Data Privacy Certifications
Executive Summary
This webinar covers the topic of data privacy and certifications related to it. It includes an overview of various certifications available for privacy and information security professionals and the components of data privacy certification. Howard Diesel highlights the importance of governance and data management in various areas and the significance of GDPR and data governance in the industry. The webinar covers other topics, including privacy technologist certification, privacy governance and architecture, analysis and interpretation of call centre data, and data lifecycle and governance considerations. Additionally, Howard discusses the ISO 27001 certification, its benefits, and the strategies and concepts involved in data privacy and security measures.
Webinar Details:
Title: Data Privacy Certifications
Date: 06 December 2021
Presenter: Howard Diesel
Meetup Group: Data Privacy & Protection with Caroline Mouton
Write-up Author: Howard Diesel
Contents
Certifications in Data Privacy
Data Privacy Certification and its Components
Data Privacy and Certification
Certifications in Privacy and Information Security
Privacy Technologist Certification
Data Privacy and Security Measures
Strategies and Concepts in Data Privacy and Security
Analysis and Interpretation of Call Centre Data
Overview of Certifications and Privacy Solutions
Privacy Governance and Privacy Architecture
Principles, Policies, and Data Management in Privacy
Data Lifecycle and Data Governance
Privacy Framework and Data Lifecycle Considerations
ISO 27001 Certification and its Benefits
Importance of GDPR and Data Governance in the Industry
Privacy, Governance, and Data Management
The Importance of Governance in Various Areas
Certifications in Data Privacy
Howard covers various data privacy and certification discussions, including the penalties and fines associated with the Protection of Personal Information Act (POPIA), a POPIA-based model for reporting on privacy assessments on warehousing incidents, and the impact of data architecture on it. He also covered data classification, search data cataloguing, evaluation criteria for data privacy programs, and using master data for data privacy. Additionally, data privacy certifications were introduced to test understanding in various areas, with the development of a web of related certifications observed during a visit to ISACA.
Figure 1 Data Privacy Certification
Figure 2 Important areas of Data Privacy
Data Privacy Certification and its Components
Data privacy certifications provide individuals with a comprehensive understanding of jurisdictional laws, regulations, enforcement models, and legal requirements for handling and transferring data. It is crucial to comprehend the laws and regulations of different countries, especially when dealing with international customers or users. Privacy programs should encompass the jurisdictional laws of all areas where the company operates rather than focusing solely on local laws. Building a generic and abstract privacy program that can be specialised for different jurisdictions helps achieve this. Data privacy certifications validate knowledge but not necessarily practical capability, which practical courses address.
Data Privacy and Certification
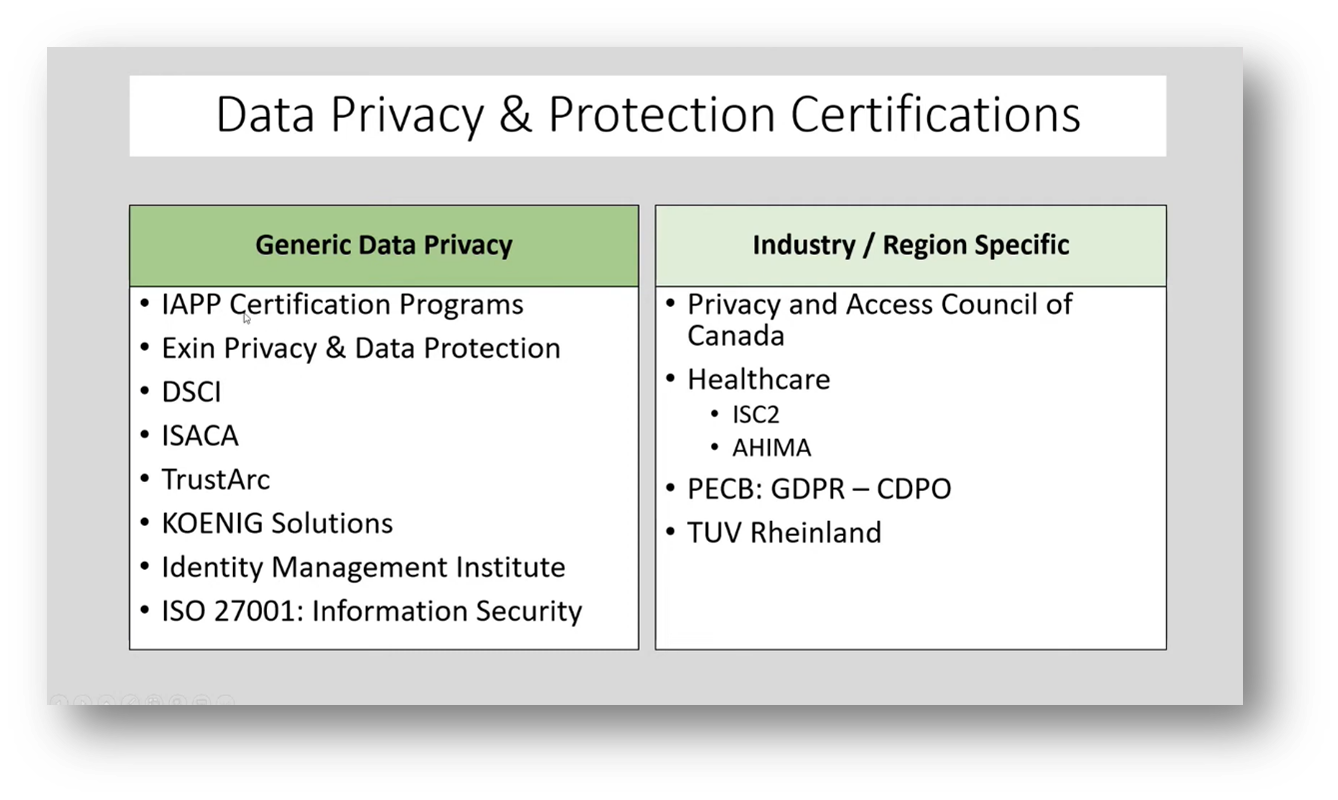
Data privacy is an important field that requires knowledge and skills in various areas, such as privacy governance, privacy architecture, and data life cycle management. The International Organization for Standardization (ISO) has created a privacy information management system standard - ISO 27701. In addition, iapp.org offers a data privacy technologist body of knowledge and multiple certifications categorised based on different levels of expertise and specialisation. Meanwhile, ISACA focuses on governance, privacy architecture, and data life cycle management in mitigating data privacy risks. To succeed in this field, choosing a specific area to focus on is crucial, which may involve understanding laws and regulations and the data life cycle, starting from planning and signing agreements before data collection.
Figure 3 Data Privacy and Protection Certifications
Certifications in Privacy and Information Security
Privacy and information security comprise three key areas: legal interpretation and implementation, privacy-enabling technologies, and architectural integration. Obtaining ISO 27001 certification can help establish a GDPR program, but industry or region-specific certifications may also be necessary. The International Association of Privacy Professionals (IAPP) offers three core certifications for privacy professionals, including Information Privacy Professional (practising privacy), Certified Information Privacy Manager (operationalising privacy), and Certified Information Privacy Technologist (engineering privacy practices). It's important to note that while the IAPP is accredited under ISO standard 17024, it emphasises certification over security. Understanding privacy laws requires seeking professional advice for accurate legal interpretation, while operationalising privacy involves integrating privacy practices into organisational processes. Finally, privacy technologists are responsible for building privacy practices into products.
Figure 4 Must-have Privacy Certifications
Figure 5 Information Privacy Technologist
Privacy Technologist Certification
The Privacy Technologist Certification focuses on implementing data protection throughout every stage of development, recognising the benefits and challenges of different technologies, and auditing technologies in place to identify potential gaps in privacy practices. One example of a challenge is managing personally identifiable information when users connect their data via self-service business intelligence. The role of a privacy technologist requires continual vigilance similar to that of a friend specialising in virus protection.
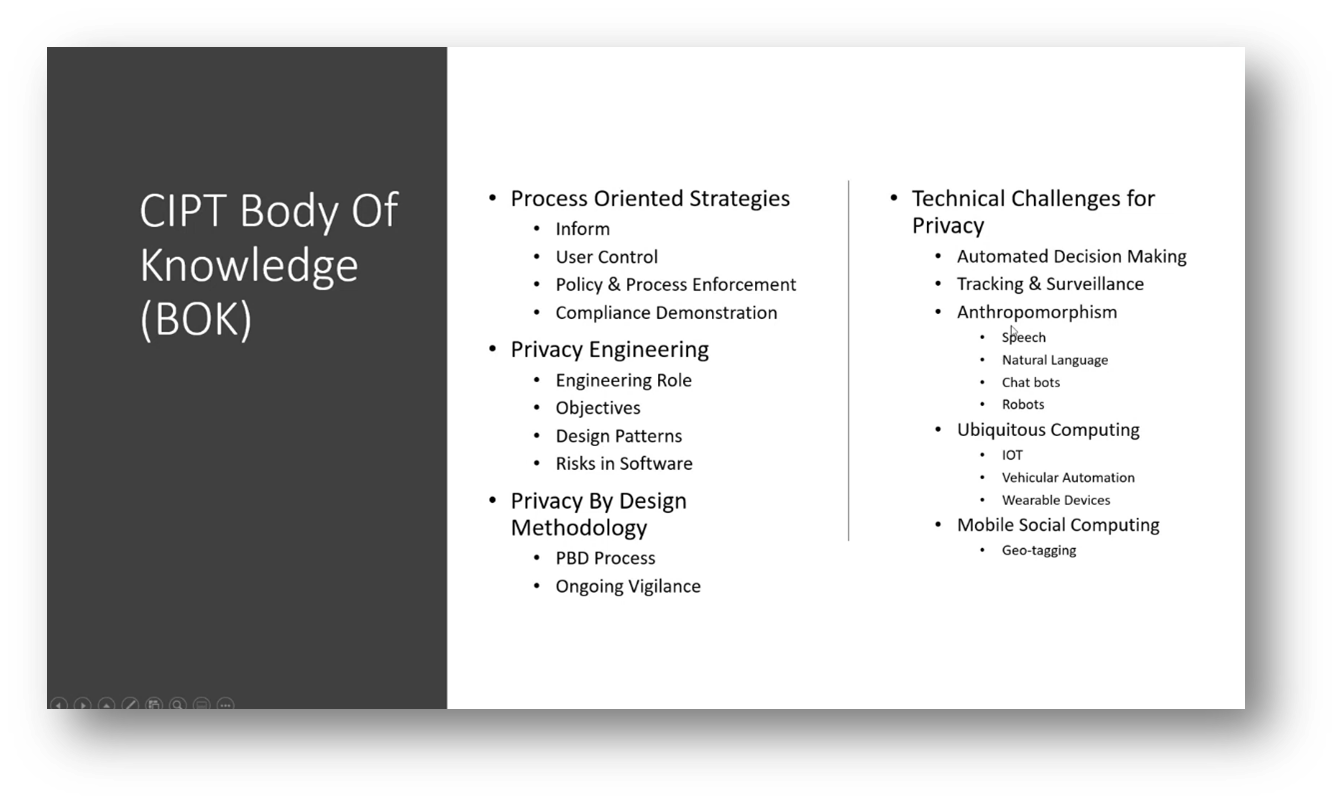
Figure 6 CIPT Body of Knowledge (BOK)
Data Privacy and Security Measures
Howard highlights the importance of understanding and addressing the growing risks associated with data exposure. He discusses the foundational principles and strategies of data privacy, including privacy risk models, privacy by design, venue-sensitive design, and the data life cycle. Howard also emphasises the need to minimise, abstract and hide data to protect privacy and enhance security. Separation of data is crucial, and the PCI standards are cited as a good practice. Data privacy threats and violations can occur during collection, use, dissemination, and intrusion (cyber attacks), and two approaches to ensuring data privacy are the data-oriented approach and the process-oriented strategy.
Figure 7 CIPT Body of Knowledge (BOK) continued
Strategies and Concepts in Data Privacy and Security
To protect data privacy, people use various techniques such as aggregation, de-identification, encryption, IIM, and authentication. Process-oriented strategies include informing data subjects of their rights, implementing user control policies, enforcing processes, and demonstrating compliance with regulators. Privacy engineering involves identifying and mitigating risks within software at the coding level. Challenges in data privacy include encryption, decommissioning devices and software, and addressing technical challenges in automated decision-making, AI, machine learning, tracking, surveillance, anthropomorphism, speech, chatbots, and robots. Considerations in data privacy involve ubiquitous computing, IoT, vehicle automation, wearable devices, and voice recordings.
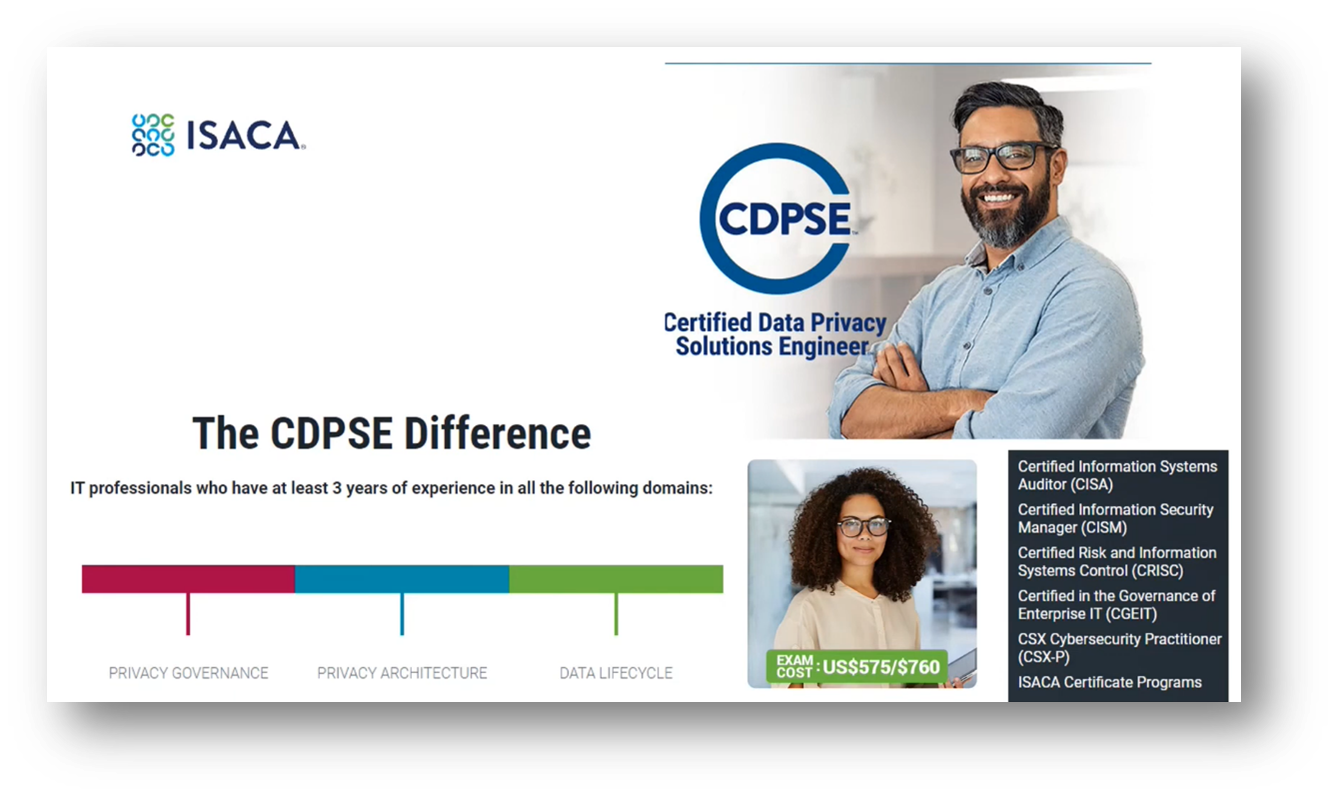
Figure 8The CDPSE Difference
Analysis and Interpretation of Call Centre Data
Howard mentions the challenges and possibilities of analysing and interpreting data from call centres. An AI developer in Ireland has created a system that can manipulate and mask data in audio and video recordings. Additionally, situational thinking in call centres is advocated for, where call rates do not just measure the effectiveness but also analyse what people say about products and the organisation. Taxonomies and semantic analysis interpret call centre data and provide feedback on customer experiences and interactions. Howard acknowledges the excitement of AI advancements in analysing call centre data but highlights privacy concerns due to the amount of information shared. It's mentioned that a bank samples call centre recordings to analyse the tonality and detect underlying emotions that may not be expressed in the text. Howard emphasises how interpreting sarcasm, politeness, and other nuances in call centre data is essential to understanding the true message being conveyed.
Figure 9 CDPSE Facts
Overview of Certifications and Privacy Solutions
ISACA and The AI App are two companies that offer privacy solutions. ISACA specialises in privacy governance, architecture, and data lifecycle management and offers a privacy solution engineer certification program that costs between $575 and $760. So far, 15,000 professionals have been certified by ISACA since 2020. Additionally, ISACA's certification requires a strong grasp of data lifecycle management, retention policies, compliance with legal requirements, and the ability to identify privacy threats, mitigate risks, and optimise end-user experience. The CDNP certification, which requires three years of relevant professional work, offers both online and in-person training, and the exam is completed in three and a half hours. The DMBOK certification, on the other hand, is a 110-question exam that takes one and a half hours to complete.
Figure 10 Data Privacy Engineer Core Capabilities
Figure 11 Privacy Governance
Privacy Governance and Privacy Architecture
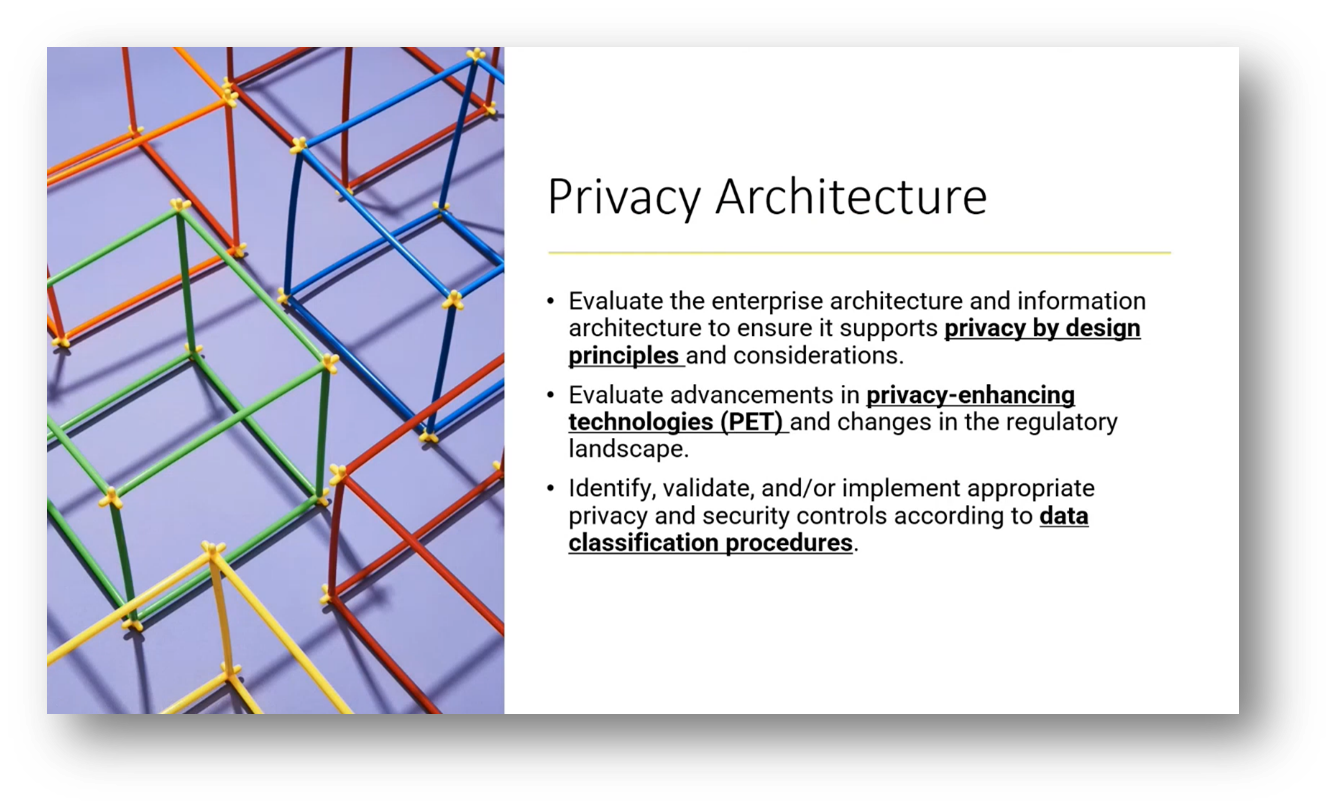
Privacy governance involves ensuring compliance with legal requirements and evaluating internal and external needs while considering the organisation's size and level. Bridging the gap between legal and IT aspects of data privacy, privacy specialists facilitate a common understanding of best practices. From the beginning, privacy architecture must be aligned with business requirements, and privacy impact assessments, implementation of procedures, and contract management are essential. Privacy by design and prioritisation of practices should be implemented, and performance metrics and data governance should be evaluated. Privacy incident management and risk assessment are crucial while training and promoting awareness are necessary. Identifying issues requiring remediation and opportunities is part of privacy governance, as is evaluating enterprise and information architecture to support privacy by design.
Figure 12 Privacy Architecture
Figure 13 Data Lifecycle (Purpose and Persistence)
Principles, Policies, and Data Management in Privacy
Howard discusses important policies and principles for data management, emphasising the challenge of implementing them in practice. He highlights the difficulty of data cleanup and the need to incorporate privacy principles into data modelling, coding, and application development. Encryption and data classification procedures, such as ROPA, are essential tools for protecting privacy. The regulatory landscape also influences privacy practices. Finally, the data lifecycle approach emphasises the importance of understanding the purpose of data before building any systems or processes.
Data Lifecycle and Data Governance
The Data lifecycle is similar to governance and privacy-related requirements but specifically focuses on the stages of data. It is recommended to have a generic data lifecycle and map specific statuses onto it for better management. Multiple individuals have emphasised the significance of following the proposed data lifecycle and data flow. The scope of a privacy program is vast, and it is crucial to target significant areas for improvement. Initial steps include data discovery exercises, creating a classification scheme, training and awareness on privacy by design, and conducting privacy impact assessments. A risk framework is in place to identify and address the riskiest risks and processing issues. While the data governance process is still developing, progress is being made slowly.
Figure 14 Who should be Certified?
Privacy Framework and Data Lifecycle Considerations
Howard emphasises the importance of privacy and alignment with the EU Data Protection Board's framework. He discusses the DMBOK lifecycle, which includes plan and designer enable stages, and highlights the need to ask privacy questions at each stage to avoid issues. Howard stresses the need for mitigation practices and procedures related to the data lifecycle to be implemented. He also highlights that different areas such as architecture, modelling, design, enabling, and destruction have different focuses but must consider privacy. Howard notes that data lifecycle considerations involve evaluating enterprise and information architecture with privacy by design and that dissemination processes, controls, and data validation require attention. Additionally, designing, implementing, and monitoring processes and procedures to keep inventory and data flow records current is important. Data privacy should concern almost everyone in the organisation, including data scientists who enrich data and need to conduct impact assessments. Finally, the summary suggests that ISO 27001 is a best-practice approach for managing information security.
Figure 15 ISO 27001 Definition: What is ISO 27001?
ISO 27001 Certification and its Benefits
ISO 27001 Certification is a legally recognised standard that is legally binding in South Africa, focusing on planning support, operations, performance evaluation, assessing risks, leadership, and continual improvement. It offers numerous benefits, such as data protection, increased attack resilience, reduced information security costs, and meeting industry requirements, particularly in larger organisations. Context is critical when implementing the rules, and ISO 27001 certification is essential to meet contractual obligations and respond to evolving security threats.
Figure 16 ISO 27001 Management system clauses
Figure 17 ISO 27001 Benefits
Importance of GDPR and Data Governance in the Industry
The General Data Protection Regulation (GDPR) has brought data privacy and enforcement to the forefront. Individuals with GDPR certification are in high demand. While understanding the legal aspects of data privacy is important, data governance and quality are crucial components in ensuring privacy and compliance. There is an overlap between the principles of GDPR, including ethics, confidentiality, and privacy. Organisations may find it challenging to get executive buy-in for data governance, but the legal obligation and potential fines motivate them to prioritise privacy. Implementing holistic data governance practices that start with privacy can lead to momentum within the organisation.
Privacy, Governance, and Data Management
Effective data management is driven by privacy concerns, leading to compliance and cost optimisation. The ultimate goal is to leverage data management to drive business growth and efficiency. To ensure privacy, it is crucial to distinguish between personally identifiable information (PII) and personal data, which is classified based on sensitivity levels. Regulatory frameworks, like GDPR and papaya regulations, are increasingly governing data governance. Privacy, governance, and data governance are interrelated and essential to meeting business requirements. Quality and privacy are interconnected, with GDPR and papaya advocating for information quality. Privacy requirements are aligned with King IV and other governance frameworks.
The Importance of Governance in Various Areas
The discussion revolved around the concept of governance, specifically its evolution over time. The adoption of King Three was seen as a mere tick-box exercise. In contrast, King Four separated tech from information and focused on making data its independent area. This move strengthened governance by introducing data principles, quality, and ethics. Everything being connected, from corporate governance to data governance and privacy governance, was emphasised. Rewriting governance principles at a corporate level and applying them to specific areas like data and people assets was deemed interesting. Furthermore, the notion of certification was briefly touched upon.
If you would like to join the discussion, please visit our community platform, the Data Professional Expedition.
Additionally, if you would like to be a guest speaker on a future webinar, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!