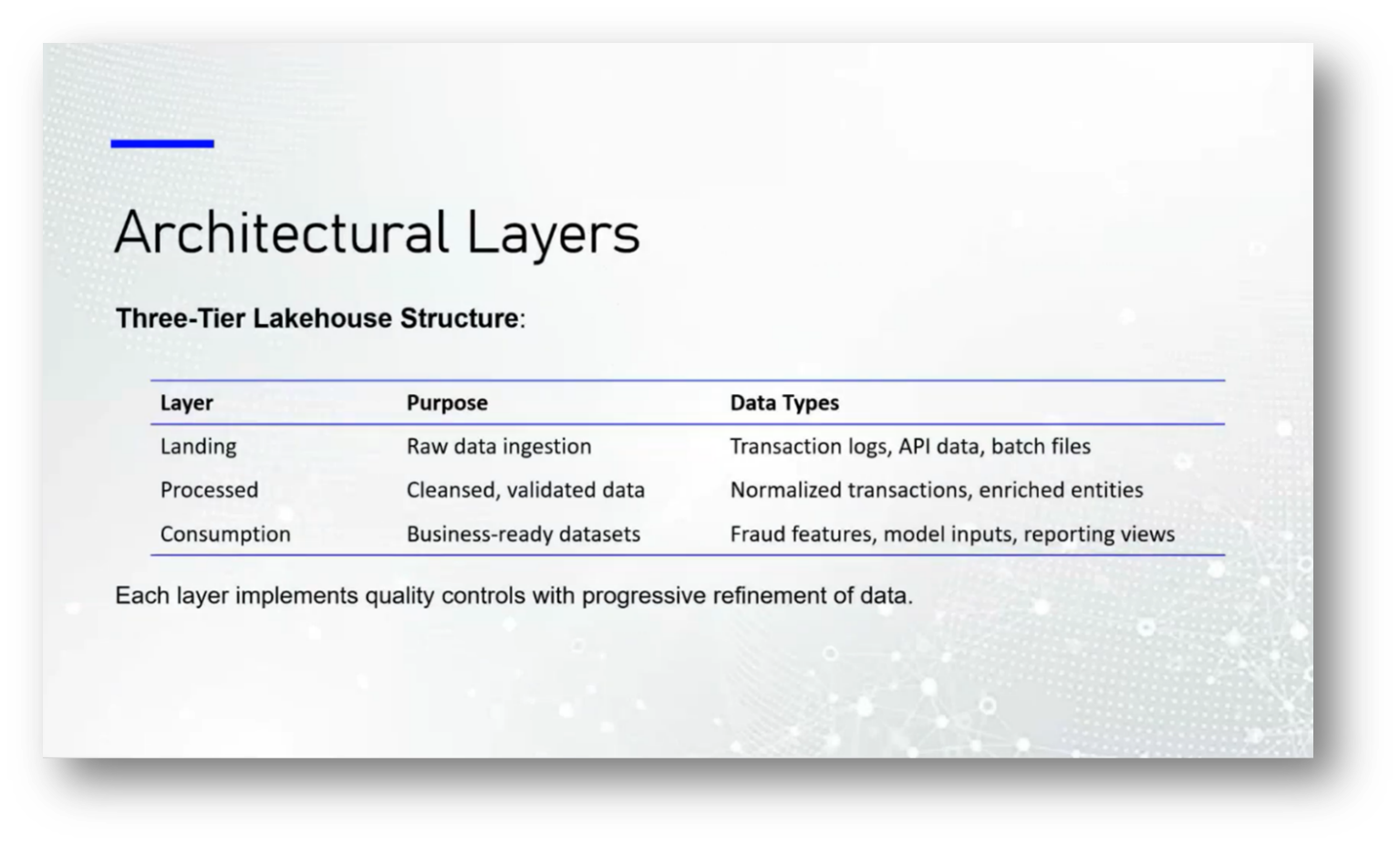
To enhance Data Management, the lake house architecture combines Data Lake storage with data warehouse capabilities, enabling rapid transaction processing through pre-calculated jobs while maintaining a unified governance framework. This approach allows for flexible data storage and efficient processing, ensuring comprehensive oversight of all incoming data.
Figure 32 Data Lakehouse Architecture Overview
Understanding the Fraud Ecosystem in the Banking Industry
Vanessa focuses on the decision to utilise a Data Lake based on cost and the necessary functionalities for processing transactions, specifically addressing the ACID principles: Atomicity ensures that a transaction is either fully completed or not executed at all; Consistency requires that the state of accounts is validated before and after transactions; Isolation guarantees that concurrent transactions do not interfere with each other; and Durability ensures that once a transaction is recorded, it remains permanent.
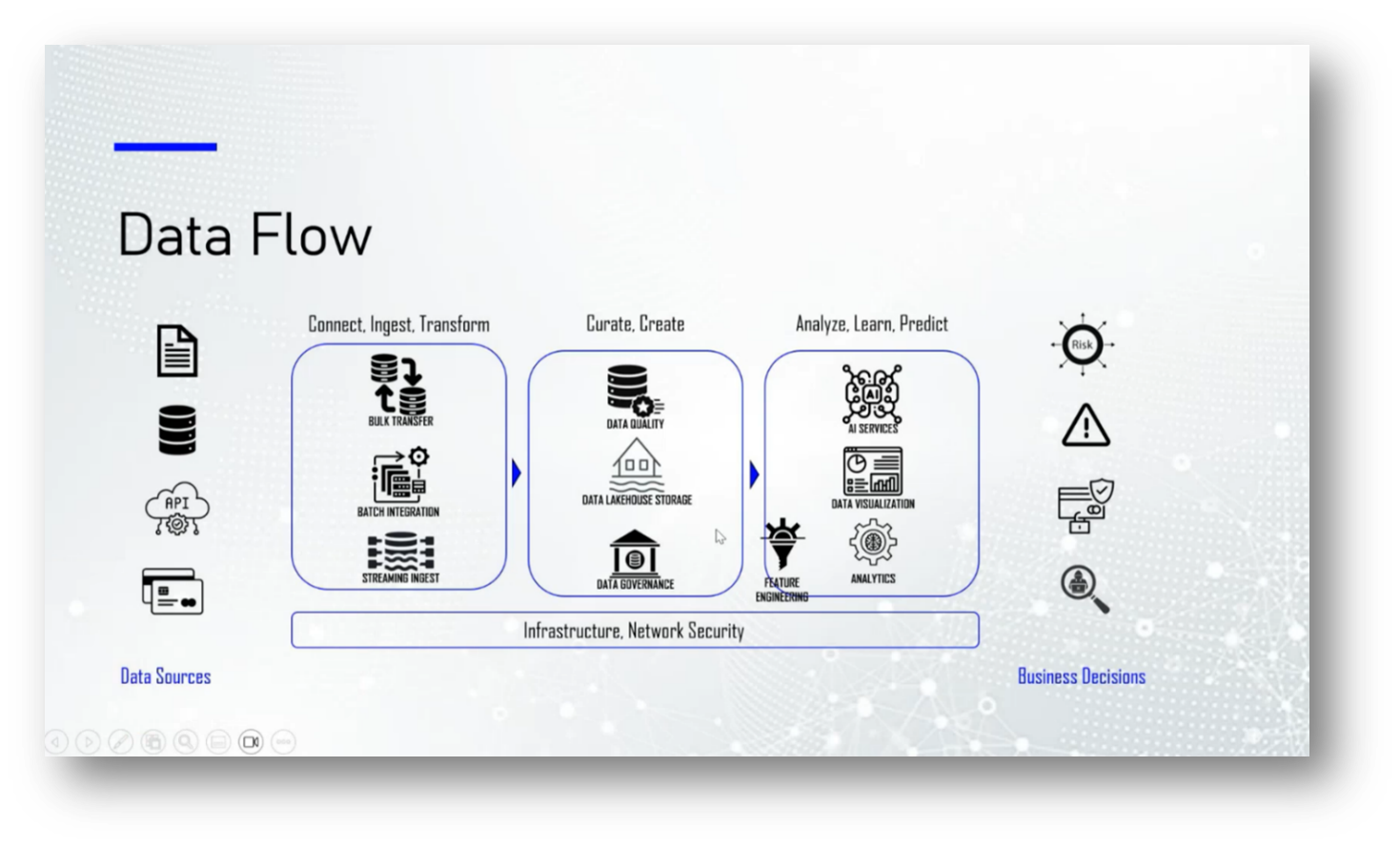
The integration of Business Intelligence (BI) tools and workload support complements this framework, allowing for real-time data ingestion from various sources such as transaction logs and APIs. Data is cleansed, validated, and normalised to maintain integrity, leading to well-structured datasets ready for modelling and reporting, thus facilitating consistent access across the Data Lake.
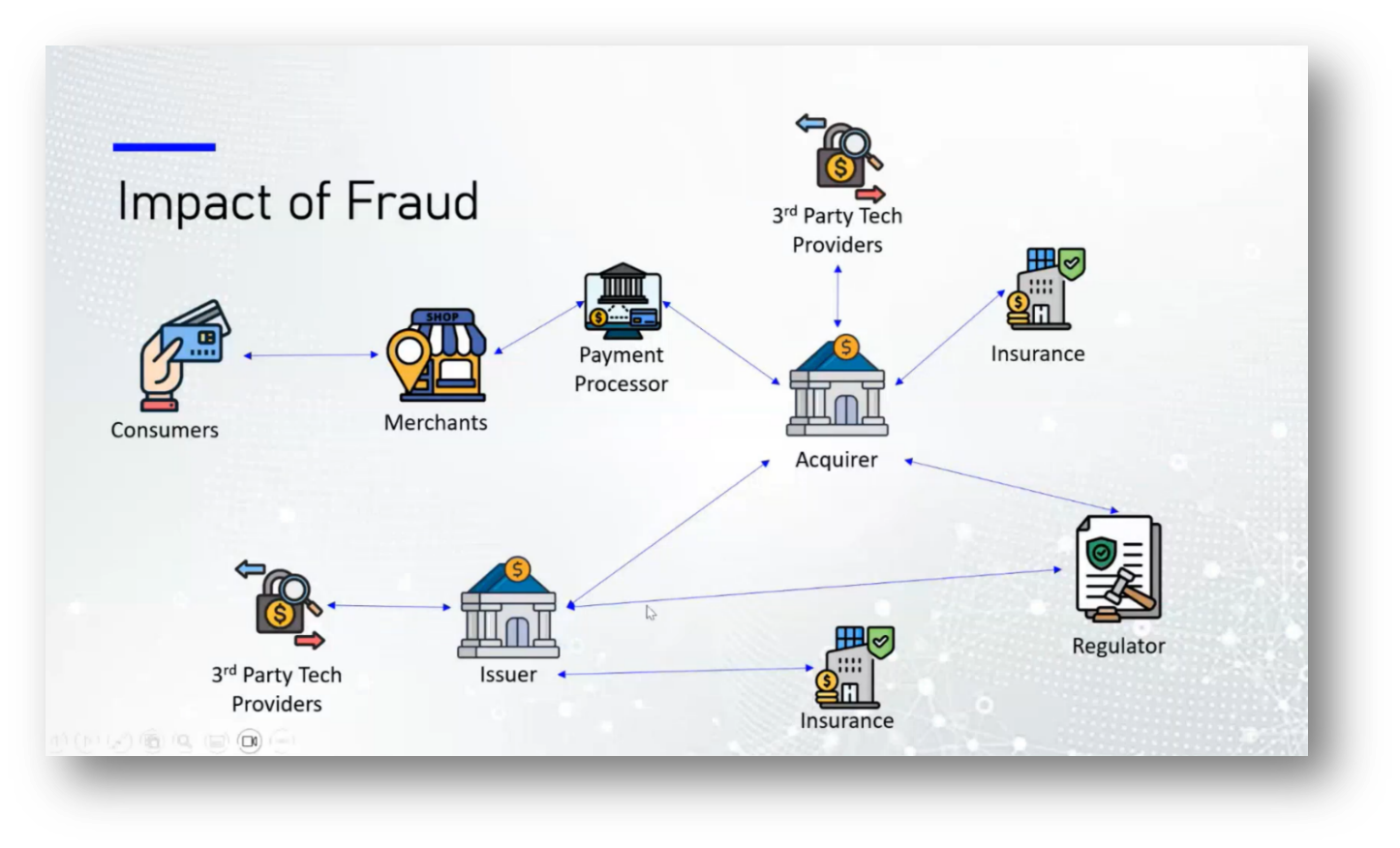
Data Governance requires a comprehensive data dictionary to ensure effective functionality across all activities, as partial dictionaries can lead to inefficiencies. A cohesive analytical service is essential for making informed business decisions, particularly in response to alerts such as fraud indicators, which can assist law enforcement in capturing criminals. This ecosystem relies on robust infrastructure and network security. In the context of fraud prevention, the flow of transactions involves various actors, including the acquiring bank, payment processors, and issuing banks, which may or may not be the same.
Third-party technology plays a crucial role in transaction monitoring, as it is often impractical to manage all fraud detection processes in-house. Regulatory complexities arise when different jurisdictions govern these entities, prompting the banking industry to standardise practices for smoother operations and clearer accountability.
Figure 33 Architectural Layers
Figure 34 Data Flow
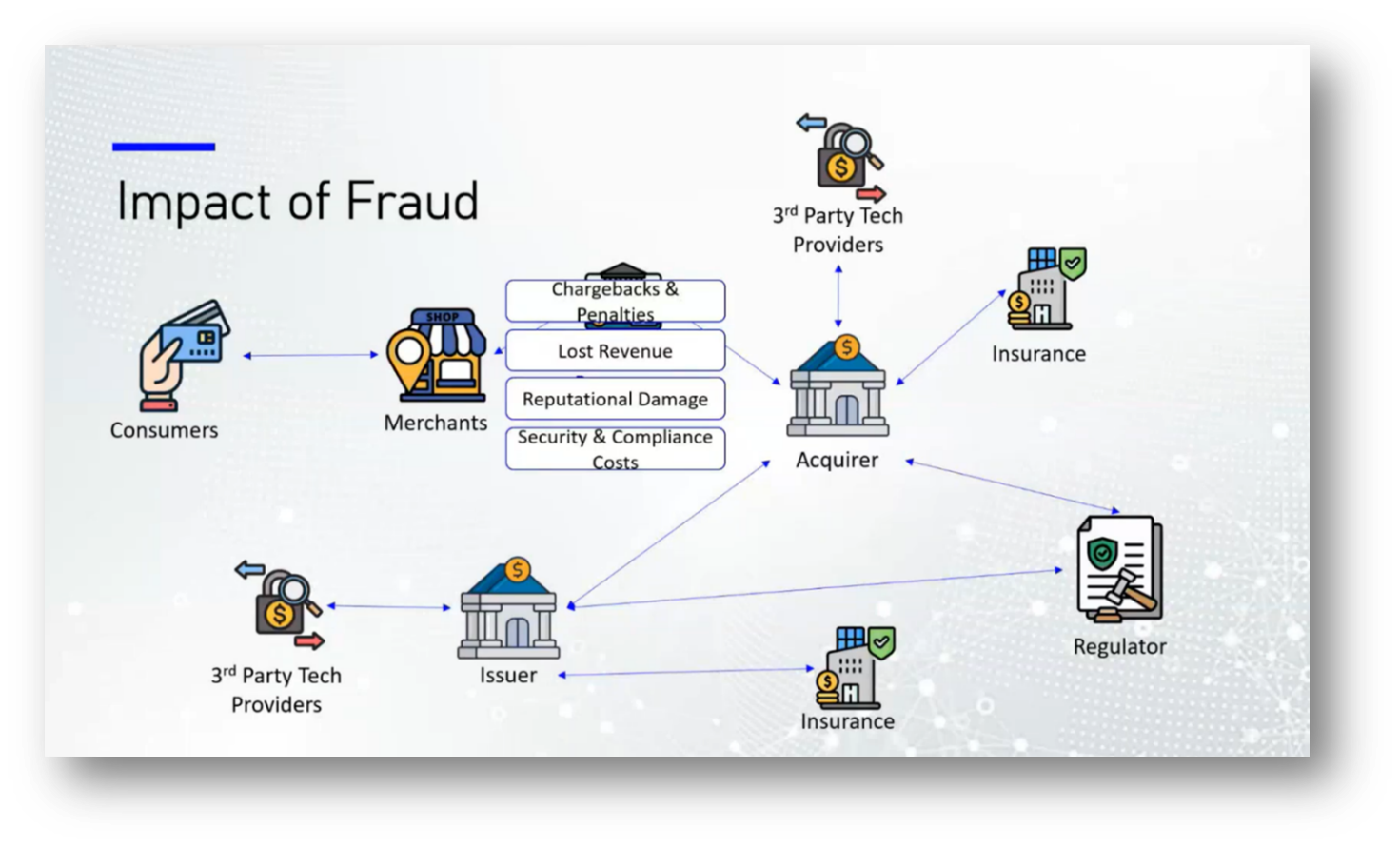
Figure 35 Impact of Fraud
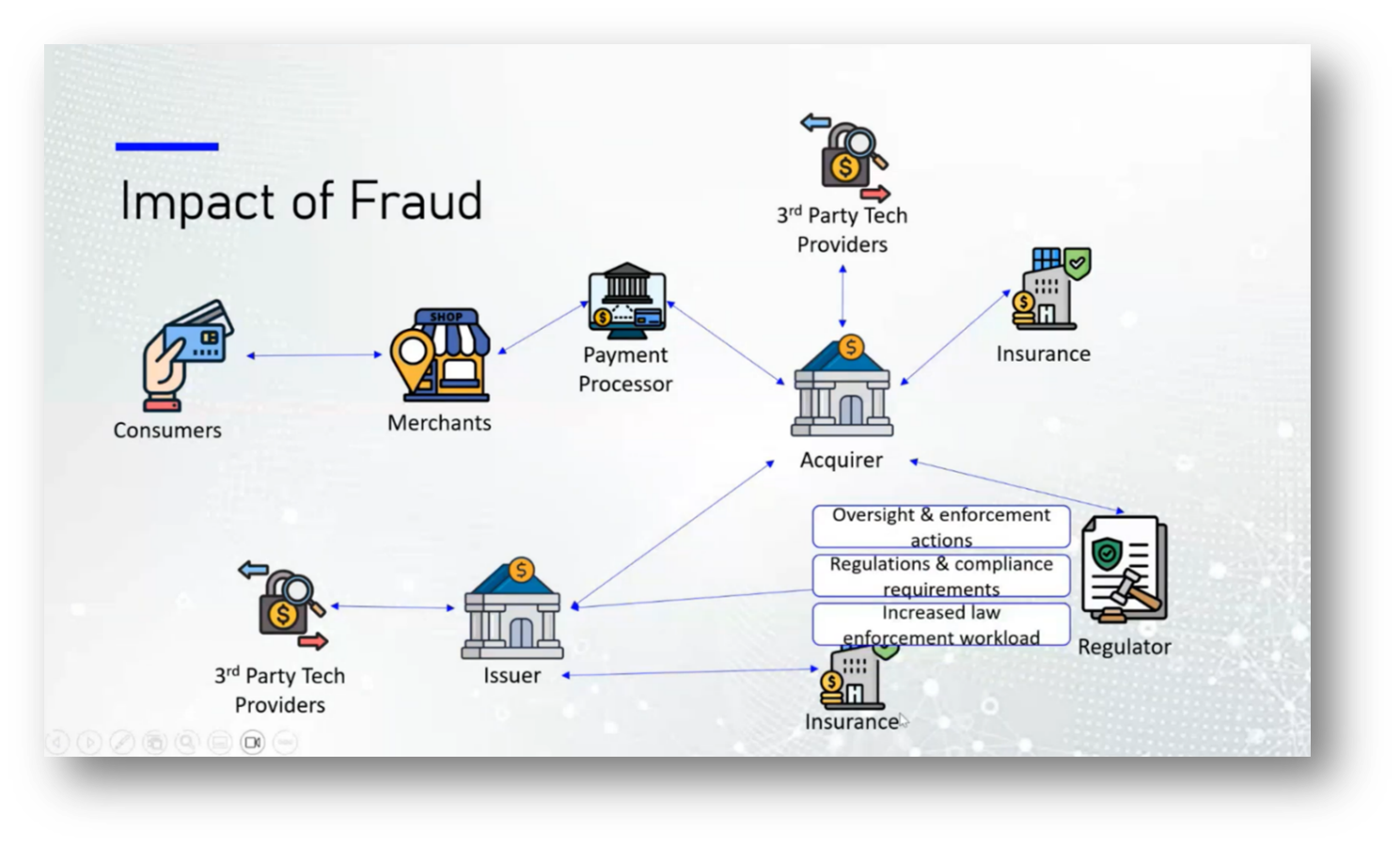
The Impact of Fraud on the Financial Ecosystem
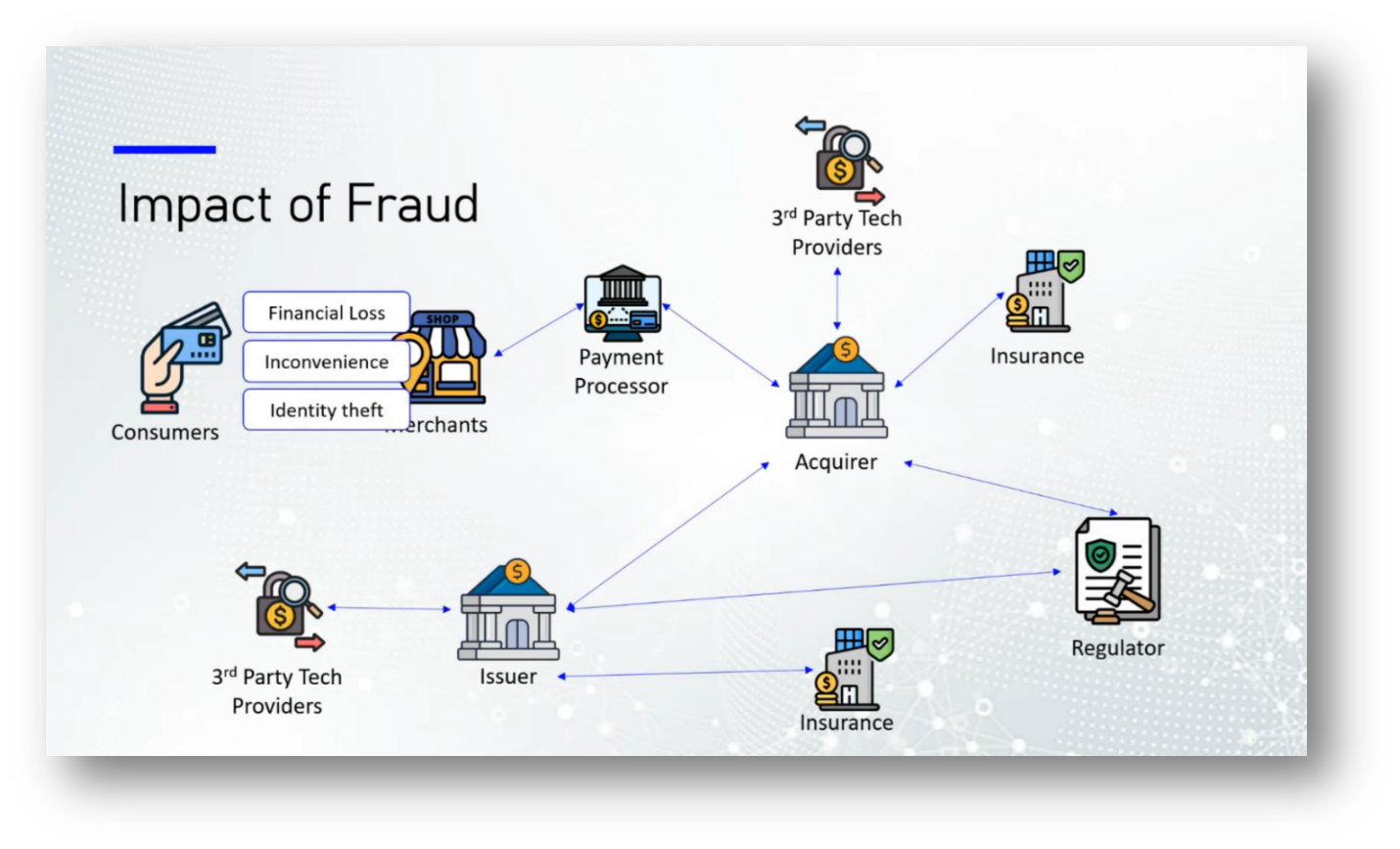
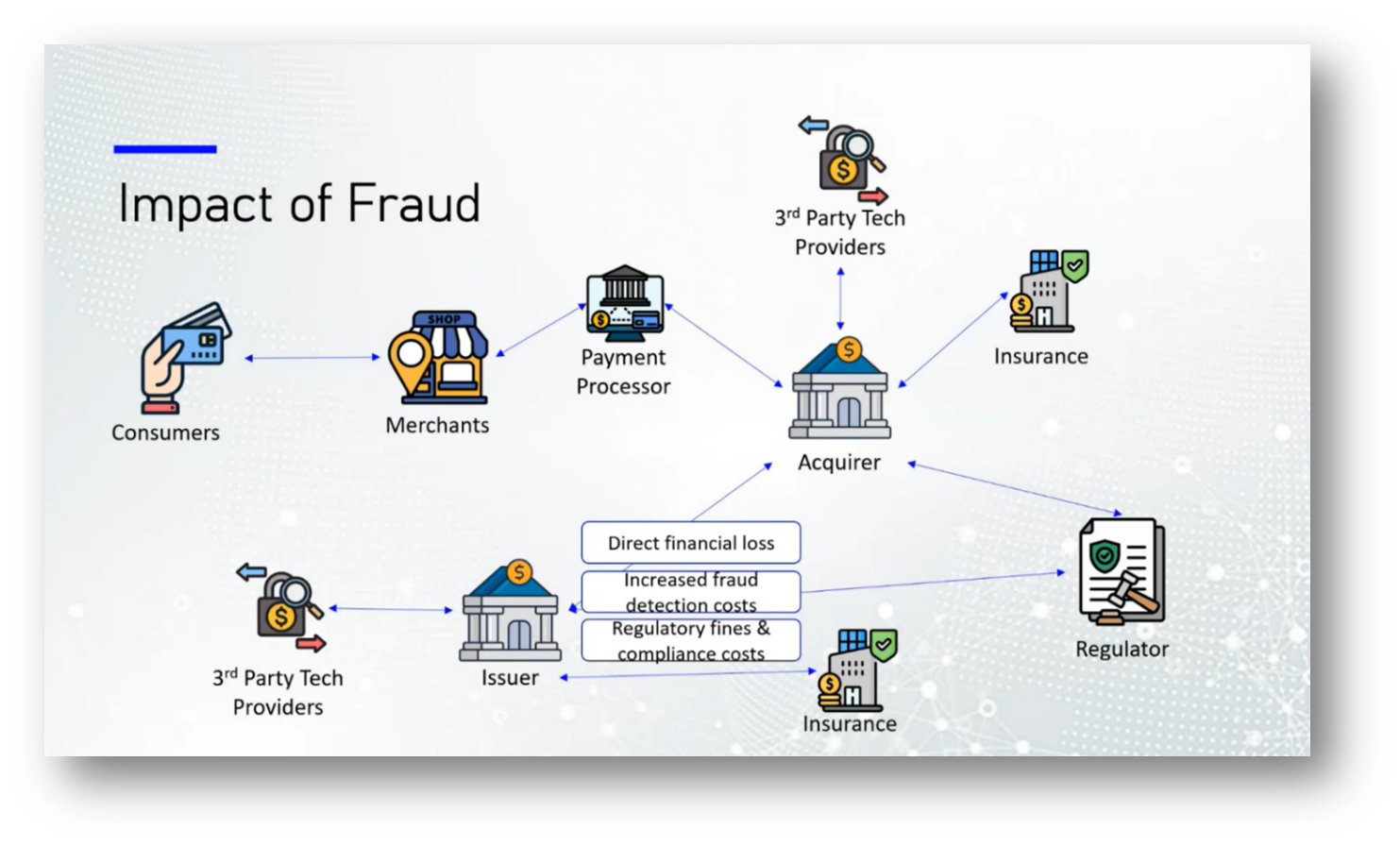
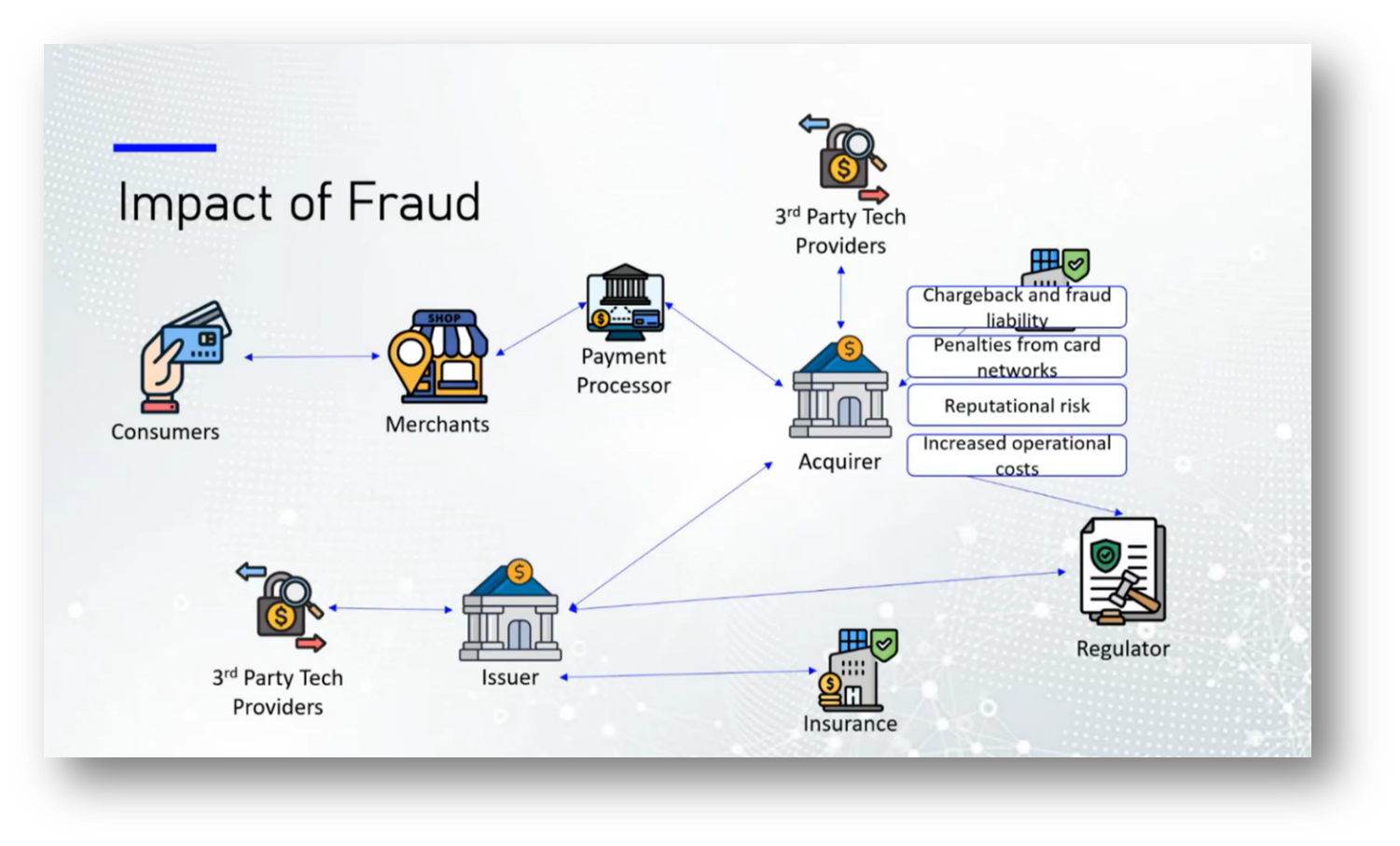
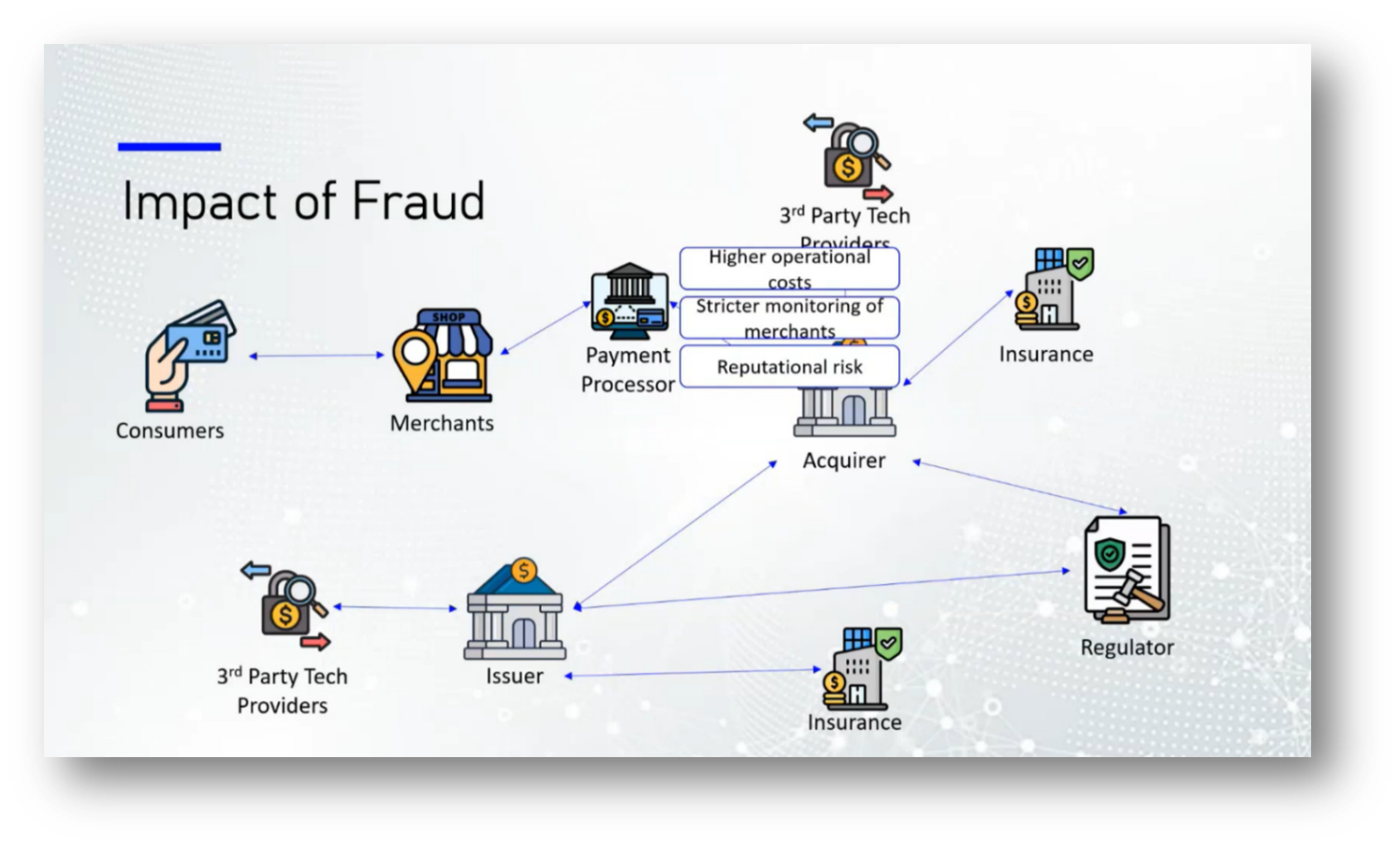
Fraud within the financial ecosystem poses significant risks to various stakeholders, including consumers, merchants, issuers, and payment processors. Consumers face financial losses, identity theft, and erosion of trust in their banks. Merchants suffer chargebacks and reputational damage without compensation for fraudulent transactions, alongside increased security and compliance costs. Issuers experience direct financial losses, regulatory fines, and customer attrition due to data breaches, while payment processors incur higher operational costs and reputational risks due to stricter compliance requirements. Overall, investing in fraud protection is more cost-effective than the repercussions of being hacked, as evidenced by trends observed in countries like Canada and Peru, where penalties for fraud often outweigh the costs of preventive measures.
The work of regulatory bodies is essential in making it more costly for companies to commit fraud than to invest responsibly. Consumers often delay experiencing the consequences of such fraud, leading to a lack of immediate urgency regarding their losses. This situation raises concerns about why protecting consumers, particularly the most vulnerable who have the least power and decision-making ability in investments, is not prioritised more aggressively. Advocates argue that safeguarding consumer interests should be paramount to prevent fraud and ensure a fair marketplace.
Figure 36 Impact of Fraud Pt.2
Figure 37 Impact of Fraud Pt.3
Figure 38 Impact of Fraud Pt.4
Figure 39 Impact of Fraud Pt.5
Figure 40 Impact of Fraud Pt.6
Figure 41 Impact of Fraud Pt.7
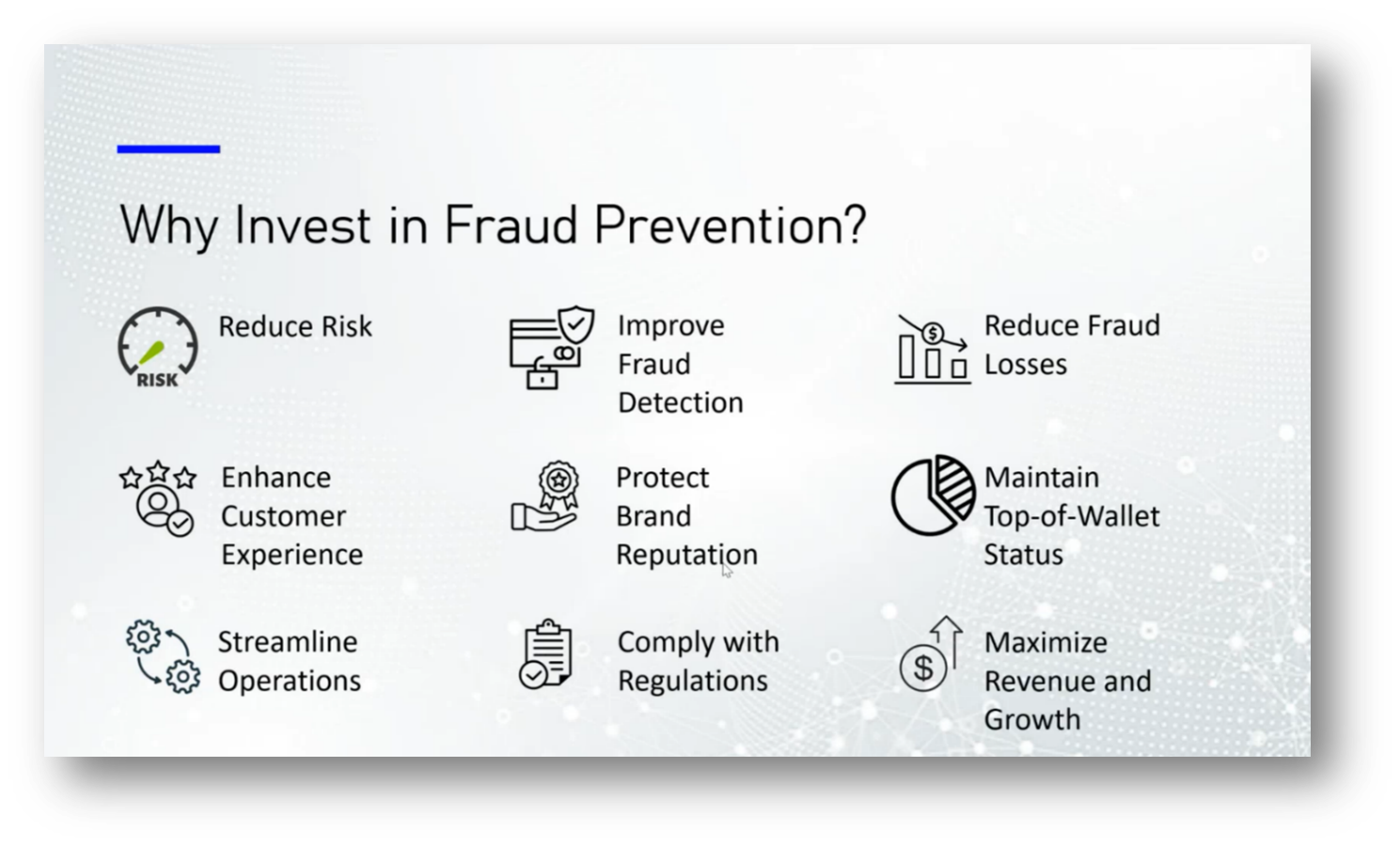
Figure 42 "Why Invest in Fraud Prevention?"
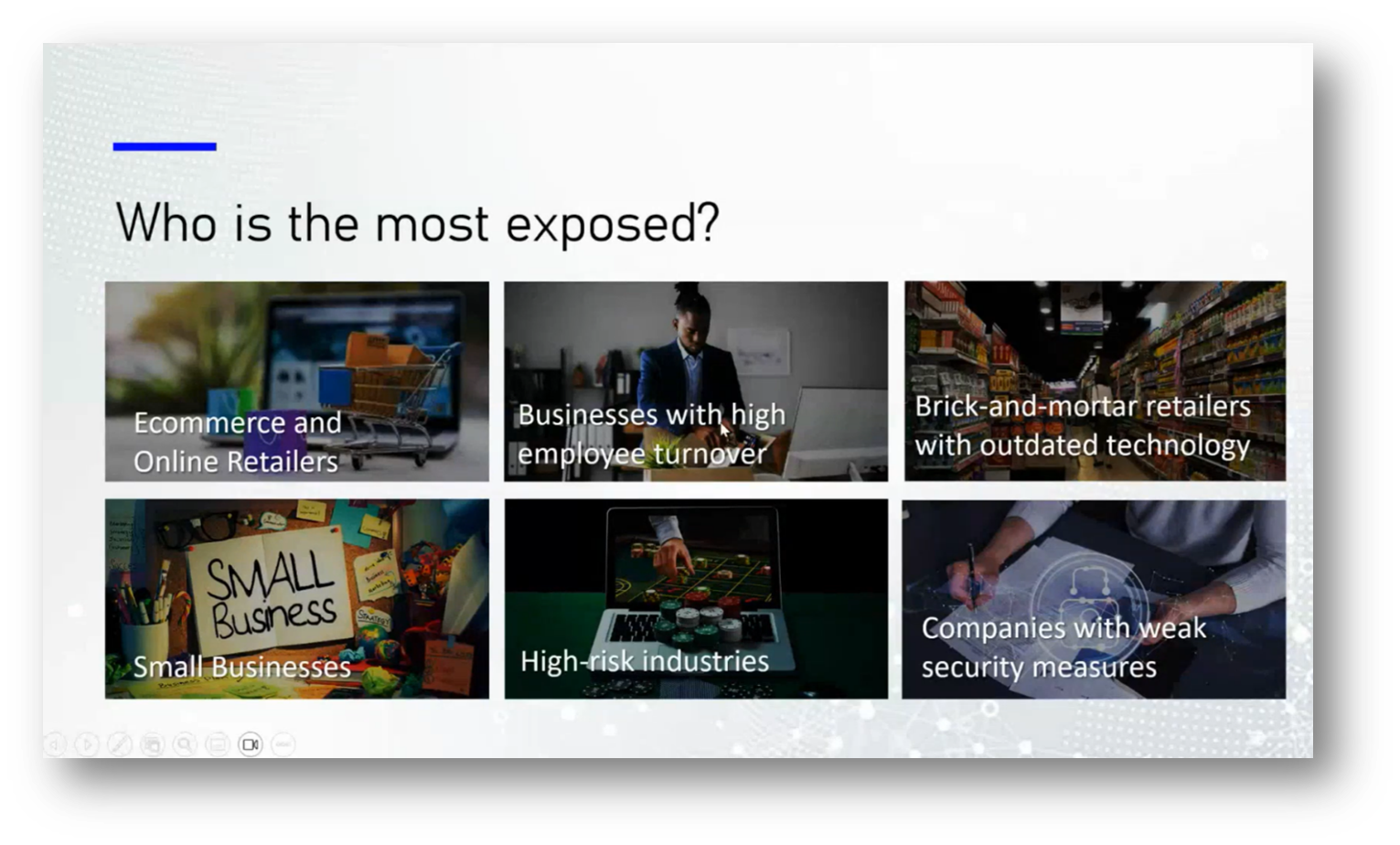
Figure 43 "Who is the most exposed?"
Information Security in Businesses
Vanessa highlights the entities most vulnerable to fraud, including e-commerce businesses due to online fraud risks and card-not-present transactions. Small businesses often lack the resources for necessary security infrastructure, while high employee turnover can increase opportunities for internal fraud as departing staff may expose security weaknesses.
High-risk industries, like gambling, are frequent targets for hacking, alongside brick-and-mortar retailers that fail to invest in updated technology. Companies that do not prioritise information security are also at risk. The session concluded with gratitude for participants, especially Marita and Vanessa, and an invitation to connect for further discussion or questions.
Figure 44 Vanessa Tarazona
Figure 45 Closing Slide
Data Security and Protecting Personal Information
In the closing discussion of the webinar, the attendees and Marita engage in the implementation of a Data Lake House. Concerns are raised regarding the handling of sensitive information related to nuclear power plants, necessitating stringent field-level security measures.
Marita emphasises the importance of Data Governance, stating that any personal information is encrypted upon arrival in the Data Lake and remains secure throughout the data processing stages. Integration teams are tasked with ensuring that data flows are protected using SSL and other security protocols from the source to the Data Lake. Additionally, tokenisation techniques are employed at the outset to allow for the management of sensitive information during processing.
If you would like to join the discussion, please visit our community platform, the Data Professional Expedition.
Additionally, if you would like to be a guest speaker on a future webinar, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!