Storing P.I with Caroline Mouton
Executive Summary
Managing data and ensuring privacy comes with risks and challenges that must be addressed. It is crucial to have a robust Data Management system to mitigate these risks and safeguard sensitive information. However, maintaining Data Privacy can be challenging, especially with the increasing amount of data generated and shared. It is essential to adhere to privacy regulations and guidelines and employ advanced security measures to mitigate the risks associated with Data Management.
Webinar Details
Title: Storing P.I with Caroline Mouton
URL: https://www.youtube.com/watch?v=zQn7hz0nEhI
Date: 11 May 2023
Presenter: Caroline Mouton
Meetup Group: DAMA SA User Group
Write-up Author: Howard Diesel
Contents
Privacy and Data Protection: A Framework Approach
Privacy and Security Guidelines for Data Management
Data Classification and Storage in the Business Environment
Economic Valuation and Data Classification in Data Management
Data Classification and the Need for a Multifaceted Taxonomy
Challenges of Classifying Data and Privacy in Information Security
Metadata and Clarification in Data Transfers and Cross-Border Privacy Issues
Understanding Privacy Laws and Data Transfers
Sensitive Data and Vendor Assessment
Change Control and Privacy Design in Business Strategy
Zoho CRM's data storage issue and the importance of corporate policies
Compliance in Privacy Protection
Data Privacy Compliance and the Role of Data Privacy Officers
Privacy Operations and Qualifications for DPOs
The Role of the Information Officer and DPOs in GDPR
GDPR Compliance and Data Sharing Best Practices
Privacy Obligations and Data Sharing
Data Privacy Recommendations
Privacy and Data Protection: A Framework Approach
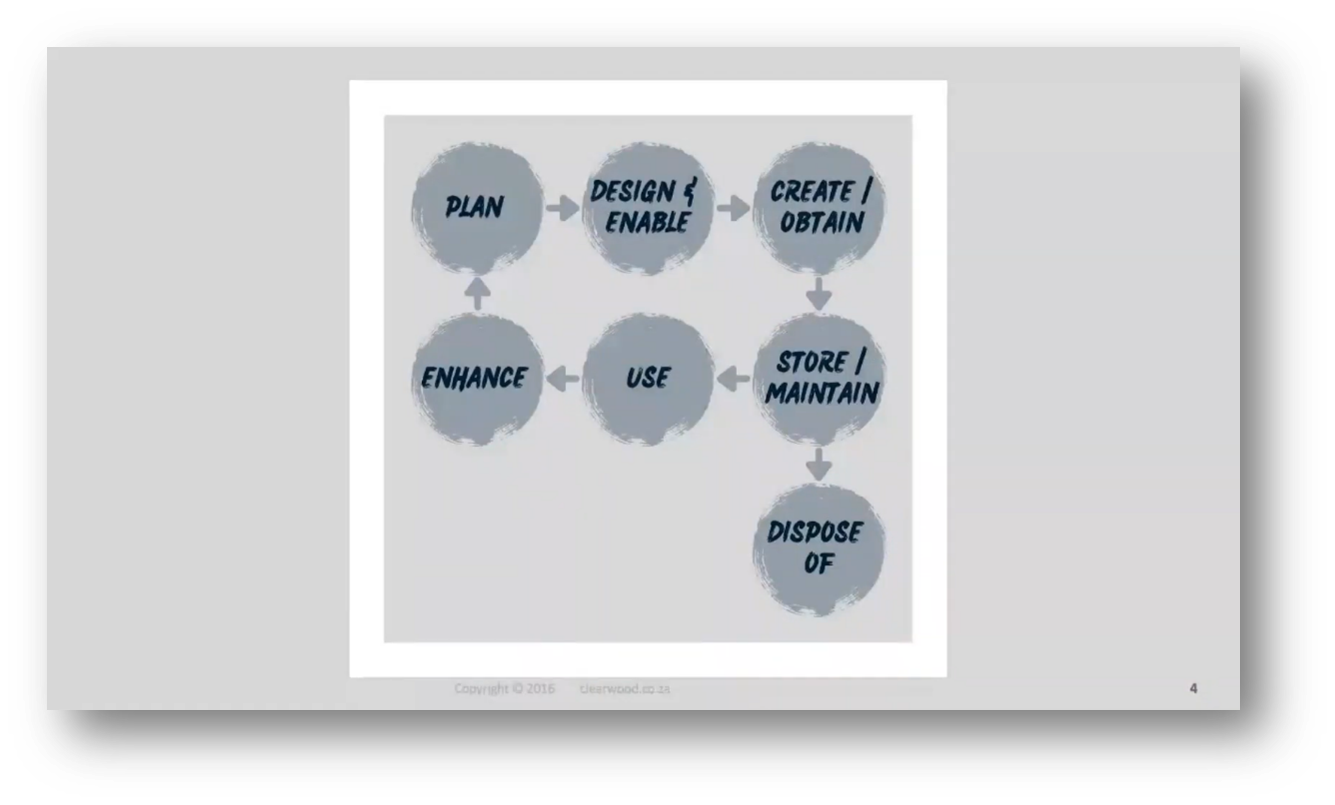
Caroline emphasises Data Management and privacy protection but states that legal advice is not something she can provide. The data protection life cycle includes planning, maintenance, and disposal. Managing data requires starting with the end in mind. Caroline advocates for “a riskiest risks” approach to privacy, including considerations for sharing and transferring data.
Figure 1 Lifecycle
Privacy and Security Guidelines for Data Management
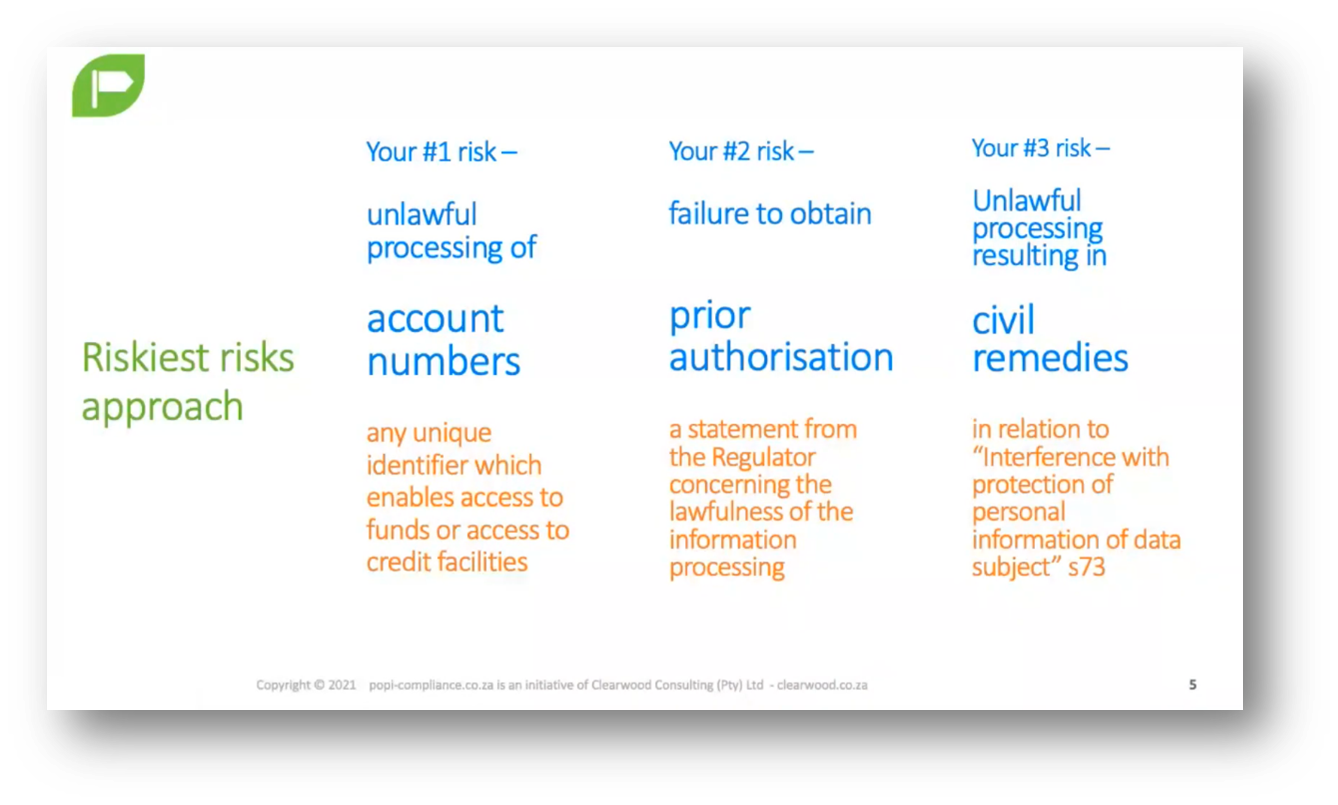
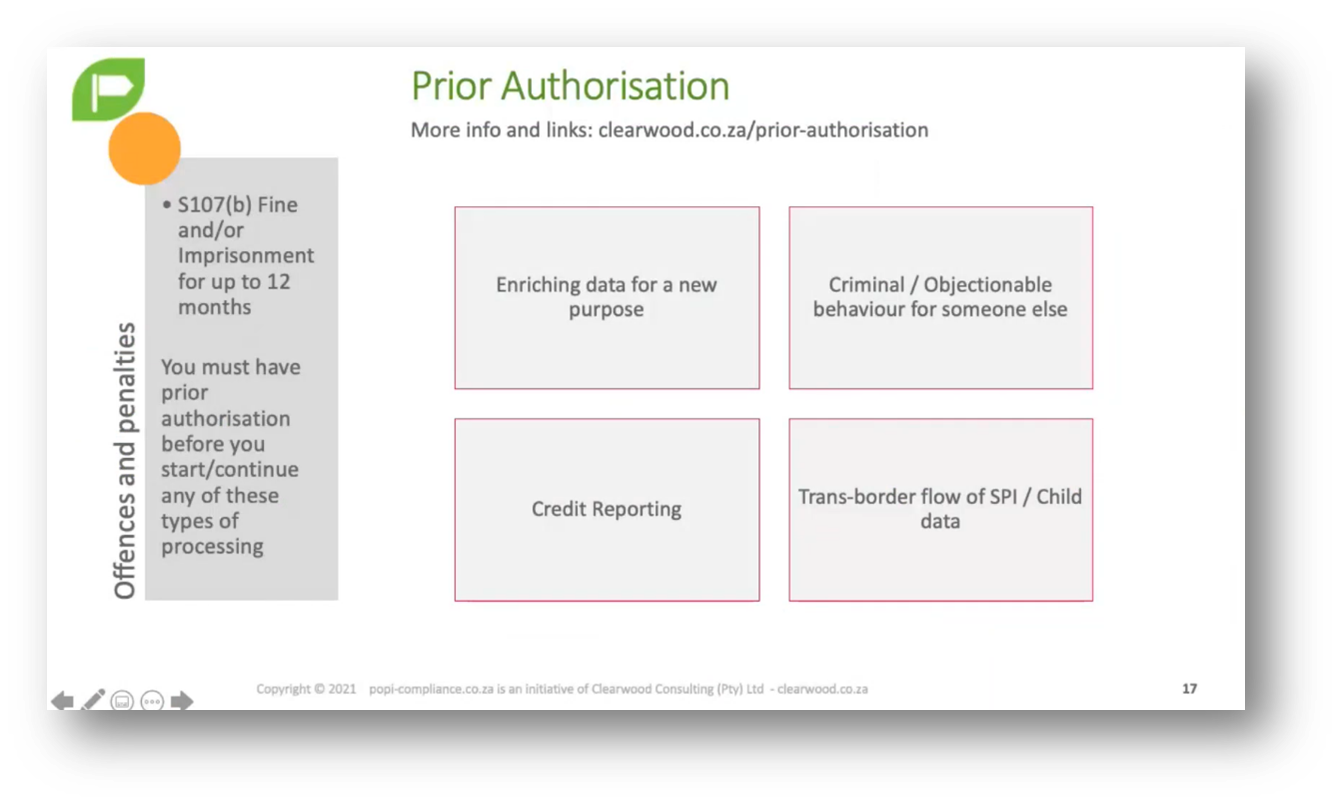
Penalties indicate potential privacy risks related to managing data, particularly financial account numbers. Breaches that could result in financial loss carry high penalties imposed by authorities. Prior authorisation plays a crucial role in Data Management, especially in transfers. When sharing information with others, obtaining appropriate authorisation to protect personal data is essential. Individuals can take legal action if their Data Privacy is compromised.
If someone interferes with the security and protection of personal information, they may face lawsuits and civil remedies. Avoid storing data unorganised and insecurely, referred to as a "swamp." Implement appropriate systems and practices to ensure data is securely stored and easily retrievable. Be mindful of cross-border data transfers, as different countries may have varying regulations and requirements.
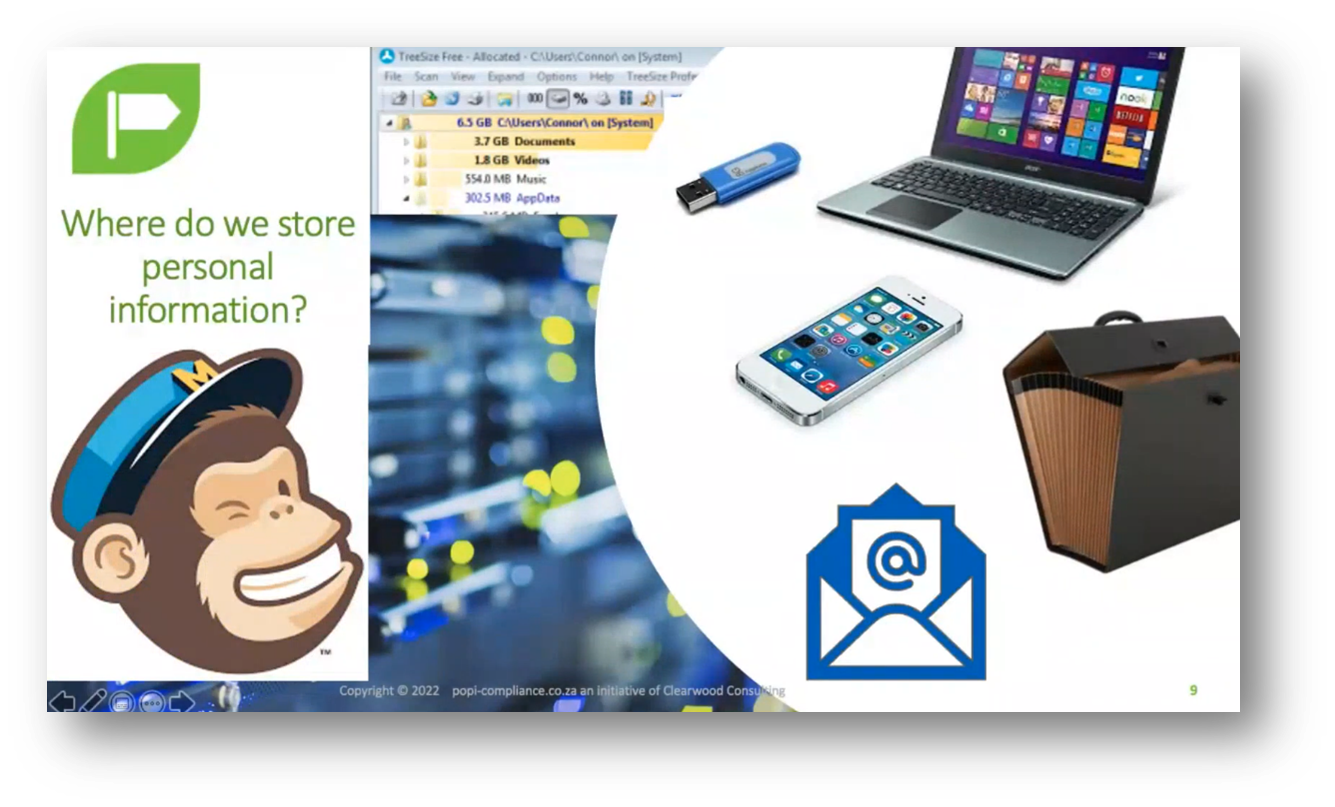
Prior authorisation may be necessary when storing data in other countries. When sharing data, be cautious and aware of the responsibilities under privacy laws, such as the Protection of Personal Information Act (POPI). Unintentional or careless sharing may lead to privacy breaches. Data can be stored on various devices, including hard drives, cell phones, and external drives. It is essential to consider secure storage options to maintain data integrity and privacy.
Figure 2 Riskiest Risks Approach
Data Classification and Storage in the Business Environment
Many people opt to store their emails in Outlook PST files and folders. However, this can result in a cluttered and disorganised mess, making navigating through the different storage locations difficult. Establishing consistent data classification is important to manage and share data effectively. Doing so will help streamline the process and make finding and accessing the information you need easier.
Figure 3 "Where do we store personal information?"
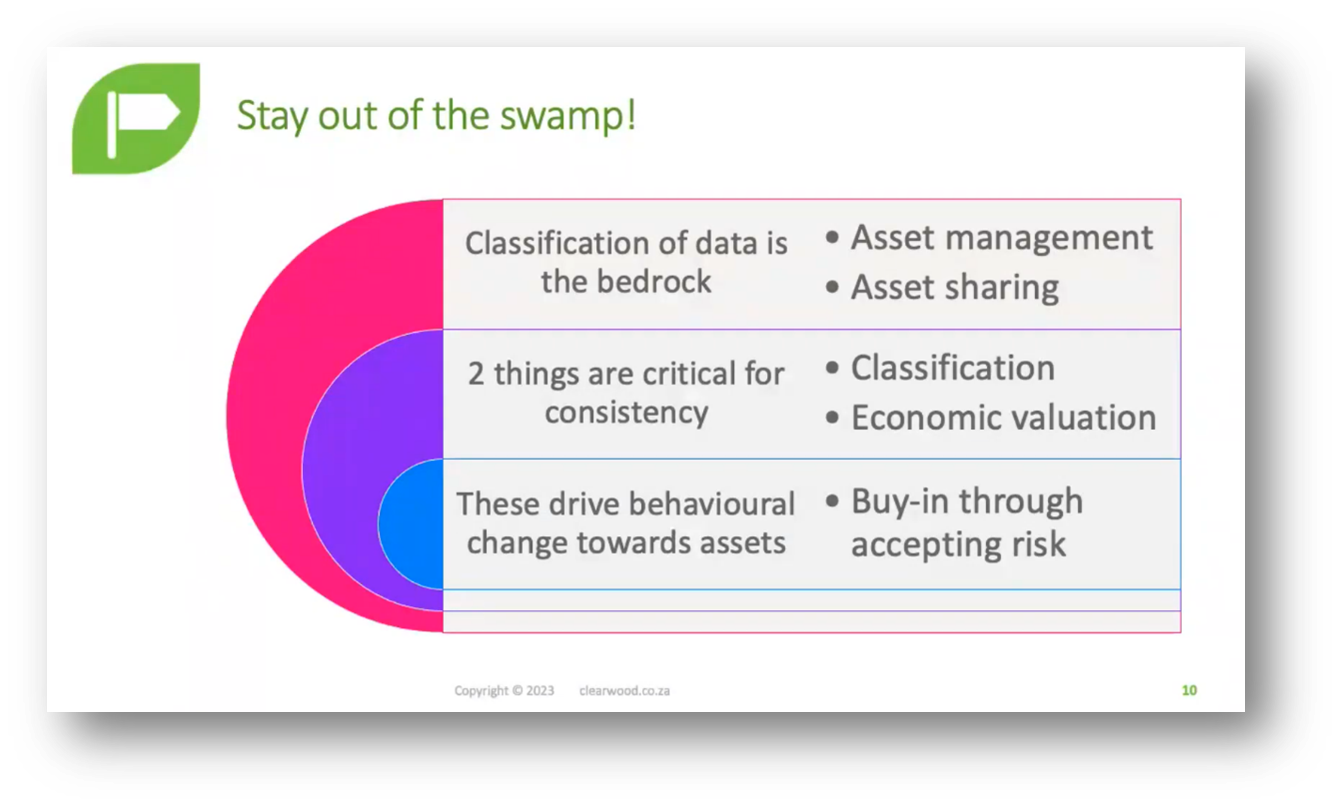
Figure 4 "Stay out of the swamp!"
Economic Valuation and Data Classification in Data Management
Economic valuation is important in prioritising Data Management and securing funding for data classification tools. Prioritising and managing high-risk and critical data helps gain business buy-in and ensure data storage security. Data assets vary in value; some data is more important than others.
Prioritising and classifying data is aided by data protection legislation and privacy measures—a systematic approach to data governance, identification, and understanding aids in effective Data Management. Economic valuation and data classification simplify the Data Management process and promote a more secure data storage system.
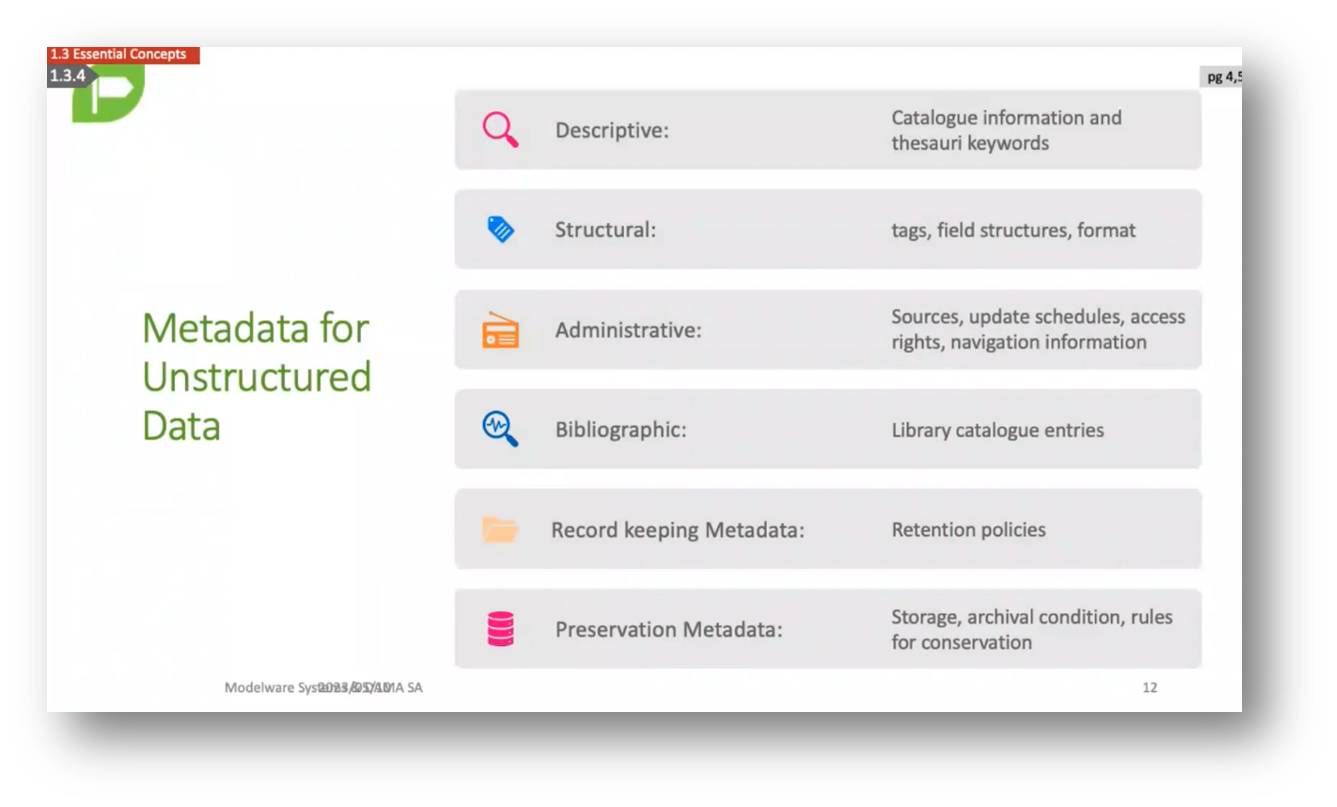
Metadata is crucial for proper data description and retention policies. Sufficient Metadata is required for structuring and tagging data for easy deletion. Mindful data storage in folders is crucial, considering retention policies. Different departments have varying perspectives on Metadata Management. Compliance officers may have difficulty aligning with structured Metadata approaches. Understanding the nature of the problem is essential for asking the right questions. Consensus on data storage and management is difficult due to diverse user perspectives.
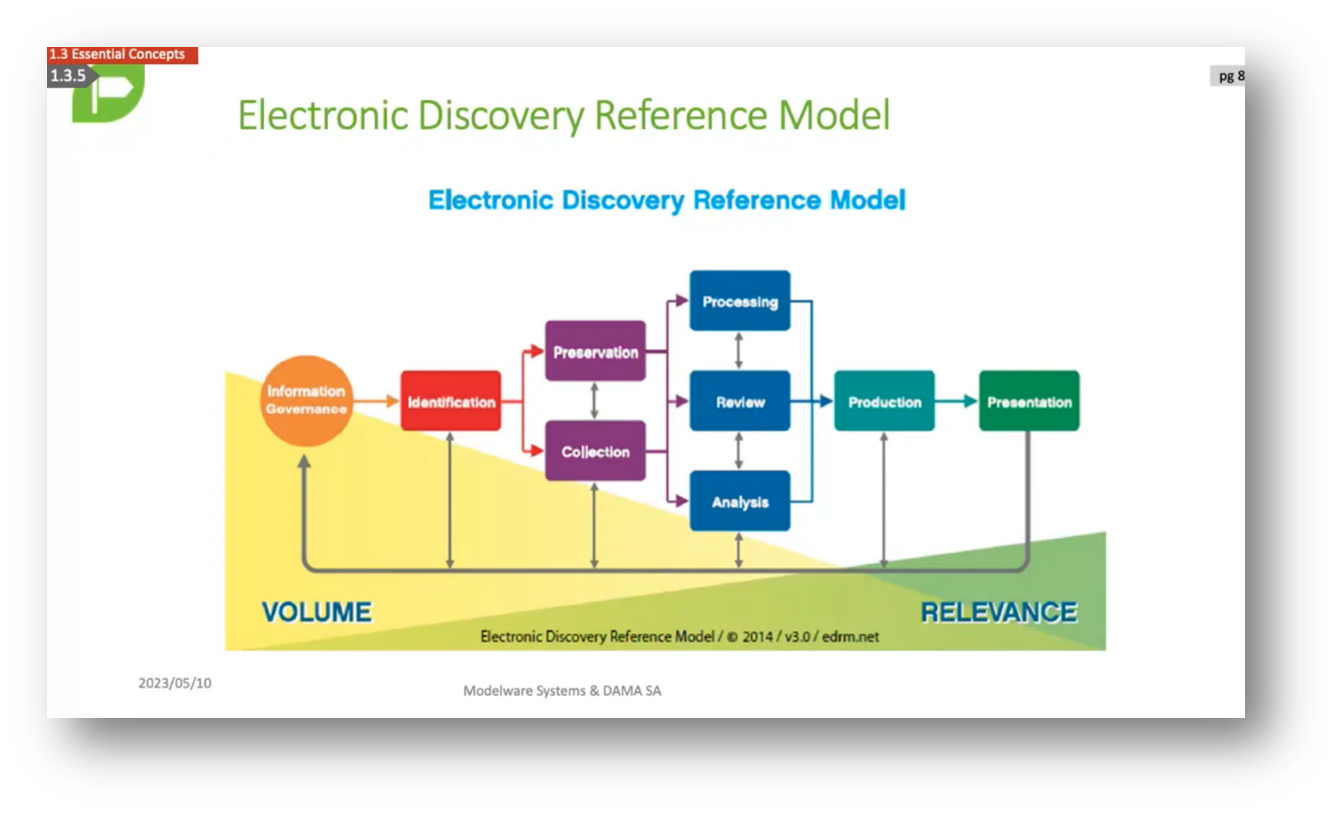
Figure 5 Electronic Discovery Reference Model
Figure 6 Metadata for Unstructured Data
Data Classification and the Need for a Multifaceted Taxonomy
A comprehensive and versatile taxonomy has been put forth to enhance the organisation and classification of data. This innovative approach facilitates the categorisation of data according to various hierarchical structures and the commonly used NIST system. This methodology can classify data as high-priority, medium-priority, or low-priority, depending on its criticality and significance.
Figure 7 "You can't use an old map to explore a new world."
Challenges of Classifying Data and Privacy in Information Security
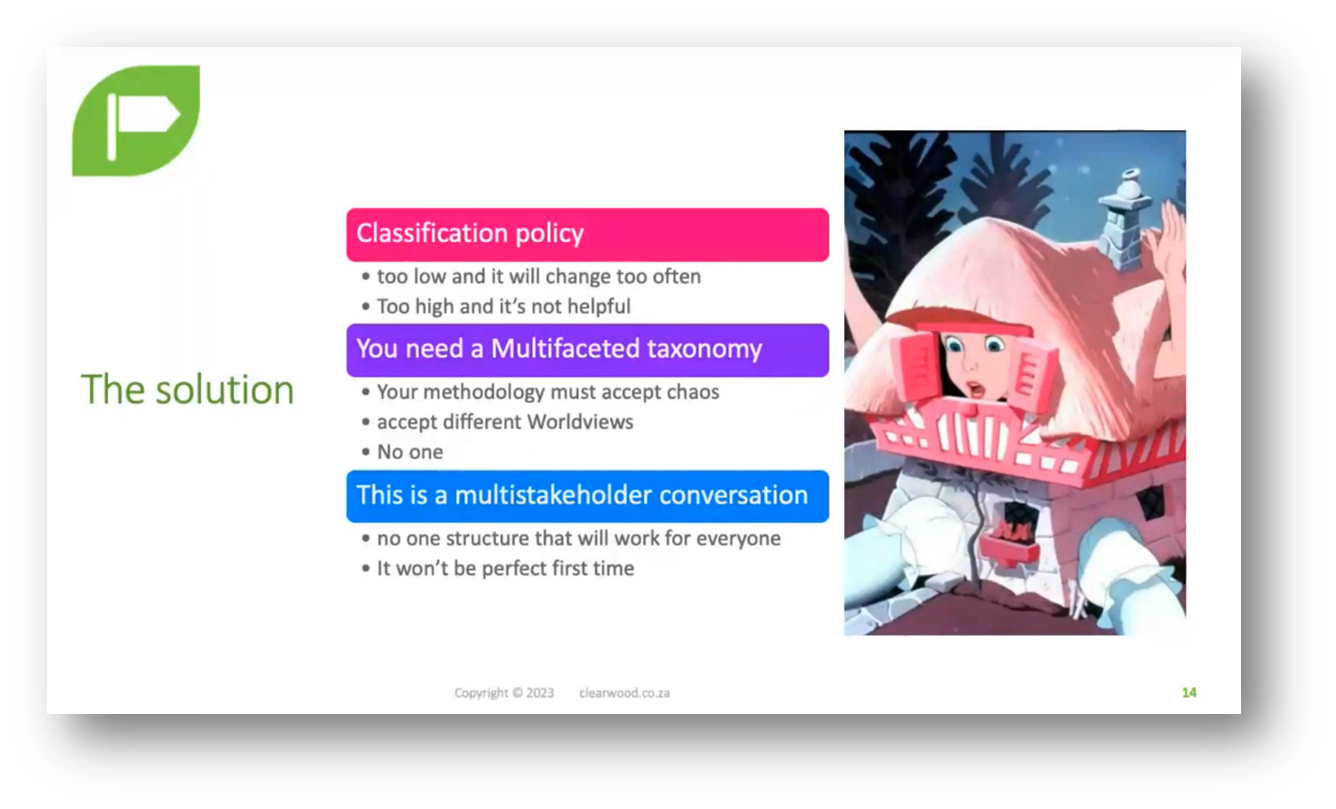
To effectively manage data and ensure privacy, it is essential to implement a comprehensive taxonomy capable of classifying information in a multifaceted manner. This will enable organisations to incorporate relevant privacy policies and safeguards, ensuring that sensitive data is handled responsibly and securely.
Figure 8 The Solution
Metadata and Clarification in Data Transfers and Cross-Border Privacy Issues
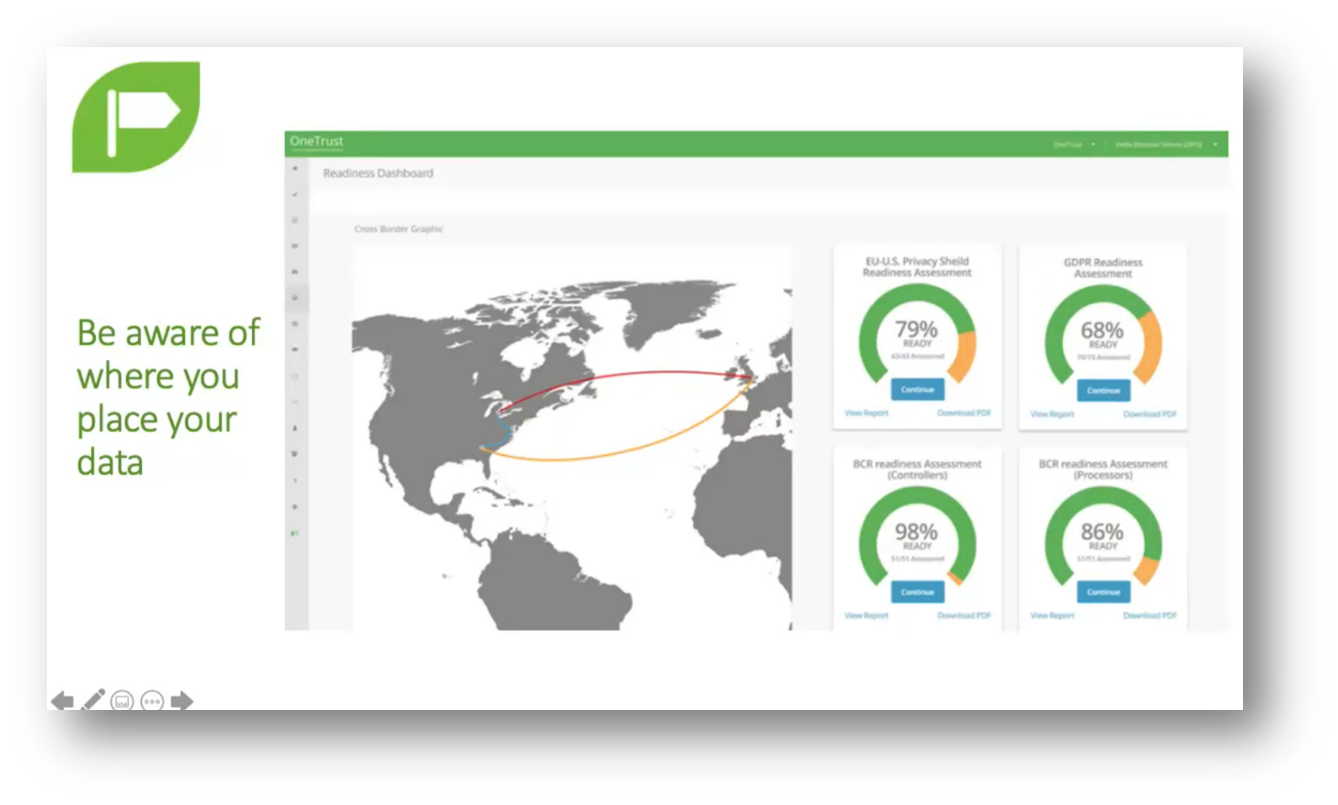
In the past, Data Management in SharePoint was disorganised and lacked proper cataloguing and classification, leading to difficulties in finding and accessing data. This can result in data becoming scattered and problematic, resembling a shared folder rather than an organised system. With increasing concern around cross-border data transfers, proper clarification and classification of data is crucial to avoid unintentional legal violations.
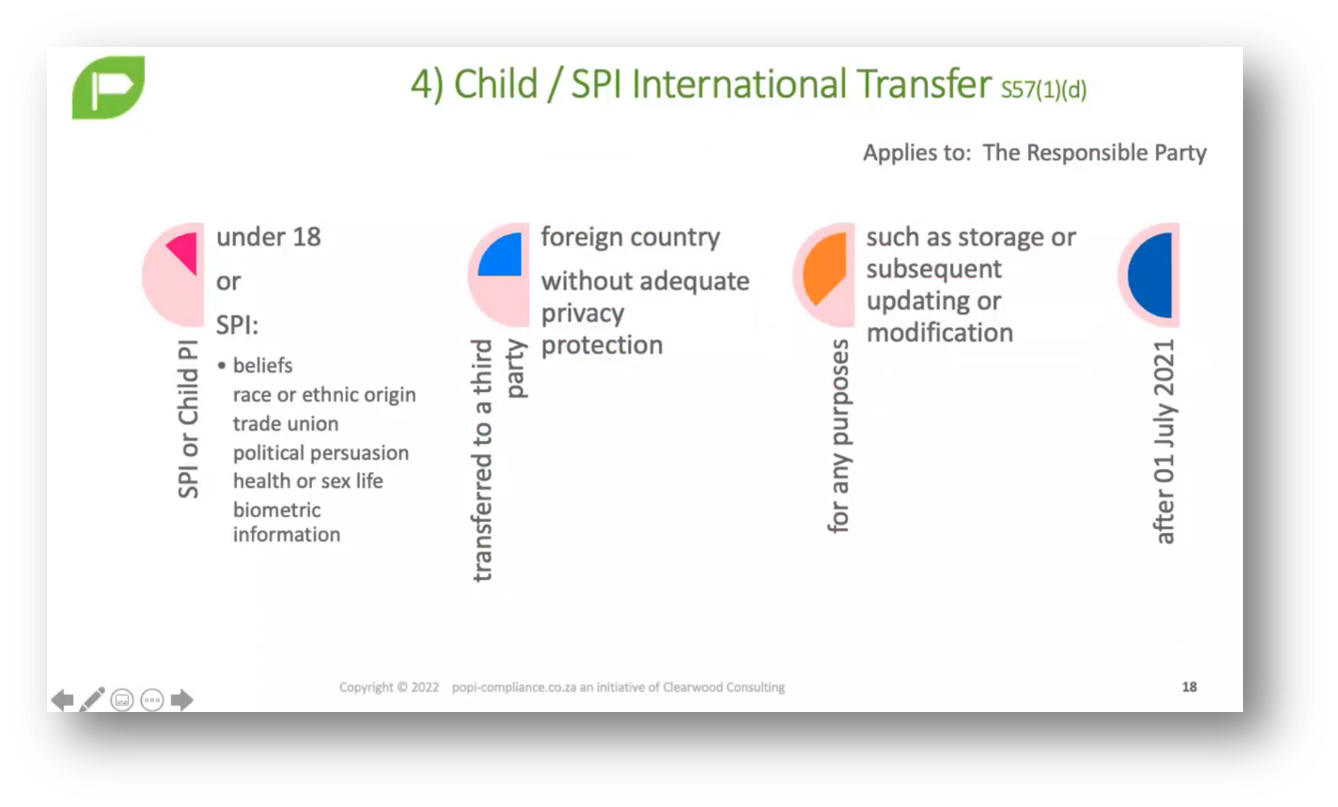
Cross-border transfers can create privacy and regulatory challenges. Failure to obtain prior authorisation for data transfers may lead to penalties, such as a 1 million Rand fine. The South African Protection of Personal Information Act (POPI) requires approval for handling specially classified personal information and data related to children.
Figure 9 Be Aware of Where you Place your Data
Figure 10 Prior Authorisation
Understanding Privacy Laws and Data Transfers
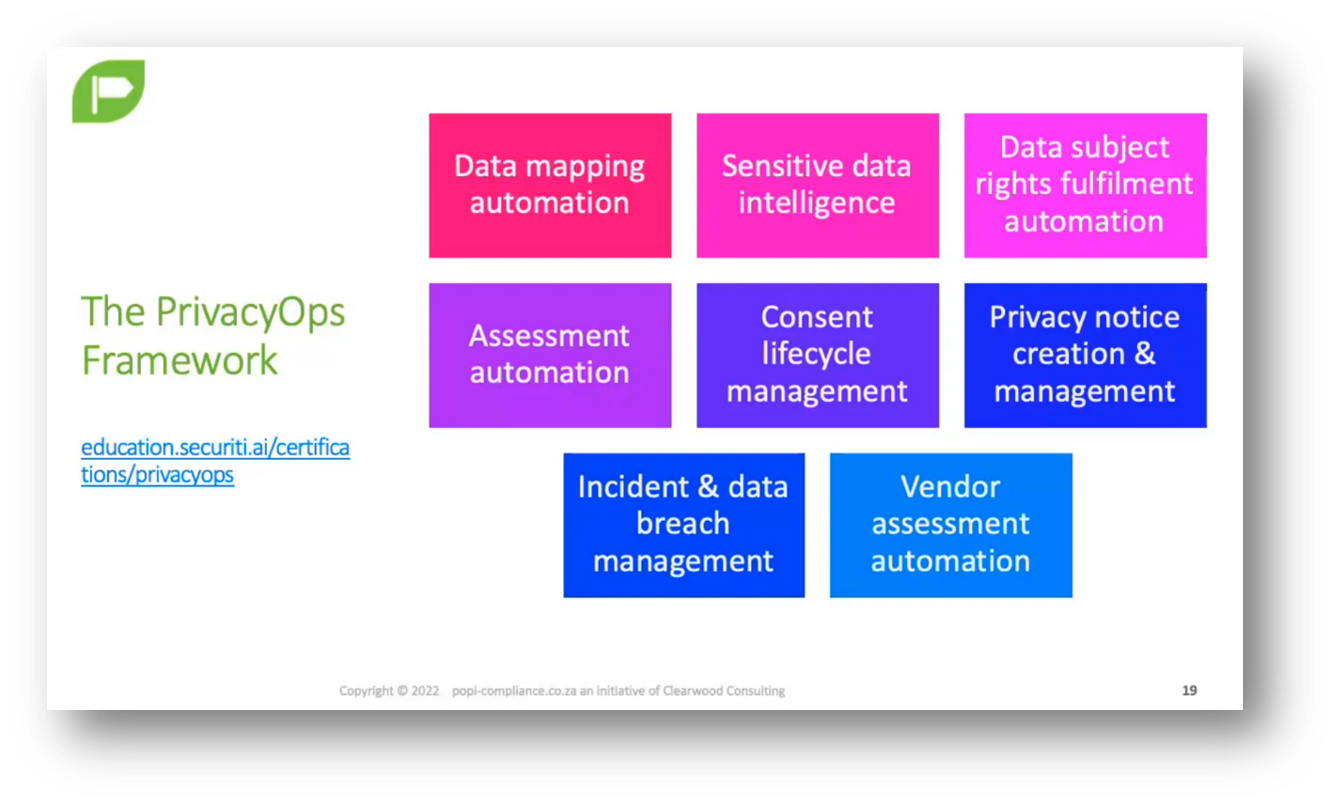
To ensure privacy compliance, it is crucial to understand what constitutes special personal information, create a corporate policy that outlines how privacy is managed and defines restricted data, obtain prior authorisation for handling restricted data, determine the responsible party, and give special attention to data about children and data that falls under the definition of restricted data. The policy should also outline which countries have sufficient safeguards for transferring data to foreign countries without adequate privacy protection. Privacy Ops training resources can provide helpful insights, and sensitive data intelligence is essential to privacy operations.
Figure 11 Child/ SPI International Transfer
Figure 12 The PrivacyOps Framework
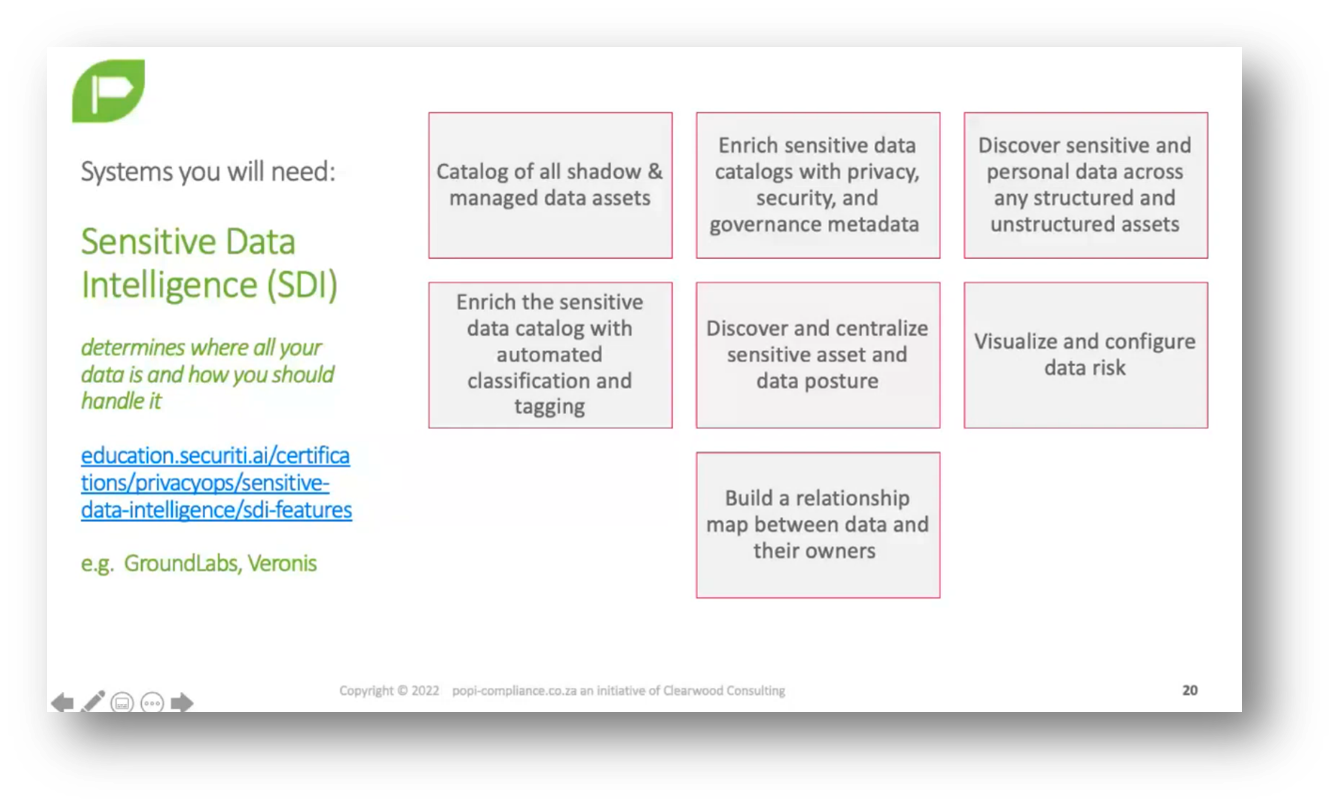
Sensitive Data and Vendor Assessment
It is crucial to understand where third-party vendors store and process sensitive data. Cataloguing all shadow and managed data assets, including unexpected areas like SurveyMonkey, is essential. Sensitive data intelligence enhances privacy and security, providing valuable insights. Effective discovery tools like Ground Labs and Verona can identify unstructured information through networks. Several tools and guidelines are available to navigate the complexities of privacy. Implementing a process that flags compliance and risks to the appropriate team at the right time is necessary.
Figure 13 Sensitive Data Intelligence (SDI)
Figure 14 When Should we Worry about Prior Authorisation?
Change Control and Privacy Design in Business Strategy
The need for change controls applies to business changes, not just technical ones. Compliance should assess if prior authorisation or consultation is required. Corporate policies must include change control for managing privacy, restricted data, processing, and data transfer. Incorporating privacy design into business strategy is more cost-effective from the beginning. Storing sensitive data in non-compliant locations can be problematic.
Zoho CRM's data storage issue and the importance of corporate policies
Zoho had to relocate data storage for new customers due to GDPR, causing inconvenience for existing ones. It's important for Salesforce users to know their data hosting to avoid similar issues. Data stewards should communicate decisions and enforce compliance review for data-related choices. Different data domains may have different regulations, requiring impact assessments. Classifying risks can help prioritise data security concerns.
Compliance in Privacy Protection
Privacy protection can be complex in a business; not everyone needs to be an expert. Instead, red flags should be reported to the compliance department for assessment. The compliance function is usually carried out by data stewards or information records management, or a risk and compliance head in a finance business.
If there is no designated compliance function, forming a privacy committee at the board level is recommended. In some companies, the Chief Information Security Officer (CISO) or the CFO may handle privacy compliance due to their authority and risk management expertise. The compliance function is separate from its methodology, framework, and capabilities. Note: The industry and availability of a designated function determine the approach to privacy compliance.
Data Privacy Compliance and the Role of Data Privacy Officers
Many individuals struggle with company privacy compliance and rely on the wrong person, such as an IT manager, to handle it. Privacy compliance is frequently postponed due to organisational factors. Some countries, like Botswana and Rwanda, are currently implementing their privacy legislation and experiencing a rush to ensure compliance. Similar situations have occurred, such as in South Africa in 2017. Data Privacy roles, such as Data Protection Officers (DPOs), are uncommon in all organisations. However, some legislations mandate the appointment of a DPO, like GDPR, while others allow outsourcing of the role.
Privacy Operations and Qualifications for DPOs
Qualified professionals in privacy operations are needed to comply with EU GDPR. The specific certifications or qualifications for a Data Protection Officer (DPO) are undefined. Understanding compliance risk is crucial for a DPO, who must also comprehend data and information governance.
Merging the worlds of data protection and information governance is vital. Caroline joined the Compliance Institute of South Africa to understand the compliance aspect of privacy, and she is also studying cybersecurity to understand the data protection aspect. The role of a DPO in POPI (Protection of Personal Information Act) is different from that of an Information Officer, who is a compliance officer rather than a Chief Information Officer (CIO).
The Role of the Information Officer and DPOs in GDPR
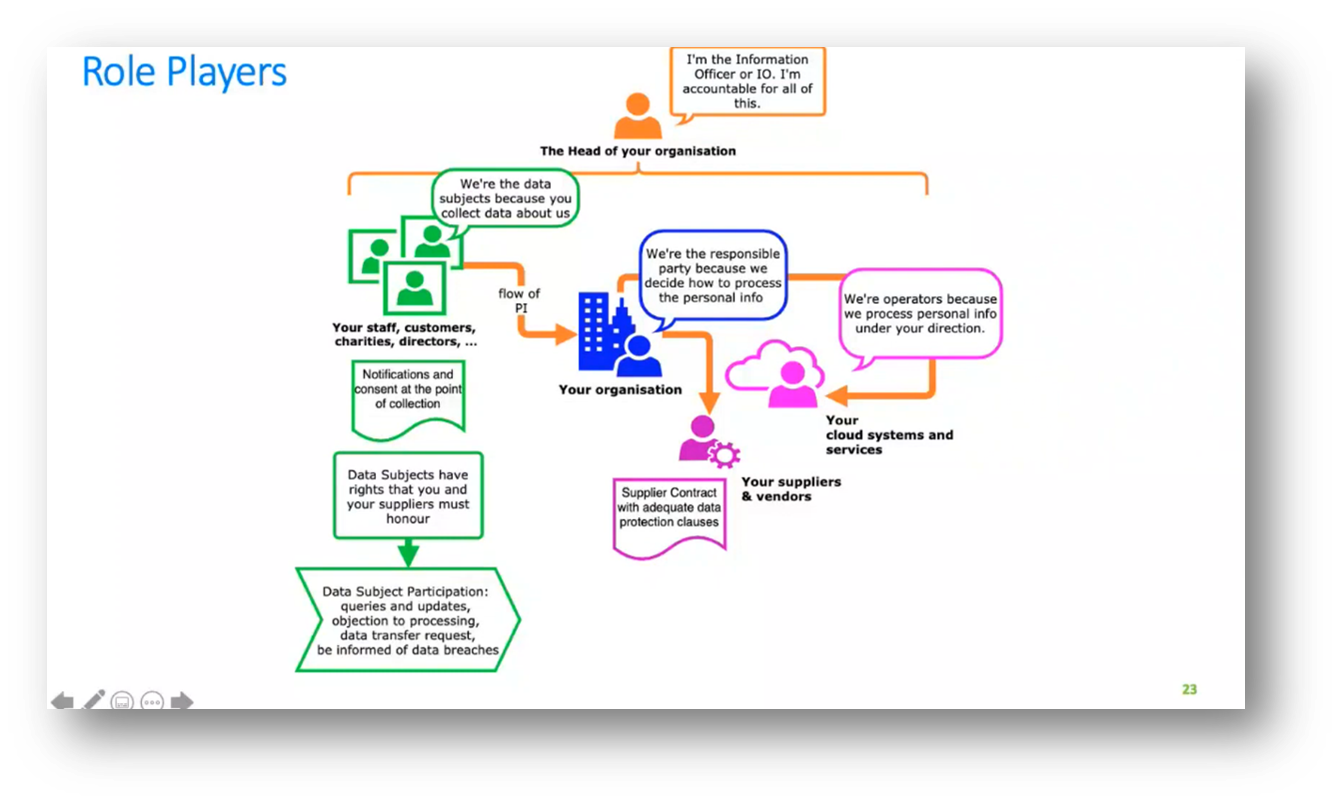
The head of an organisation is accountable to the regulator, even if they delegate responsibilities to others. In GDPR, the CEO, managing director, or sole proprietor is the DPO responsible for communicating with the regulator in case of a data breach. During a data breach, it is crucial to have a capable individual, such as the head of the risk or CFO, communicating with the regulator to understand legal accountability, language, timing, and politics.
POPI simplifies the process of nominating a person based on the organisation type. Organisations collecting data from individuals are responsible for notifying them, obtaining consent, respecting their rights, and allowing participation. Data subjects have the right to request information, object to data collection, request data deletion, and receive their data in a specific format. The responsible party and information officer are accountable for any data breaches or unlawful processing, even if caused by third-party breaches.
Figure 15 Role Players
GDPR Compliance and Data Sharing Best Practices
As a professional, you are accountable for ensuring your subcontracted suppliers comply with GDPR. If a supplier changes their subcontracted supplier, they must inform the controller (the responsible party). Cloud service providers offering software as a service must obtain permission from all customers before changing their suppliers.
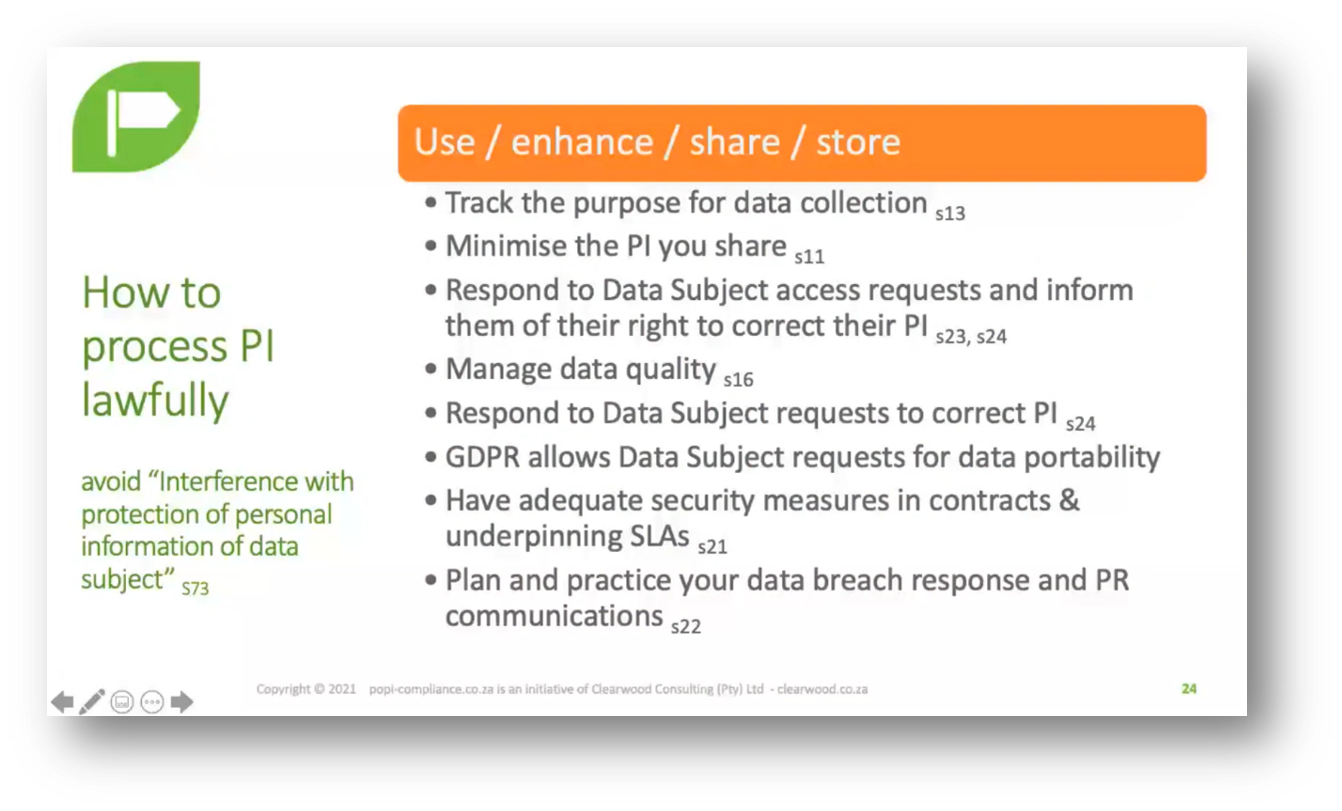
GDPR requires data processors to avoid interfering with protecting personal information while processing, enhancing, sharing, and storing data. GDPR emphasises checking the purpose of data collection and minimising data sharing. Only share necessary information with service providers and restrict access to specific data based on the tasks required. Data controllers must respond promptly to data subject access requests. Before providing the requested data, controllers must verify the data subject's identity.
Figure 16 How to Process PI Lawfully
Privacy Obligations and Data Sharing
Data Privacy best practices include ensuring data access, portability, security measures in contracts, and verifying the privacy protections of cloud service providers. Adopt frameworks like OWASP and international standards to protect personal information and assess and address top security risks when sharing data through APIs. The top 10 lists help highlight internationally accepted security risks and protect against compromises.
Figure 17 Unauthorised Access at All Levels
Data Privacy Recommendations
Caroline closes the webinar by stressing the importance of organised data storage. She compares disorganisation to a "swamp" of irrelevant information. Cross-border data transfer should be cautious, especially with sensitive personal information or data about minors. Understanding the responsibility of sharing data and its potential consequences or mishandling is vital.
If you would like to join the discussion, please visit our community platform, the Data Professional Expedition.
Additionally, if you would like to be a guest speaker on a future webinar, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!