How ISO27001 Should Integrate with Data Management & Data Protection Purposes with Caroline Mouton
Executive Details
This webinar outlines key aspects of Data Privacy and Information Security, emphasising the significance of legislation like the POPIA and GDPR in shaping organisational practices. It highlights the importance of ISO standards and robust risk management frameworks in establishing effective security policies, conducting security checks as per Section 19 of the Digital Privacy Act, and implementing controls as outlined in ANNEX A.
Caroline Mouton addresses the critical role of auditing, particularly in aligning with PCI-DSS and ISO standards, to enhance Data Security and compliance within cybersecurity initiatives. Additionally, she addresses cyber insurance as being considered vital for mitigating risks and ensuring a secure Controls Framework in today’s technology-driven environment.
Webinar Details
Title: How ISO27001 Should Integrate with Data Management & Data Protection Purposes
Date: 30 October 2024
Presenter: Caroline Mouton
Meetup Group: DAMA SA User Group
Write-up Author: Howard Diesel
Contents
Data Privacy, ISO Standards, and Technological Updates
Understanding the POPIA Privacy Legislation and Its Impact
Information Security and Privacy in the Context of GDPR
Section 19 of the Digital Privacy Act: The Requirements of Security Checks
Risk Management: Information Security Frameworks
Risk Management and Information Classification
ISO 27000: Privacy and Security Management
Risk Management: Information Security Policies
The Importance of Controls in Information Security
Data Security and Auditing: PCI-DSS and ISO 27000
Understanding Audit Recommendations and Risk Management
The Role of ANNEX A Controls in Information Security Management
Risk Management in Information Security
ISMS Process and Compliance in Cybersecurity
ISO Standards and Risk Management in Companies
Cyber Insurance and Secure Controls Framework
Data Privacy, ISO Standards, and Technological Updates
Caroline Mouton opens the webinar on Data Privacy and ISO standards. Howard highlights the growing popularity of ISO 27000, particularly in Saudi Arabia, where corporate demand is increasing as part of due diligence practices by investors. Caroline notes the contrast with the United States, where SOC 2 is more prevalent, emphasising the regional differences in standards. An attendee from Saudi Arabia, confirmed his involvement with ISO 27000 training.
Caroline also introduced her initiative, KnowWhatSkills.tech, under the consulting firm Clearwood, aimed at sharing knowledge and updates on technology. Additionally, she mentioned the release of SFIA version nine, which modernises roles by incorporating more AI roles and expanding marketing profiles, resulting in a more accessible and organised website. Caroline expressed excitement over the enhancements and acknowledged the work required to update relevant badges.
Figure 1 Title Slide
Figure 2 Getting in contact with Caroline Mouton
Figure 3 Speakers Experience
Figure 4 Declaration
Understanding the POPIA Privacy Legislation and Its Impact
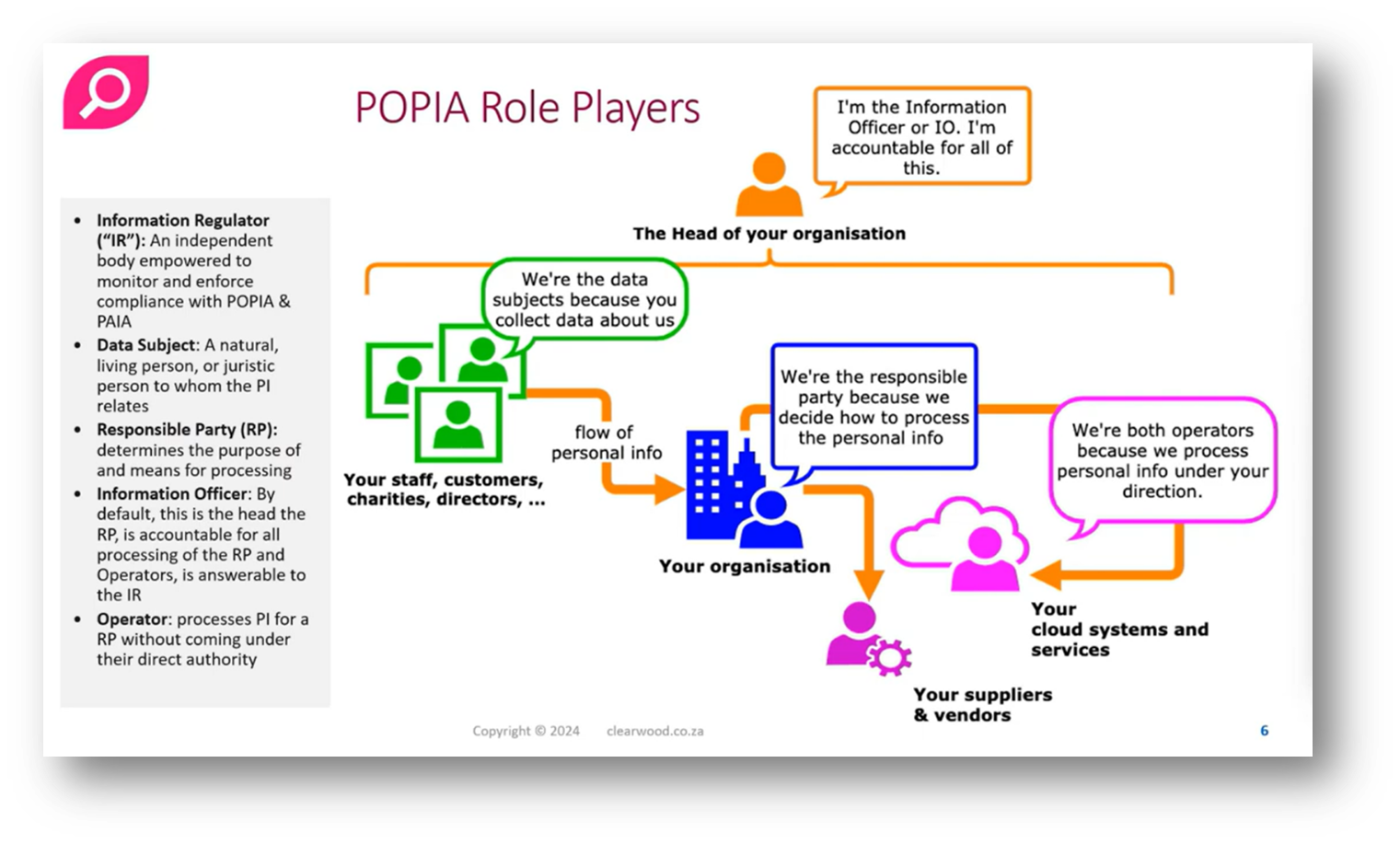
POPIA, or the Protection of Personal Information Act, is South Africa's privacy legislation closely aligned with global privacy laws stemming from OECD guidelines. Key elements include the roles of data subjects, responsible parties, and operators; the latter encompasses anyone handling personal information on behalf of the responsible party.
The Information Regulator serves as the supervisory authority, similar to entities in the EU and other regions, while the head of the organisation is designated as the information officer, holding full accountability for data management. Unlike the GDPR, where a Data Privacy Officer (DPO) is not mandatory, POPI requires this role to be explicitly named, even for sole proprietors, reflecting the stringent compliance framework in South Africa's privacy legislation.
Figure 5 "POPI-101"
Figure 6 POPIA Role Players
Information Security and Privacy in the Context of GDPR
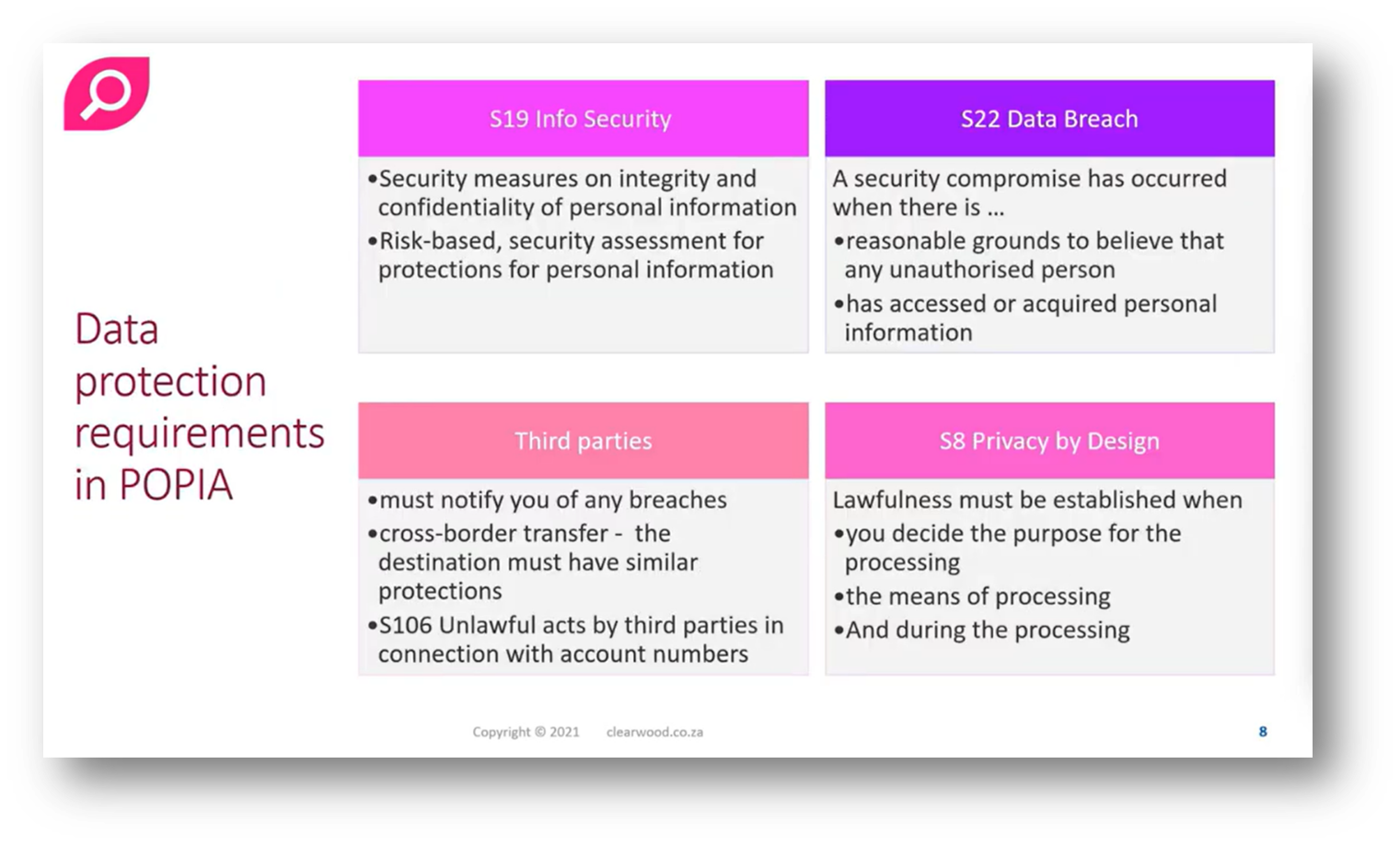
A discussion starts on Information Security and encompasses several key areas, primarily highlighted in Section 19, which delves into the management of data breaches as part of incident management. Additionally, it addresses third-party management, including supplier and vendor risk management, emphasising the necessity of contracts with these partners. While Section 8 alludes to the concept of privacy by design, it is not explicitly named in the POPIA (Protection of Personal Information Act); however, GDPR (General Data Protection Regulation) clearly defines terms like privacy by design and security by design, as well as privacy by default and security by default. Ultimately, both regulations underscore the importance of integrating privacy and security principles into the design framework.
Figure 7 "What does POPIA want?"
Figure 8 Data Protection Requirements in POPIA
Section 19 of the Digital Privacy Act: The Requirements of Security Checks
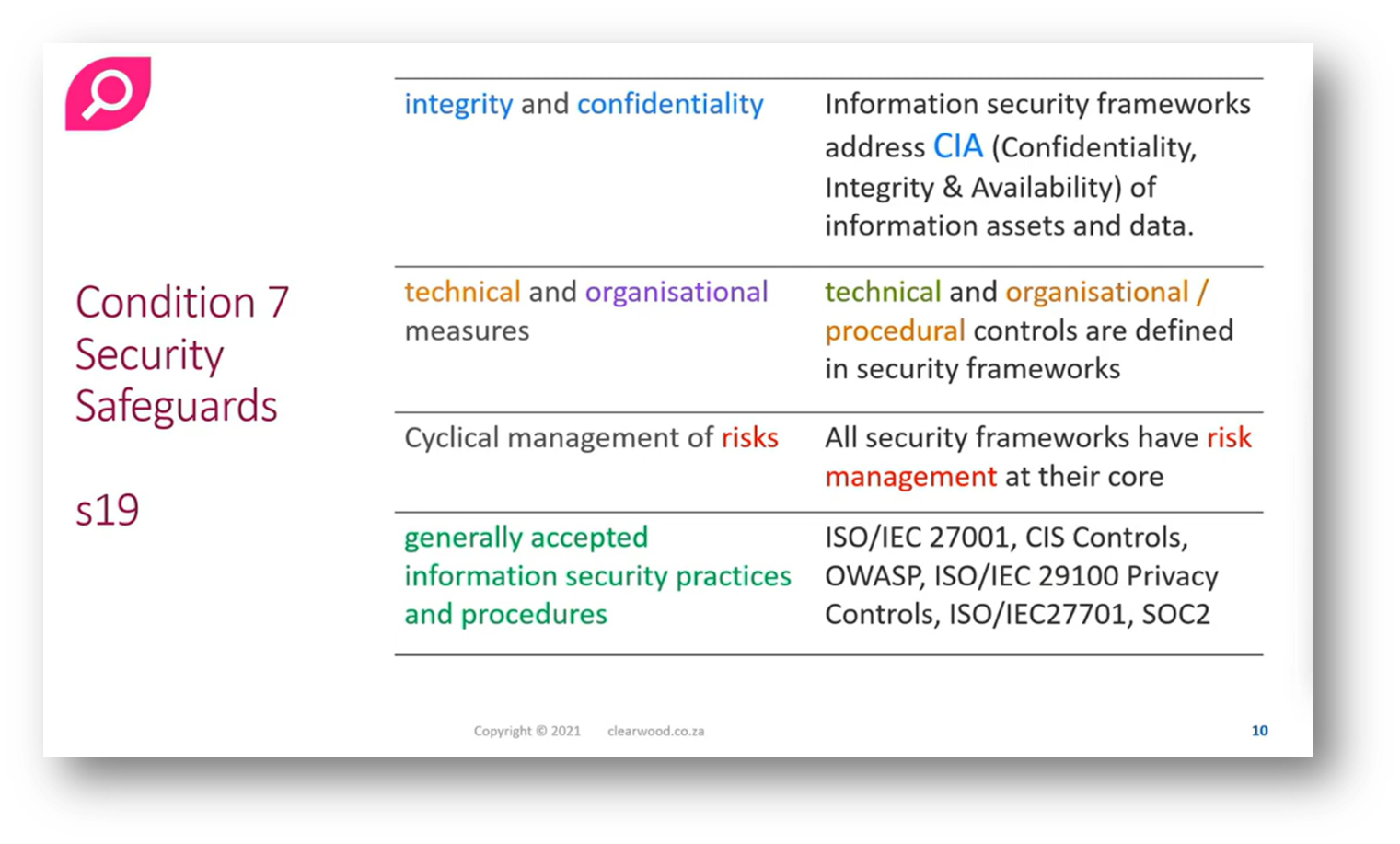
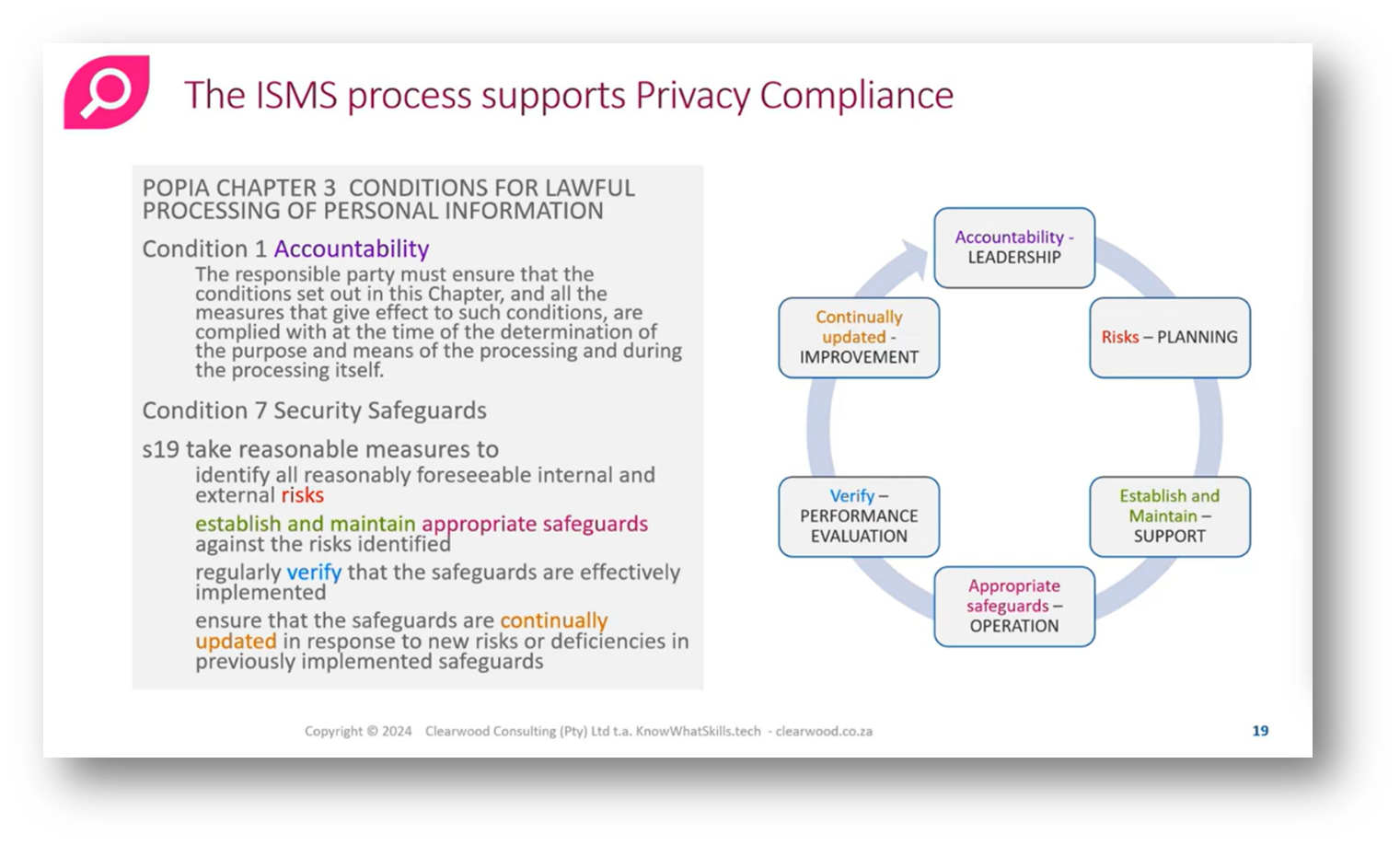
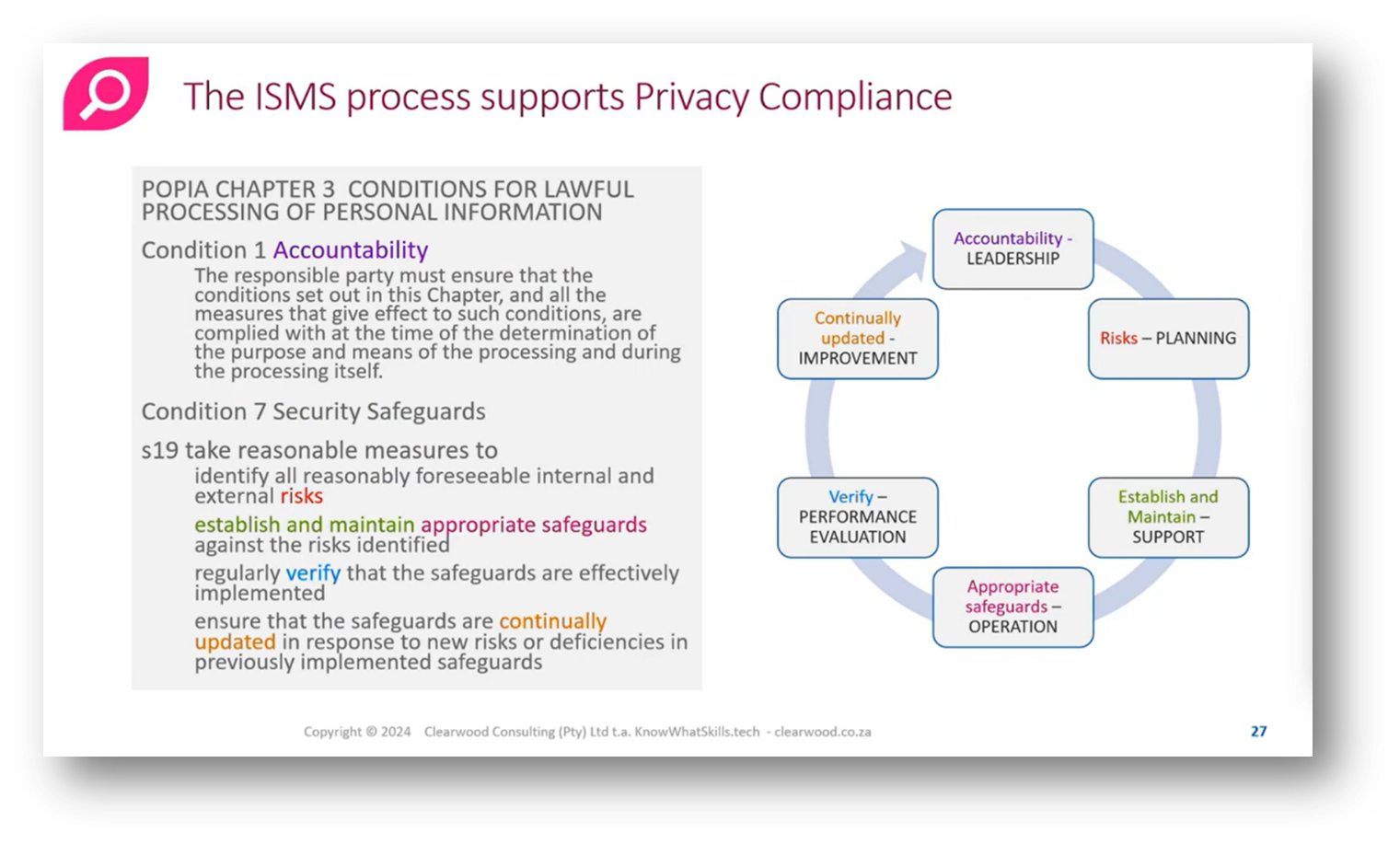
The Condition 7 security guards outlined in Section 19 emphasise the need for reasonable technical and organisational measures to safeguard the integrity and confidentiality of personal information. This includes preventing loss, damage, unauthorised access, and unlawful processing of data. Organisations are required to identify foreseeable risks, establish appropriate safeguards, regularly verify their effectiveness, and ensure these measures are updated in response to emerging threats or changes. Additionally, compliance with relevant laws and generally accepted Information Security practices is mandatory, particularly in highly regulated industries like finance and healthcare. Importantly, if another law offers greater protection than the Protection of Personal Information Act (POPI), that law takes precedence; otherwise, POPI applies. Organisations must avoid creating their own security definitions without adherence to established standards.
Figure 9 Condition 7 Security Safeguards
Figure 10 Condition 7 Security Safeguards Part Two
Risk Management: Information Security Frameworks
Caroline explores the key elements of Information Security frameworks, focusing on the CIA triad—Confidentiality, Integrity, and Availability—while also incorporating safety for software. She highlights the importance of technical, organisational, and procedural controls as essential components of these frameworks. A central theme is the cyclical management of risk, which involves continuous assessment and adaptation to new challenges. Effective risk management is crucial and should be tailored to the organisation's technology stack, industry, and context. Additionally, while there is a wealth of accepted practices and procedures in Information Security, choosing the most suitable ones for a specific business is vital, with ISO 27000 often being a prominent and widely referenced standard.
Figure 11 Condition 7 Security Safeguards Part Three
Risk Management and Information Classification
The management of risks involves a cyclical process of classifying and monitoring various types of risks, particularly in highly regulated industries like finance. This includes critical risk data (CRD) and high-risk data, with a classification framework that may consist of up to 33 levels. Information classification requires labelling data as top secret or confidential, differentiating it from risk management. Effective risk management encompasses various obligations, including legal, contractual, reputational, and financial loss risks, as well as business continuity concerns. Organisations typically employ a risk management methodology to report to their boards, fulfilling governance requirements within the framework of Governance, Risk, and Compliance (GRC).
Applying information categorisation to dates, documents, and records enhances risk management and compliance by making it more efficient to label and handle personal information. The DMBOK outlines a risk classification process that categorises data into critical, high, and moderate risk categories. Various frameworks, such as ISO 27000 and the National Institute of Standards and Technology (NIST), stress the importance of classifying information and applying risk ratings, yet they do not define risks explicitly. Caroline emphasises the need for information management and security practices to align with an organisation's overarching risk management strategy.
Compliance officers play a vital role in integrating information management procedures with risk classification. Moreover, engaging with professional organisations, like the Risk Management Association of South Africa, can provide valuable insights into effective risk handling.
ISO 27000: Privacy and Security Management
ISO 27000 focuses on establishing a quality management system for Information Security, integrating a privacy management approach within its framework. This standard emphasises a cyclical process beginning with top-down leadership commitment, followed by planning, resource support, operational risk assessment and treatment, and performance evaluation.
Caroline moves on to highlight the importance of senior management's involvement in budgeting and strategy, as well as mandatory internal audits and management reviews, which are necessary to ensure ongoing effectiveness. Importantly, ISO 27000 advocates for robust controls over personal information, distinguishing its requirements from standard security practices, thereby creating a comprehensive model for managing Information Security and privacy effectively.
Figure 12 "An Introduction to ISO/IEC27001"
Figure 13 "Lifting the Lid - An Outline of the ISO/IEC27001 Requirements"
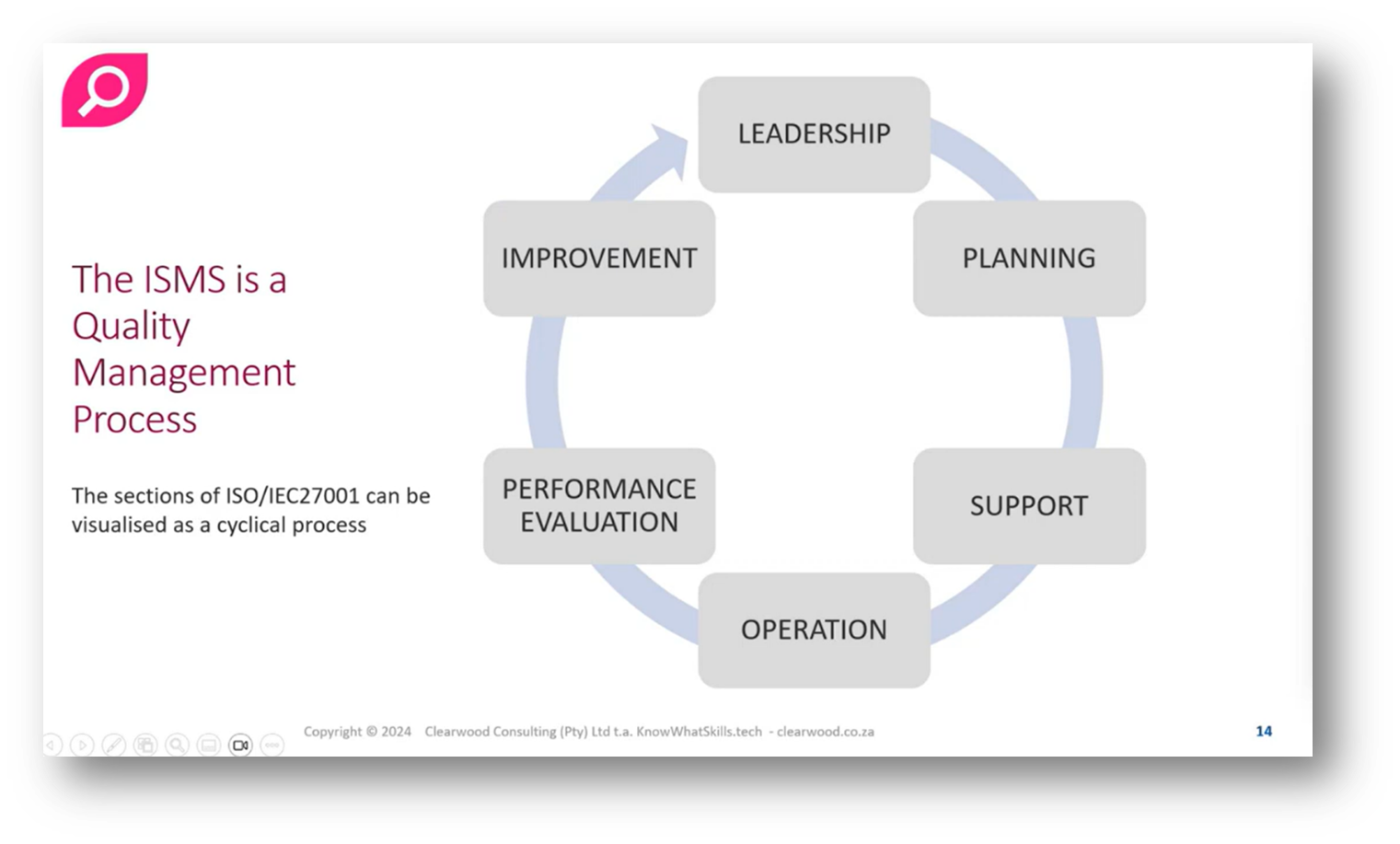
Figure 14 The ISMS is a Quality Management Process
Figure 15 ISO/IEC27001 Visualised as a Cyclical Process
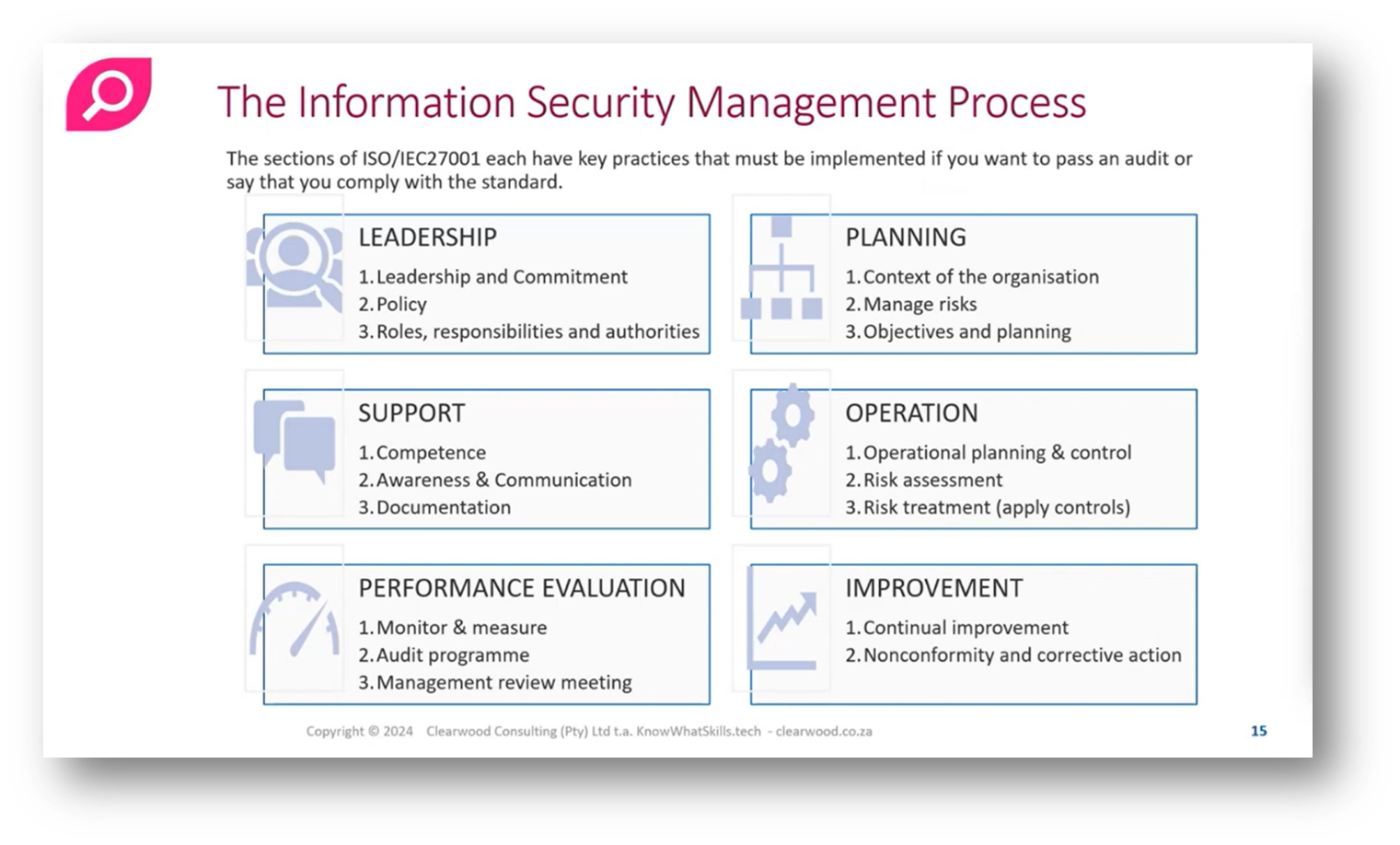
Risk Management: Information Security Policies
The key elements of effective leadership in Information Security Management are outlined with emphasis on the importance of establishing policies and commitments in the Information Security policy. Risk Management is integral to planning, supported by training, communication, and documentation. The operational aspect involves conducting risk assessments and applying controls as part of the risk treatment plan, followed by evaluation, auditing, management review, and continuous improvement, which form the foundation of an information management system.
The alignment between ISO 27001 and the Protection of Personal Information Act (POPIA) is highlighted, with accountability as a critical requirement and security safeguards requiring reasonable risk identification. Establishing and maintaining safeguards, represented by support functions, involves providing training and allocating resources, while the operational step entails implementing and monitoring these safeguards. Caroline then addresses the role of mitigation as part of the operational phase, where specific controls, such as firewall configurations and policies, are executed.
Figure 16 The Information Security Management Process
Figure 17 The ISMS Process Supports Privacy Compliance
The Importance of Controls in Information Security
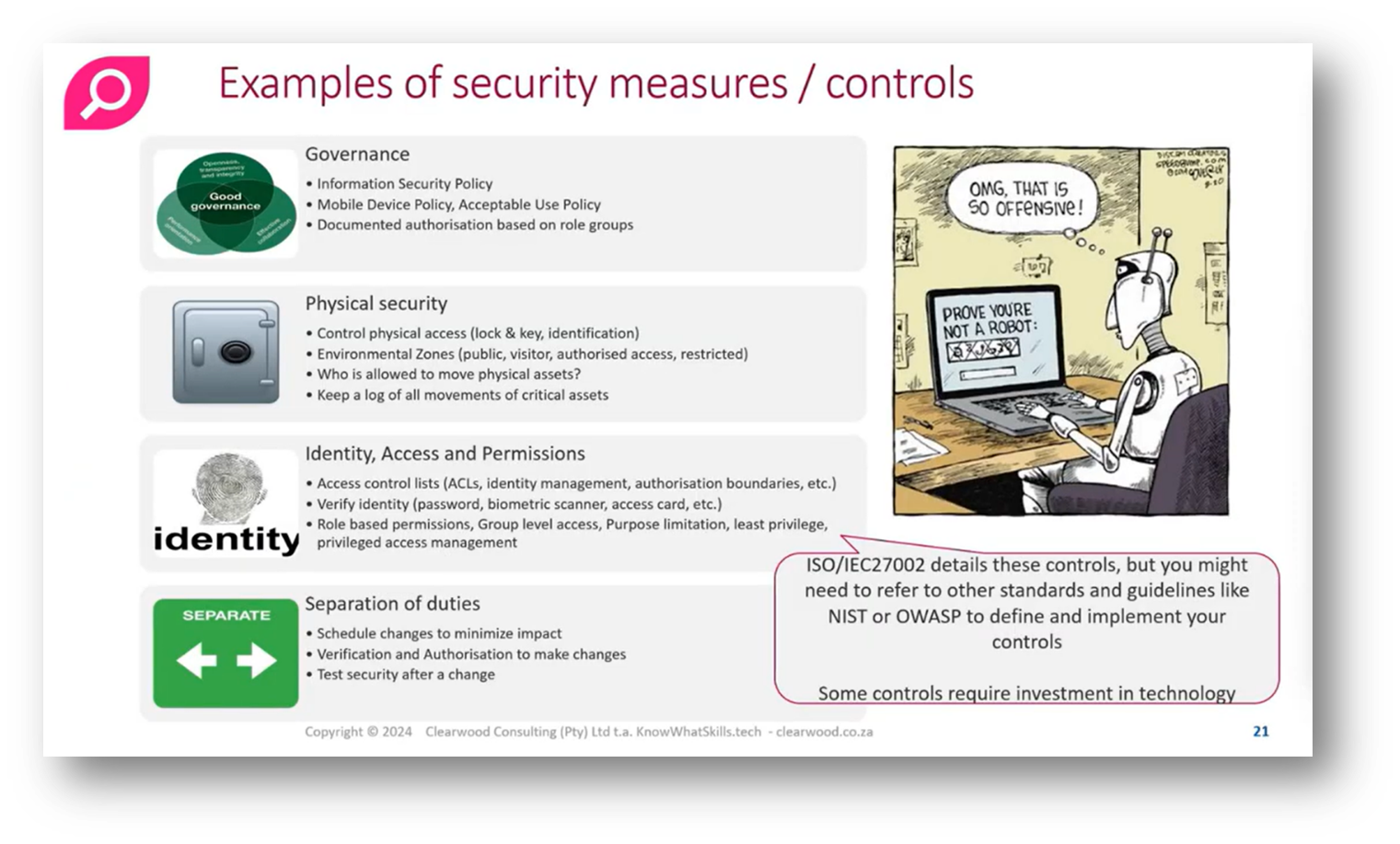
Caroline states that it is essential to clarify the concept of security measures or controls, which encompass a broad range of safeguards, including policies, procedures, and access controls. The terminology in Information Security can often be overwhelming, but understanding these controls is crucial for compliance, particularly when auditors and regulators require evidence of awareness training. Effective controls should be supplemented by a documented process, which includes tools like a RACI grid to define responsibilities and accountabilities, ensuring continuous improvement. Recognising the importance of these processes is vital as they often play a critical role in the overall effectiveness of security measures.
Figure 18 ANNEX A - Let's take a closer look at the controls
Figure 19 Examples of Security Measures/ Controls
Data Security and Auditing: PCI-DSS and ISO 27000
The Payment Card Industry Data Security Standard (PCI-DSS) provides a framework of controls for organisations handling credit card and payment information, emphasising the importance of regular auditing and monitoring of data access, both during and outside of working hours. Effective auditing is a crucial control mechanism that requires assigned responsibilities and consistent oversight rather than relying solely on annual compliance checks.
Organisations should conduct these audits frequently—ideally daily or weekly—to ensure the protection of financial information. This proactive approach aligns with incident management and event monitoring policies outlined in ISO 27000, demonstrating that compliance and genuine data protection efforts must work hand in hand. Utilising established PCI guidelines can also benefit the management of other sensitive data, such as bank account numbers.
A discussion starts on the implications of the POPI Act, particularly the 10 million Rand fine related to the management of financial and account numbers. Caroline emphasises the importance of frameworks like PCI-DSS for establishing effective controls over such sensitive information, including cryptocurrencies. She highlights that various Information Security frameworks exist, with ISO 27000 focusing more on management processes and oversight rather than specific auditable controls found in ISO 27001.
Auditors primarily look for evidence of compliance, such as the segregation of duties and defined Information Security roles, rather than dictating specific responsibilities. While risk assessments inform areas of focus for auditors, organisations have the flexibility to reference different frameworks if they suit their risk mitigation strategies, ensuring that the auditing process is standardised to avoid subjective interpretations.
Figure 20 ISO/IEC27001 ANNEX A
Understanding Audit Recommendations and Risk Management
When conducting an ISO audit, auditors may identify missing access controls and recommend improvements based on ISO 27001 and its supplementary document, ISO 27002, which provides in-depth guidance on Information Security policies. Organisations are encouraged to use these documents as a "cheat sheet," but it's essential to prioritise controls based on a thorough risk assessment, focusing on resource allocation and accepting certain risks while documenting them in an improvement plan. This approach not only helps in addressing audit findings but also supports compliance with regulations, such as POPIA, by providing a framework for justifying decisions and demonstrating how risks were evaluated. If a data breach occurs, companies can reference their risk assessments to explain prior decisions, acknowledge areas for improvement, and outline plans for mitigation.
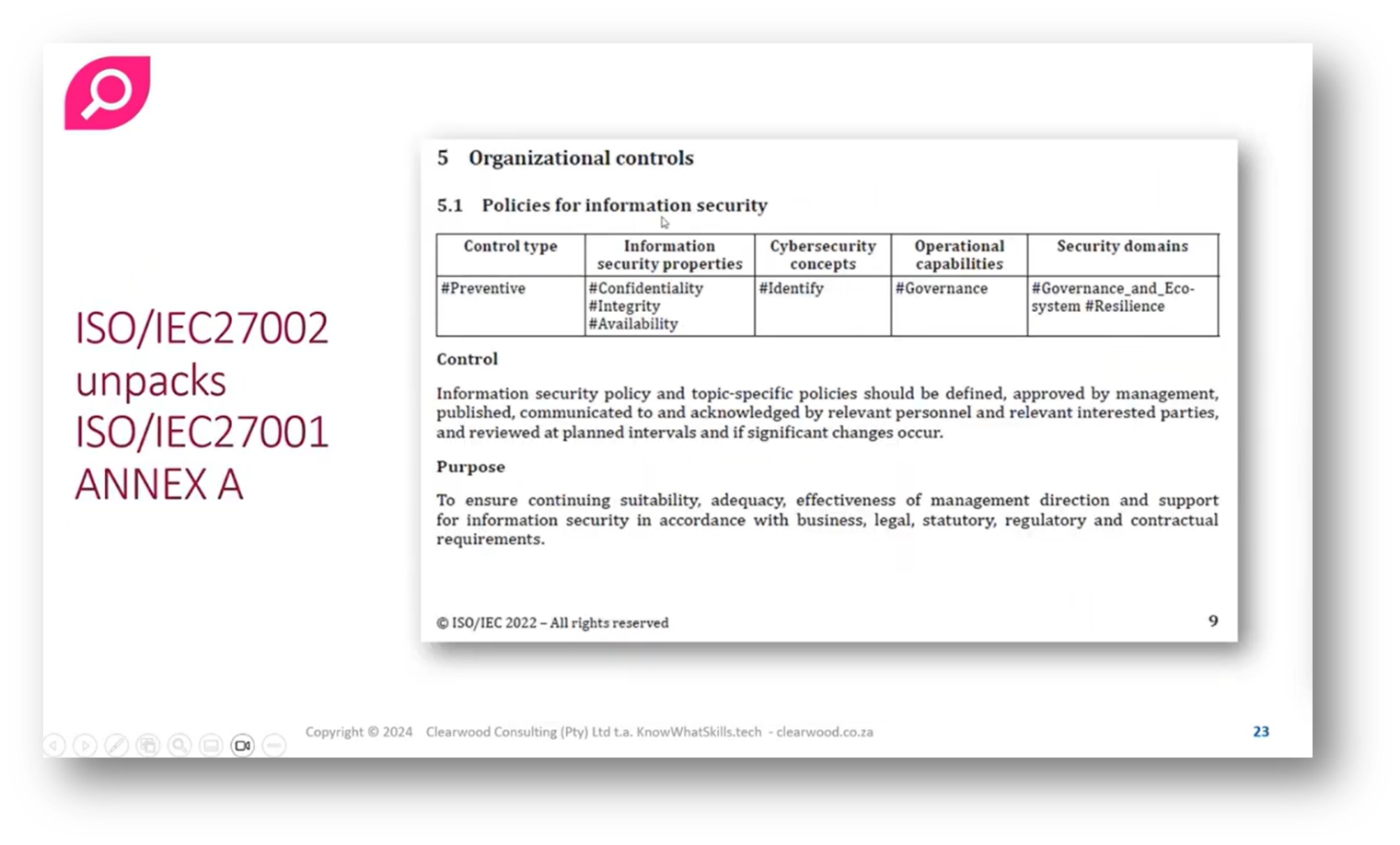
Figure 21 ISO/IEC27002 unpacks ISO/IEC27001 ANNEX A
The Role of ANNEX A Controls in Information Security Management
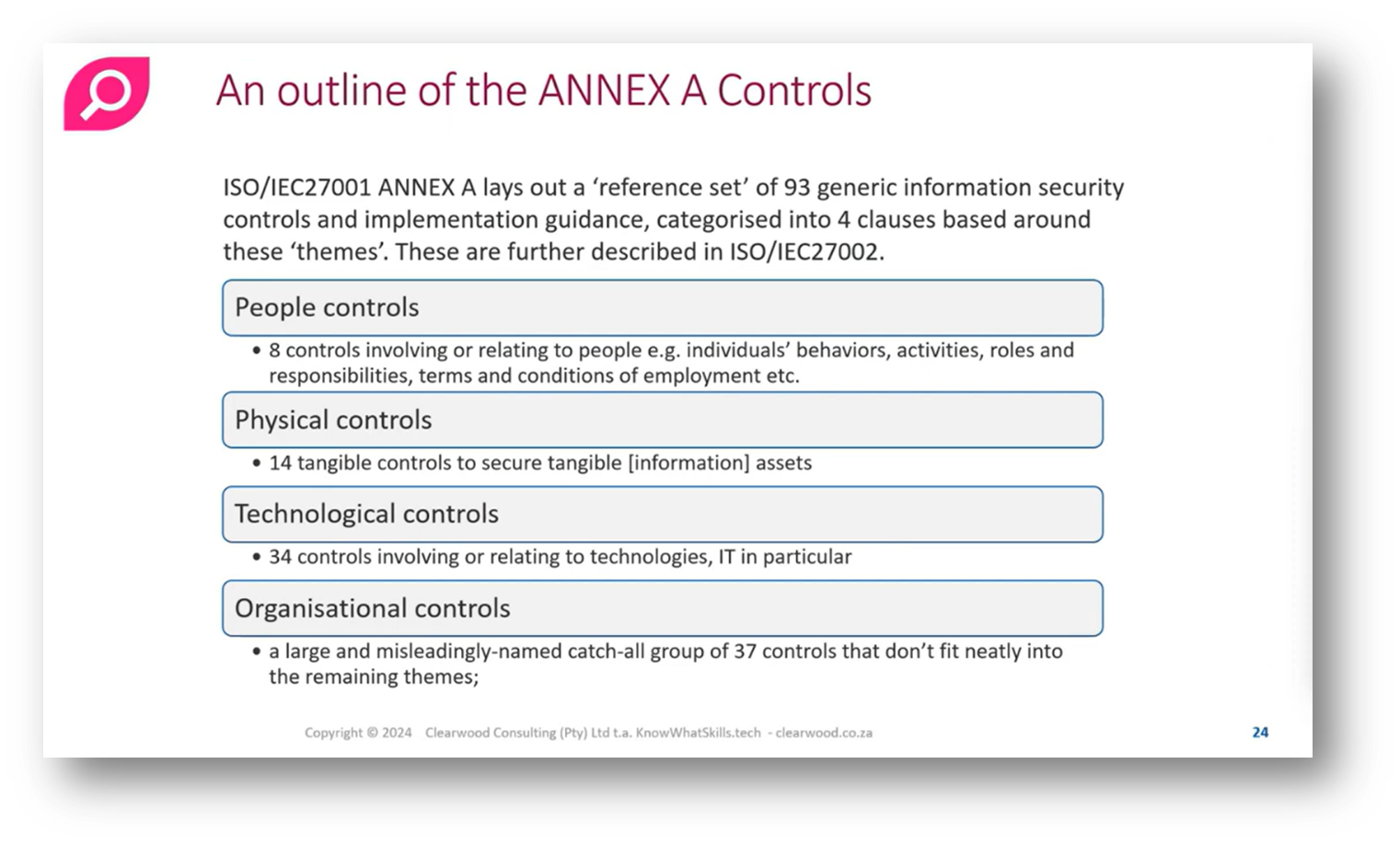
The ANNEX A controls are categorised into main areas: people controls, which focus on behaviours, roles, responsibilities, and employment terms; physical controls, pertaining to tangible aspects like technology disposal; and technology controls, which address IT systems and privacy enabling technologies (PETs), including privacy by design in software development. Organisational controls serve as a catch-all for anything not neatly fitting into other categories, such as access control.
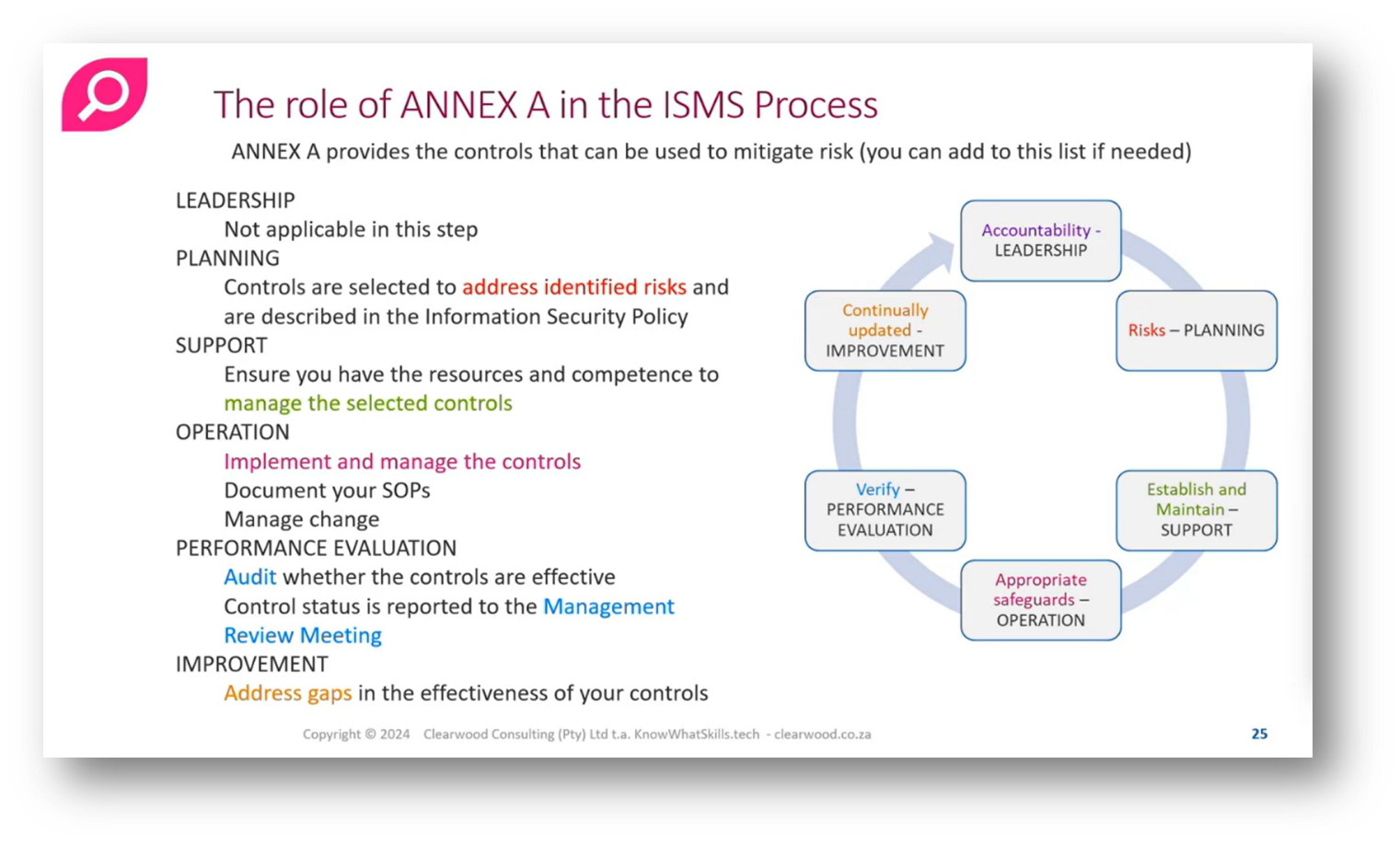
In the context of an Information Security Management System (ISMS), leadership primarily concerns itself with risk assessment rather than the specific nature of controls. During the planning phase, organisations select controls to mitigate identified risks, followed by an implementation phase where necessary tools, such as firewalls, are acquired, staff are trained, and responsibilities like log monitoring and separation of duties are established to enhance security and prevent unauthorised access.
Figure 22 An Outline of the ANNEX A Controls
Risk Management in Information Security
In the operational phase of Risk Management, organisations implement and manage controls, document standard operating procedures, and oversee change authorisation to ensure effective monitoring and security; this includes conducting audits, such as physical audits of firewalls, to detect unauthorised access. Performance evaluations assess whether the controls are successful in mitigating risks, requiring regular management reviews with key stakeholders, including the IT manager and CFO, to examine if the initial risk plans are being met.
It's crucial to conduct internal audits by impartial individuals and address any gaps found, such as unauthorised changes to security measures. Understanding inherent and residual risks is essential for communicating effectively with executives and stakeholders about risk tolerance and resource allocation, ensuring security measures align with organisational priorities without overspending on areas deemed less critical.
Effective risk management in organisations involves aligning various risk assessment methodologies across departments, such as privacy compliance, Information Security, and marketing. Different teams often use different metrics, like one trust’s risk assessments and ISO 27,000 standards, to categorise risks as high, medium, or low, leading to potential misunderstandings. For instance, a 10 million Rand fine may be trivial for one organisation but significant for another, highlighting the importance of context in determining risk appetite. It's crucial for Information Security and privacy officers to communicate with senior management in terms that resonate with other departments, particularly when demonstrating how risks, including reputational risks, intersect. Engaging all relevant stakeholders fosters a common Risk Management Language, enabling informed decision-making on investments in security controls and compliance efforts.
Figure 23 The Role of ANNEX A in the ISMS Process
Figure 24 The ISMS Process Supports Privacy Compliance
ISMS Process and Compliance in Cybersecurity
The ISMS process supports compliance with ISO 27001 by implementing, managing, auditing, reviewing, and assessing the effectiveness of controls, which includes conducting vulnerability and penetration tests. It's important to consider the integration of policy and process levels, particularly in documenting roles and responsibilities, as these affect resource competency and budgeting during the planning stage. A discussion among the attendees and Caroline highlights the necessity for leadership to design management strategies that align policies with operational needs, and this insight is particularly relevant for those responsible for evaluating security measures.
Figure 25 Closing Slide
ISO Standards and Risk Management in Companies
Caroline emphasises the importance of a company's maturity stages in meeting ISO standards, particularly ISO 27000, which focuses on capabilities like access management. While maturity indicates how effectively a company manages these capabilities, the standards do not mandate automation or a formalised system. It's crucial, however, to maintain evidence of due diligence—such as meeting minutes—to demonstrate that discussions and considerations about security risks were conducted. Ultimately, organisations should take a defensible position in their compliance efforts, ensuring that their risk management decisions can be justified based on available resources and risk handling effectiveness.
In a legal context, organisations must establish defensible positions by adhering to recognised protocols and frameworks, such as the Secure Controls Framework, which assists in risk ranking and prioritising necessary security controls. These guidelines emphasise that lacking minimum controls can be considered negligent.
Organisations should document their risk assessment and management processes clearly to justify their decisions in a court of law, ensuring they can defend their strategies over time. Additionally, considerations around litigation risks have prompted the development of an insurance market, raising the question of whether enterprises in South Africa can obtain insurance to safeguard against potential legal challenges.
Cyber Insurance and Secure Controls Framework
The webinar closes with a discussion highlighting the importance of understanding cyber insurance and professional indemnity insurance, particularly the fine print within policies. It was noted that certain policies may exclude coverage for data breaches arising from criminal activity, which could leave businesses vulnerable, as most security events involve some form of criminality.
Caroline touches upon the Secure Controls Framework (SCF), which consolidates various standards and offers a maturity rating for security controls, providing a clearer understanding of what measures to implement based on maturity levels. This tool aids organisations in determining investment decisions and whether to automate processes or rely on manual monitoring. Overall, awareness of insurance limitations and available frameworks is crucial for effective risk management in cybersecurity.
If you would like to join the discussion, please visit our community platform, the Data Professional Expedition.
Additionally, if you would like to be a guest speaker on a future webinar, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!